HackingBlogs: The United States filed charges against four men in 2020 on the grounds that they had constructed a resilient hosting empire that had formerly controlled the Russian cybercrime market and financed numerous organised crime groups. Talks on Spamdot
On accusations of conspiracy and racketeering, all four entered guilty pleas. However, the two Russian men involved have an intriguing and little-known past. They co-ran the most popular spam forum in the world and collaborated with some of the most dangerous cybercriminals in Russia.

Two main administrators ran the cybercrime forum Spamdot (also known as Spamit) from January 2005 to April 2013. It was an invite-only community for Russian-speaking individuals involved in the spam sending and botnet building industries. The usernames of the Spamdot administrators were Salomon (also known as Sal) and Icamis (also known as Ika).
What is Spamdot ?
Spamdot was home to fraudsters running some of the most nasty botnets in the world, worldwide malware contagions known by strange names like Rustock, Cutwail, Mega-D, Festi, Waledac, and Grum, as I described in my 2014 book, Spam Nation.
Icamis and Sal communicated with these botmasters on a daily basis through private messages and the Spamdot forum. Together, those botmasters were in charge of millions of spam-spewing zombies that were also continuously gathering passwords and other information from compromised computers.
Salomon is currently in jail, as we will see in a moment, in part because he assisted in robbing numerous small American businesses using some of those identical passwords that were obtained. He is presently serving the last few months of a 60-month sentence in a federal prison located in Michigan.
Threat actor Synopsis
Revealing Rescator’s true identity
In April 2013, Icamis revealed Rescator’s true name in a long farewell letter to Spamdot users, announcing his decision to shut down the forum and completely leave the cybercrime industry.
To no one’s surprise, Icamis continued in the industry; he just changed the way he talked about it, becoming more reserved and centred on aiding criminal organisations in their efforts to embezzle money from American bank accounts. However, the Rescator story served as a stark reminder that ten years of inquiry into the real-life identity of Ika/Icamis had been entirely neglected. This is an attempt to correct that oversight.
Understanding Salomon identity
Salomon used the email address ad1@safe-mail.net and the password 19871987gr in order to sign up as a Spamdot associate. Constella Intelligence, a breach tracking service, discovered that the email address grichishkin@gmail.com was using the password 19871987gr. That email address, Alexander Valerievich Grichishkin, from Cherepovets, is linked to several accounts.
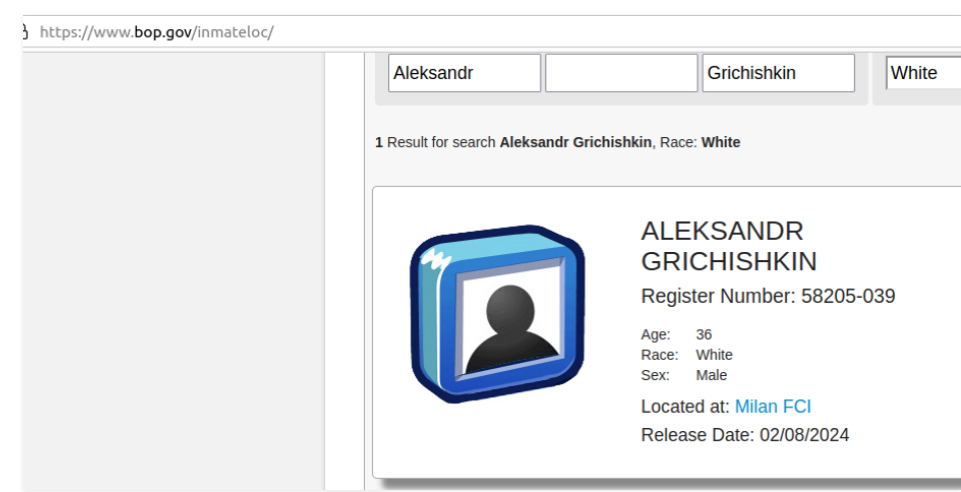
Grichishkin was detained outside of Russia in 2020 after being ordered to stop offering bulletproof hosting to groups of cybercriminals. According to the U.S. government, Grichishkin and three other people put up the infrastructure that cybercriminals exploited from 2009 to 2015 to spread malware and target victims and financial institutions across the country.
Among those clients were criminals who created botnets and stole bank passwords using malware such as Zeus, SpyEye, Citadel, and the Blackhole exploit kit.
ICAMIS Identity discovery
Icamis’s identity became clear when KrebsOnSecurity started looking for hints that could link him to Cherepovets, which is apparently Ika’s hometown based on the IP addresses he frequently used to access Spamdot.
Many of the email addresses and domains associated with Icamis, such as icamis[.]ws, icamis[.]ru, and icamis[.]biz, invoke the name “Andrew Artz,” according to historical domain ownership records obtained from DomainTools.com. In 2003, Icamis used the email address icamis@4host.info to advertise his services, including bulk-domains[.]info. From a 2005 advertisement he ran
What is Spammit
Spamit, a highly guarded affiliate programme, has announced that it will shut down at the end of September. For years, it has paid some of the greatest spammers in the world to promote websites for counterfeit pharmacies.
Spamit administrators attributed the upcoming shutdown to heightened awareness of their programme, which engaged affiliates through a number of websites using the spamit name, such as spamit.com, spamit.biz, and spamdot.biz.
The most well-known use of spammer affiliates is to advertise the widely used “Canadian Pharmacy” websites, such zithmed.com, which is shown on the left. Although thousands of these fly-by-night Canadian pharmacy websites are available online at any given time, offering prescription drugs without a prescription, experts claim that the majority of the drugs sent to customers are manufactured in and shipped from China or India. These pharmacies are about as Canadian as caviar.


