What is Styx Stealer ?
A new piece of malware called Styx Stealer can steal cryptocurrency, instant messaging sessions from Telegram and Discord, and browser data. Despite its new appearance, it has already been observed in attacks.
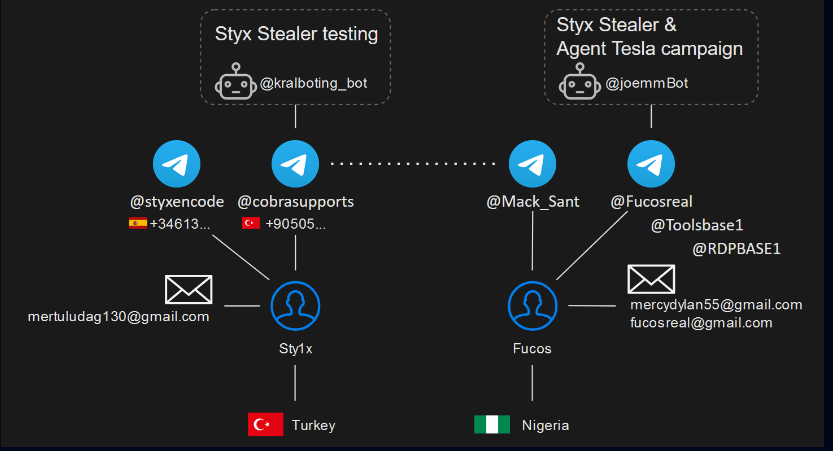
It was discovered that the creator of Styx Stealer was connected to Agent Tesla threat actor Fucosreal, who was engaged in a spam operation that also targeted research-checkpoint clients.
How did the attacker expose himself ?
Due to the developer’s critical mistake, a significant amount of private data was obtained by CPR. This information included the number of clients, profit details, nicknames, phone numbers, email addresses, and similar details about the actor behind the Agent Tesla campaign.
Indepth look on Styx Stealer
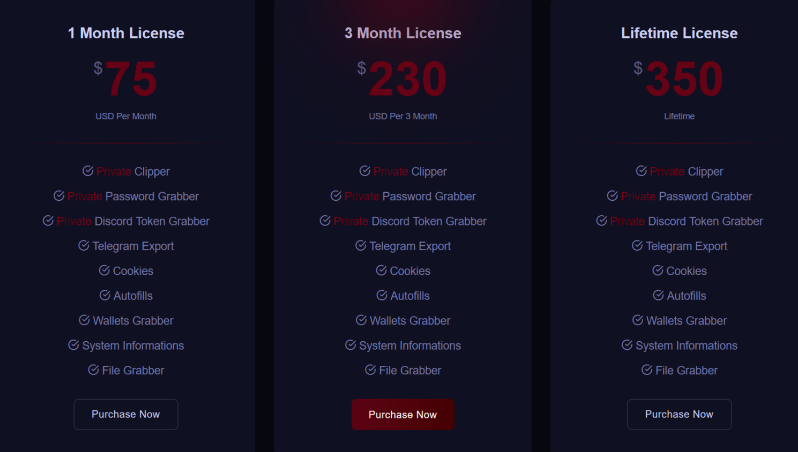
Strong malware called Styx Stealer can take use of users’ saved passwords, cookies, and auto-fill information from a variety of browsers running Gecko and Chromium as well as information from browser extensions, cryptocurrency wallets, Telegram and Discord sessions, and browser extensions.
Before the malware is launched, it also collects system data, such as hardware specifications and the external IP address. It can also snap images to get a better idea of the surroundings. These fundamental duties are all carried over from Phemedrone Stealer.
The developer of Styx Stealer included a few more features, including auto-start, data transfer to Telegram re-implemented, further sandbox evasion and anti-analysis techniques, and clipboard monitor and crypto-clipper.
Styx Youtube Demonstration
Previously available on the Styx YouTube channe Styx the demonstration of Styx Stealer and Styx Crypter is not available at this time. Notably, Styx Crypter is promoted as a reliable tool for software protection, just as other crypters.
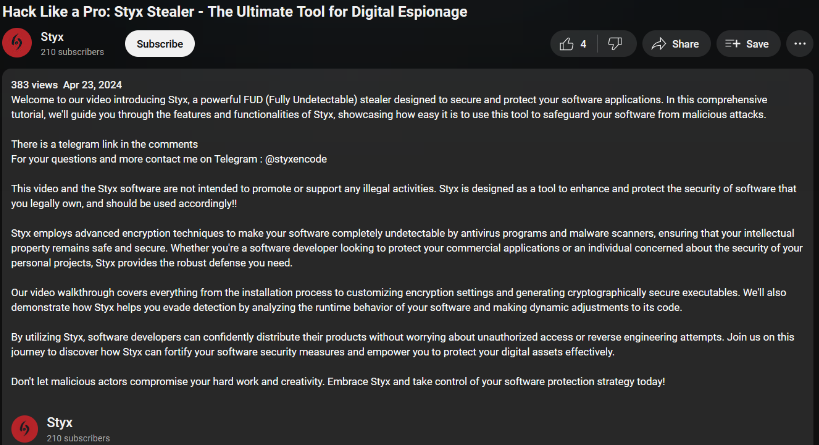
The Styx Crypter description is largely repeated in the YouTube description of Styx Stealer.
