Attention! The source @vxdb from which this news originated has withdrawn its comment and expressed apology. The person tweeted “I misspoke in this tweet. I was unaware of the naming arrangement between Raymond Hill and the team at ‘Adblock‘. I was under the impression that this was trying to leech off of the uBlock Origin name. I was incorrect. My apologies.“
An Important Message : Numerous extensions for the Chrome browser exist that mimic the genuine article. Users should make sure they are installing the legitimate extension and not a phoney one.
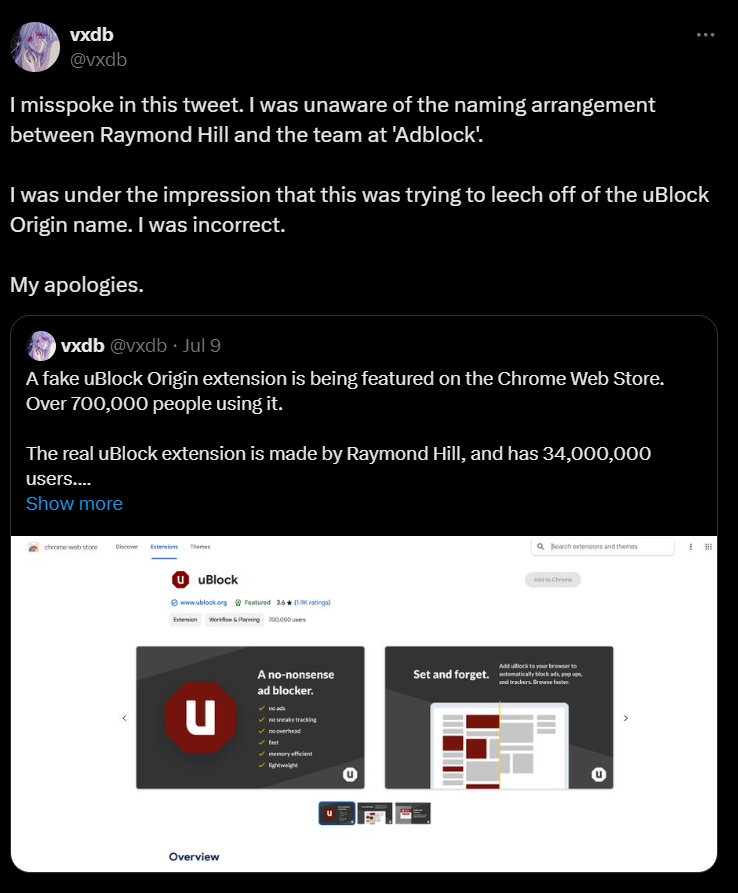
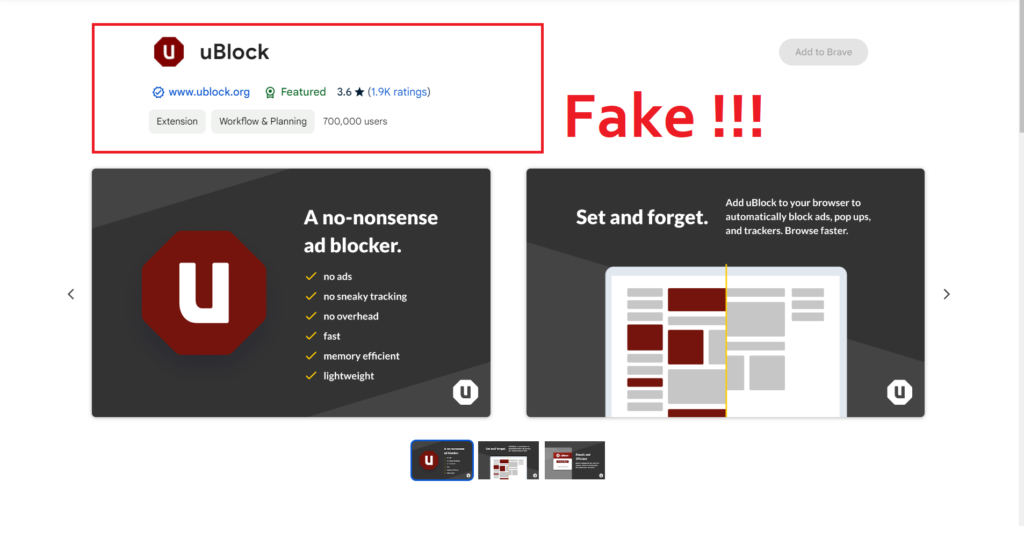
Hackingblogs: On the Chrome Web Store, there is a fraud version of the uBlock Origin extension. More than 700,000 users are on it.
Raymond Hill created the original uBlock extension, which is used by 34,000,000 people.
