Zero Day Vulnerability in Google Chrome : In order to prevent cyberattacks, users are advised to update their browser right away.
Chrome in there official blog channel said “With great pleasure, the Chrome team announces that Chrome 128 has been promoted to the stable channel for Linux, Mac, and Windows. This will be implemented over the next few days or weeks.
Among the corrections and enhancements in Chrome 128.0.6613.84 (Linux) 128.0.6613.84/.85 (Windows, Mac) are several.”
Reporting That “[$11000][356196918] High CVE-2024-7965: Inappropriate implementation in V8. Reported by TheDog on 2024-07-30“
Detail of CVE-2024-7965
Before 128.0.6613.84, Google Chrome’s improper implementation in version 8 would have given rise to a remote attacker’s possibility to use a manipulated HTML page to take advantage of heap corruption. (High level of security for chromium)
What is Heap Corruption ?
A software problem known as a heap corruption vulnerability arises when a program’s memory allocation and deallocation algorithms do not handle memory correctly. This may occur when a software writes data to a memory location that is either unallocated or used for a different reason.
Result: The software could crash, give invalid results, or allow hackers to use it to obtain unauthorised access.
As part of the 2024 competition, Google has announced the introduction of an update that addresses the tenth zero-day vulnerability that malicious or white hat hackers are actively exploiting.
A bug in the Google Chrome browser’s implementation of the V8 JavaScript engine is identified as CVE-2024-7965 (CVSS score: 8.8). Due to the vulnerability, a remote attacker may be able to execute malicious code on the target device by using a properly constructed HTML page to induce heap corruption.
Pwn2Own: Eight 0 Days Chrome V8 JavaScript engine
- Using a specially constructed HTML page, remote attackers can take advantage of heap corruption through a high-severity out-of-bounds memory access vulnerability in the Chrome V8 JavaScript engine, CVE-2024-0519, which could grant them access to confidential data without authorisation.
- CVE-2024-2887: WebAssembly (Wasm) standard has a high-severity type confusion flaw. By using a manipulated HTML page, it might result in remote code execution (RCE) attacks.
- The WebCodecs API, which is used by online applications to encode and decode audio and video, has a use-after-free vulnerability known as CVE-2024-2886. The vulnerability allowed for remote code execution by allowing unauthorised readers and writers to access prepared HTML pages.
- A high-severity vulnerability in the Chrome V8 JavaScript engine that results from an out-of-bounds read is known as CVE-2024-3159. By creating carefully designed HTML pages, remote attackers were able to take advantage of this vulnerability and access data that was not in the memory buffer allotted. This led to heap corruption, which could be used to extract confidential data.
- A high-severity use-after-free vulnerability in the Visuals component, which manages the rendering and browser-based content display, is identified as CVE-2024-4671.
- CVE-2024-4761: An out-of-bounds write issue in the JavaScript engine in Chrome V8, which powers the application’s JS code execution.
- The Chrome V8 JavaScript engine has a type misunderstanding vulnerability (CVE-2024-4947) that allows arbitrary code execution on the victim device.
- V8 JavaScript engine in Chrome has a type misunderstanding vulnerability (CVE-2024-5274) that can cause crashes, corrupt data, or arbitrary code execution.


Google has fixed eight additional zero-days since the beginning of the year that were identified as being used in attacks or during the Pwn2Own hacking competition:
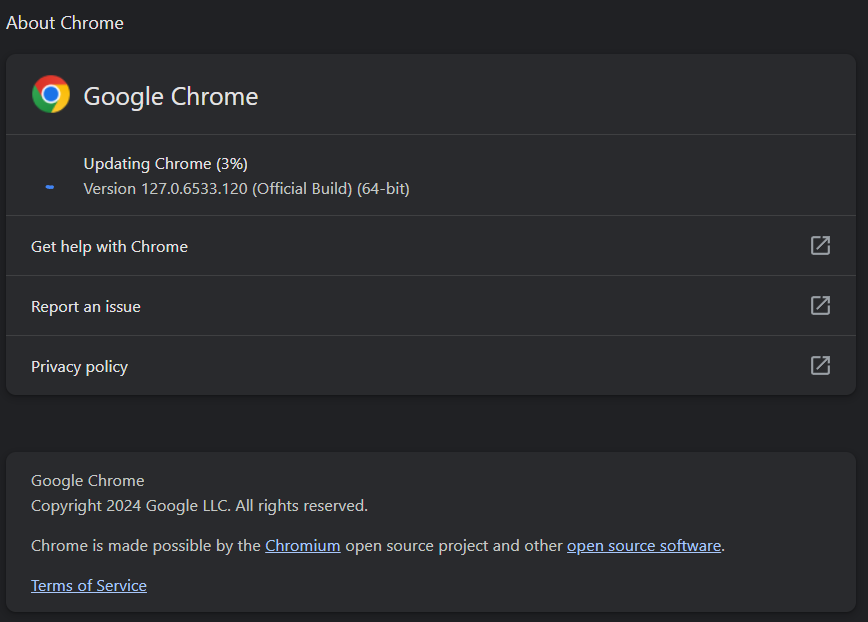
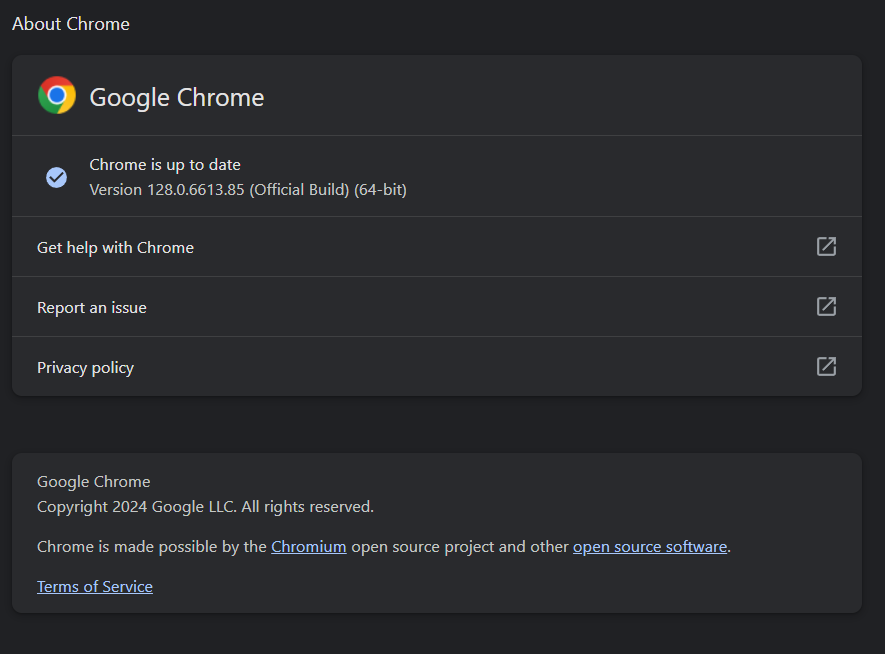
Updating Chrome
When security patches become available, Chrome will update automatically. However, if you want to speed up the process, you can manually apply the updates by navigating to Chrome menu > Help > About Google Chrome, waiting for the update to finish, and then clicking the ‘Relaunch’ button to install it.
“Access to bug details and links may be kept restricted until a majority of users are updated with a fix,”
“We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed.”
Although Google confirmed the existence of the vulnerabilities CVE-2024-7971 and CVE-2024-7965, it has not yet disclosed more information regarding the types of attacks that have exploited these vulnerabilities.