“The Ultimate Tool for Digital Espionage… designed to secure and protect your software applications.”
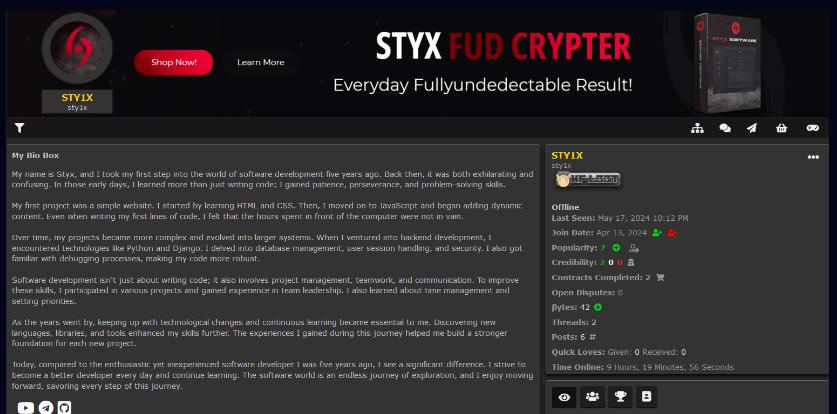
Although April 26, 2024, is when the domain styxcrypter[.]com was registered, sales started a little sooner. On April 23, the Styx YouTube channel released the first video featuring Styx Stealer; on April 13, the STY1X account on Hackforums was created, promoting Styx Crypter.
Agent Tesla stole data for this campaign by using the Telegram Bot API. The Telegram Bot token was successfully extracted from the malware settings by Checkpoint Research Team.
The creator of this bot, @joemmBot, is @Fucosreal, and its identification is “6649460096“:
They noticed a document that did not fit the standard Agent Tesla report structure when they were keeping an eye on the bot activities. It was discovered that this document was an archive with a header that said “Styx Stealer” and was constructed similarly to Phemedrone Stealer:
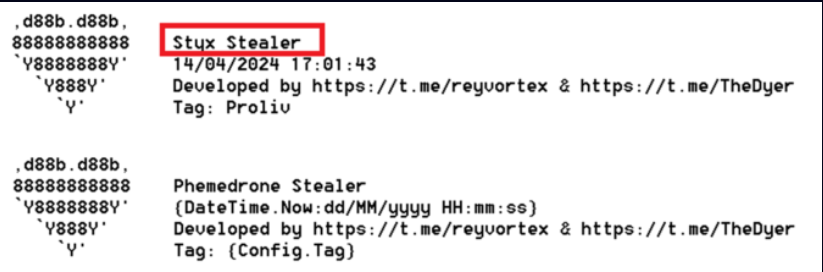
Finding the threat actor
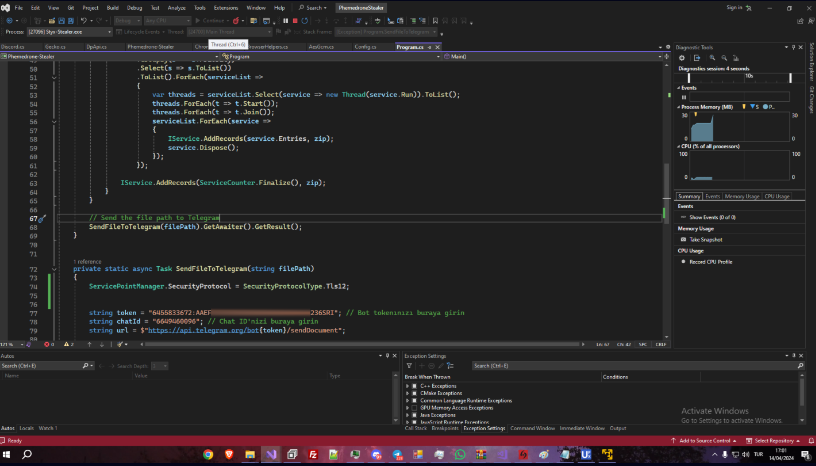
A screenshot of the Visual Studio IDE with a project called “PhemedroneStealer” while debugging the “Styx-Stealer.exe” process was also found in the captured archive. A hard-coded Telegram Bot token and conversation ID that matched perfectly with those taken from the Agent Tesla sample we previously examined were found in the project’s Program.cs file.
