Introduction
In this beginner-friendly guide, we’ll walk through the process of creating a Banner Grabbing Script with Python3 for pentesting purposes. Banner grabbing is a common technique used in cybersecurity to gather information about a target system, such as its operating system, services running, and software versions.

Setting up Environment
So inorder to run python go to the official website python.org and download the latest version install the setup add the necessary bin folder to enviroment variable and then install VSCode. Now Install the CodeRunner Plugin in VSCode and also install the python plugin on VSCode and that is it you are ready to Code.
Banner Grabbing Script with Python3
Now let’s dive into writing the Python script for banner grabbing. We’ll start by importing the necessary library and defining our main logic.
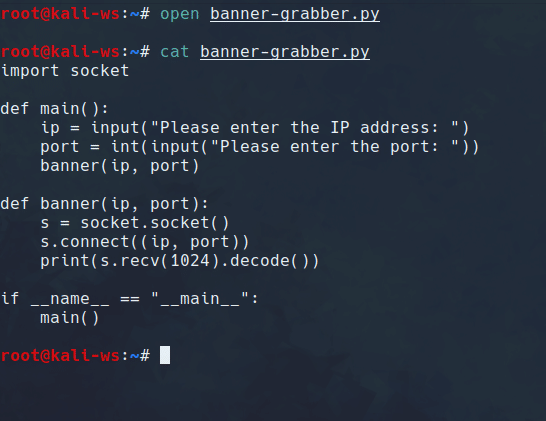
import socket
def main():
ip = input("Please enter the IP address: ")
port = int(input("Please enter the port: "))
banner(ip, port)
def banner(ip, port):
s = socket.socket()
s.connect((ip, port))
print(s.recv(1024).decode())
if __name__ == "__main__":
main()
Banner Grabbing Script with Python3
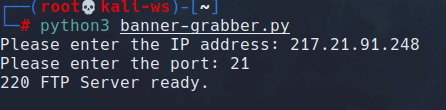
Explanation
- We import the (socket) library, which allows us to work with sockets in Python.
- The main() function prompts the user to enter the IP address and port.
- The banner() function establishes a connection to the specified IP and port, retrieves the banner, and prints it.
Improving the Script
To make our script more robust and user-friendly, we can implement exception handling and refine the banner display.
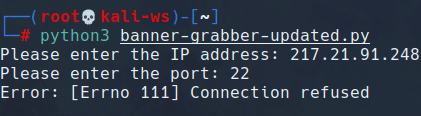
import socket
def main():
try:
ip = input("Please enter the IP address: ")
port = int(input("Please enter the port: "))
banner(ip, port)
except Exception as e:
print("Error:", e)
def banner(ip, port):
try:
s = socket.socket()
s.connect((ip, port))
print("Banner from", ip, ":", port)
print(s.recv(1024).decode().strip())
s.close()
except Exception as e:
print("Error:", e)
if __name__ == "__main__":
main()
Banner Grabbing Script with Python3
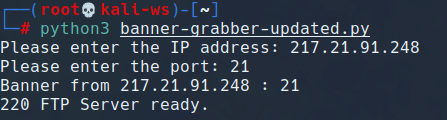
Explanation
- We use
try-exceptblocks to catch and handle any exceptions that may occur during execution. - The
strip()method removes leading and trailing whitespace from the banner for cleaner output.
Frequently Asked Questions
- What is a banner-grabber?
A banner-grabber is a tool that can be used to capture information about a remote server’s operating system, software, and version information by analyzing the response headers from a server. - How can I use a Banner Grabbing Script with Python3 ?
You can use the python script to send a request to a server and read the response headers to gather information about the server’s software and version. - Is it legal to use a banner-grabber on a server without permission?
It is always best to obtain permission from the server owner before using a banner-grabber tool, as unauthorized access or use of such tools may be illegal. - What can I learn from a banner-grabber?
You can learn valuable information about the server, such as the operating system, software running on the server, and potentially any known vulnerabilities associated with them. - Are there any risks associated with using a banner-grabber?
There are potential risks associated with using banner-grabber tools, such as accidentally triggering security alerts or firewall rules on the server. - Can a banner-grabber be used to hack into servers?
While banner-grabber tools themselves are not typically used for hacking, the information gathered from them can be useful for potential attackers to identify vulnerable servers. - How accurate is the information gathered by a banner-grabber?
The information gathered by a banner-grabber tool is only as accurate as the response headers provided by the server, so it may not always be 100% reliable. - Are there any alternatives to using a banner-grabber tool?
There are other methods to gather information about a server, such as using scanning tools like Nmap or in-depth manual analysis of the server’s response headers. - Can a banner-grabber be used for legitimate purposes?
Yes, banner-grabber tools can be used by cybersecurity professionals for legitimate purposes, such as auditing server configurations and identifying potential security vulnerabilities. - How can I protect my server from banner-grabbers?
You can protect your server from banner-grabber tools by regularly updating software, applying security patches, and monitoring server logs for any suspicious activity.
Conclusion
In this tutorial, we’ve learned how to create a simple banner grabbing script using Python3. By understanding the basics of socket programming and implementing error handling, you’re now equipped to explore further in the field of pentesting and cybersecurity.Also checkout other interesting blogs on hackingblogs.com
Happy hacking!