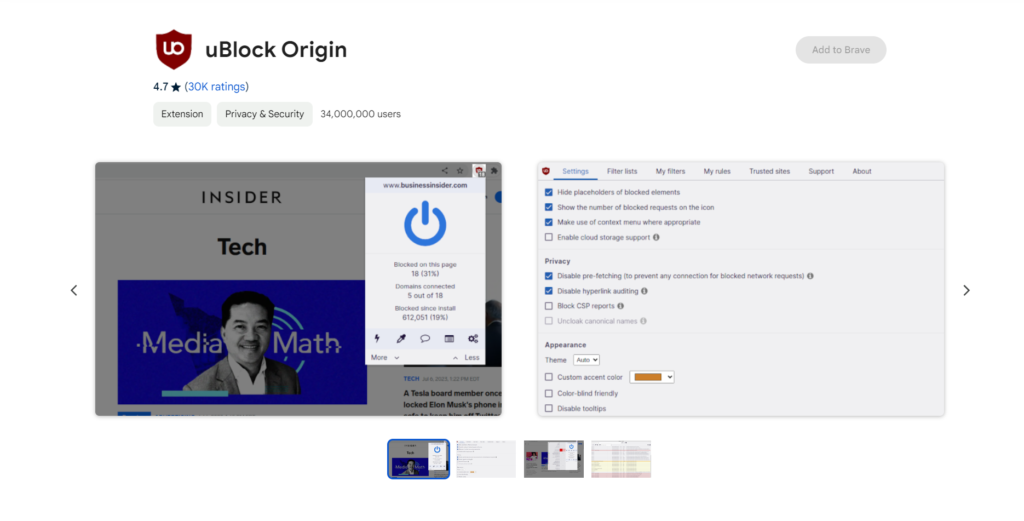
Ublock Origin Vs Ublock(Fake)
Installing an ad blocking extension to improve one’s web browsing experience may not be the best idea for users, as recent research from AdGuard has shown that many well-known ad blockers are not only fraudulent but also harmful.
Following a comprehensive examination of the ad blockers on the Chrome Web Store, the company discovered that Ublock by Charlie Lee had tricked people into downloading it by posing as uBlock Origin, a well-known ad blocker.
Since the add-on is based on the coding of the original “ublock” extension, at first it worked as intended, removing advertisements from websites.
It was subsequently found that these extensions started submitting a request to urldata.net for every new domain they visited, having been used for almost 55 hours. This made it possible for the extensions to get affiliate links from the websites that users visited; if they bought anything while on those websites, the owner of the extensions would get paid a percentage. This Is Cookie Stuffing.
What is Cookie Stuffing ?
A dishonest affiliate marketing tactic known as “cookie stuffing” involves installing cookies on a user’s computer without that user’s knowledge or consent.
Cookie stuffing is a technique employed by false ad blockers that is essentially an ad fraud scam. The makers of these fake extensions are not only fooling users into downloading them by acting as more well-known ad blockers, but they are also earning off their browsing patterns and online transactions.
Reddit User’s On this matter
Many individuals have been duped by a complete imitation of uBlock Origin that is available in the Chrome Webstore. My inexperienced eyes tell me that they uploaded your precise script along with a duplicate extension icon and more. Though I am not clear what their goals were, I hope they were limited to using the Google Store to make money rather than selling data or infecting computers.
They purchased and are currently using the uBlock.org domain, and their fictitious address points to an Atlanta law office.
There is only “uBlock Origin” in Firefox, there is no “uBlock“, so whatever you are using is certainly not “uBlock”.
Frequently Asked Question
- What is cookie stuffing used for in affiliate marketing?
- Cookie stuffing is used to fraudulently claim commissions by placing affiliate cookies on users’ browsers without their knowledge, attributing purchases to the stuffer.
- How does cookie stuffing work?
- Cookie stuffing involves surreptitiously dropping affiliate cookies onto visitors’ browsers, often through scripts or iframes, to claim commission on subsequent purchases.
- Why is cookie stuffing considered fraudulent?
- It deceives websites into thinking they’ve referred customers, earning undeserved commissions and distorting affiliate marketing metrics.
- What are common methods of cookie stuffing?
- Methods include using scripts, iframes, browser extensions, and plugins to covertly inject affiliate cookies into users’ browsers.
- Can cookie stuffing lead to legal consequences?
- Yes, in some jurisdictions like the USA, cookie stuffing has been prosecuted as wire fraud due to its deceptive nature.
- What industries are most affected by cookie stuffing?
- Industries relying heavily on affiliates such as iGaming, online trading, e-commerce, and travel are particularly vulnerable to cookie stuffing.
- How do legitimate affiliates and merchants suffer due to cookie stuffing?
- Legitimate affiliates lose revenue, and merchants receive inaccurate performance data, potentially affecting their marketing strategies.
- How can merchants detect and prevent cookie stuffing?
- Techniques like traffic monitoring, device fingerprinting, and behavior analysis can help identify suspicious affiliate activities.
- What happened in the eBay cookie stuffing case?
- Two affiliates were convicted of wire fraud for using cookie stuffing to earn millions in undeserved commissions from eBay, despite not actively driving sales.
- What measures can companies take to combat cookie stuffing?
- Implementing comprehensive anti-fraud platforms, monitoring affiliate conversion rates closely, and fostering partnerships with reputable affiliates can mitigate cookie stuffing risks.