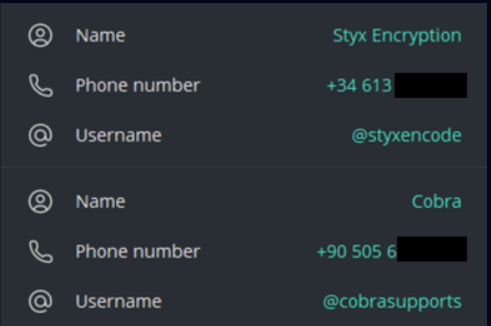
From the archive, researchers were able to recover encrypted user data for the @styxencode and @cobrasupports Telegram accounts.
It is interesting to note that the phone number linked to the @styxencode account has Spain’s country code (+34). It’s possible that this might be a temporary number that was bought just to use one of the many specialised providers to register the Telegram account. The second phone number, (+90 505 6), is associated with a Turkish operator and might be the creator of Styx Stealer’s personal number.
The only chat that the @kralboting_bot generated was with the user @cobrasupports. In that discussion, Styx Stealer reports from his computer were included, albeit with a previous timestamp.
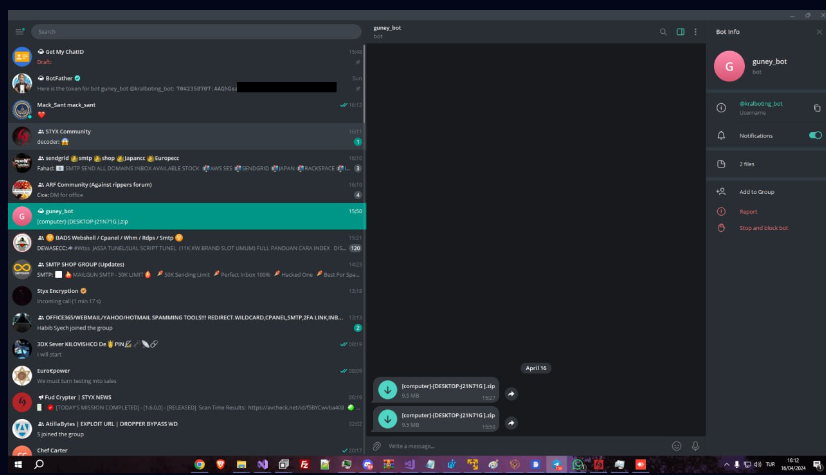
During debugging, Sty1x first implemented the ability to transfer data over Telegram and tested it on his own bot. Additionally, he convinced @Mack_Sant to use the identical stealer build on his machine. Then, Sty1x put the token that @Mack_Sant had sent him from the @joemmBot inside the stealer.
By the way, @Mack_Sant also gave Sty1x a picture of his laptop and smartphone displaying the conversation with this bot that included reports from Styx Stealer. Additionally, a screenshot of Agent Tesla reports is shown to us, which amply supports our belief that the owner of this bot and the creator of the Agent Tesla campaign is @Mack_Sant, also referred to as @Fucosreal:
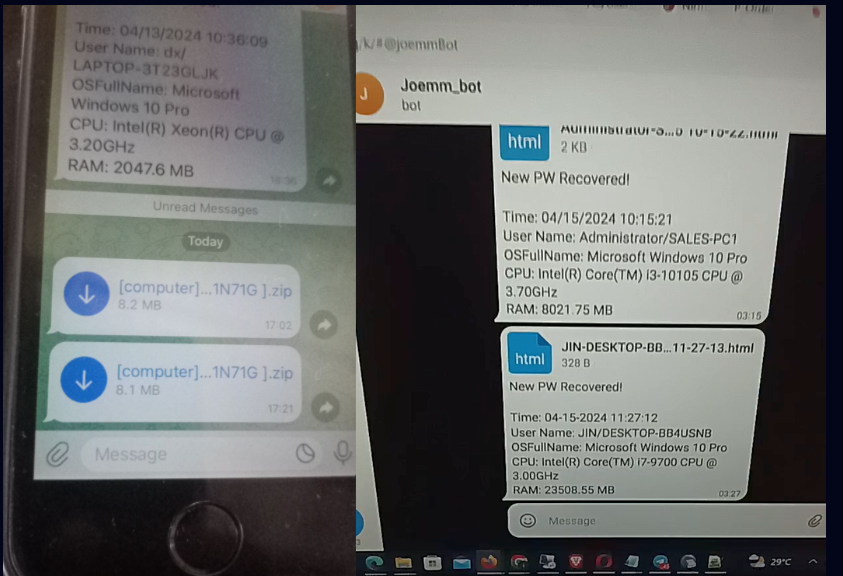
And it is possible that Styx Stealer will reappear with enhanced features or new targeted techniques. Users may keep up to date and safeguard their important online data by installing strong security measures and keeping up with the current dangers.


