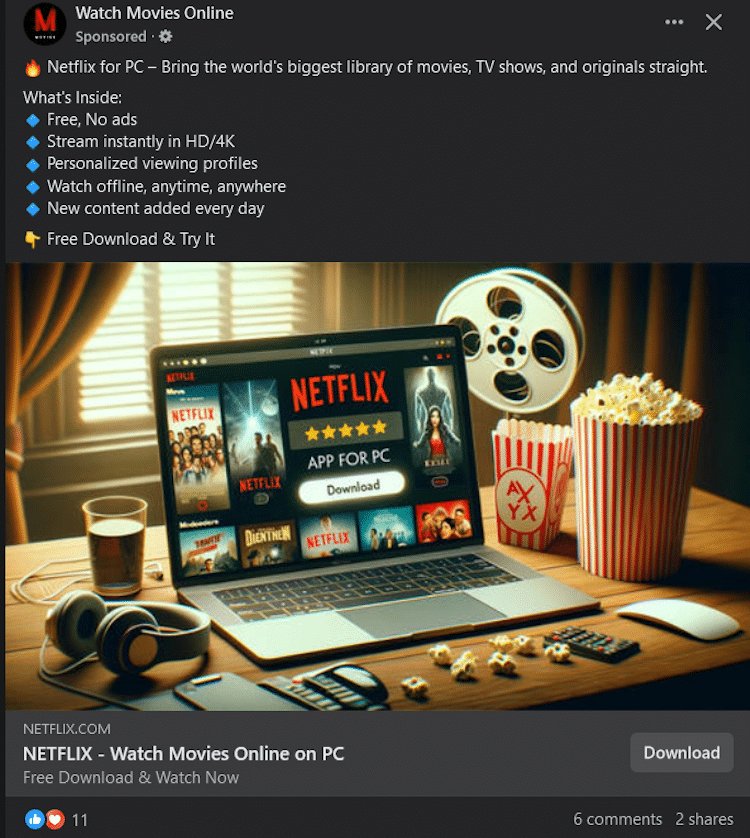
Ads campaign by cybercriminals is aimed at Facebook users. According to Bitdefender, they are using Meta’s advertising to copy trustworthy businesses to spread the SYS01 infostealer virus, which has the ability to take over accounts and personal data. Bitdefender Labs found a persistent assault that massively impersonates well-known brands like Netflix, Office 365, CapCut, and others.
“The malvertising campaign that has been wreaking havoc on Meta platforms for at least a month is continuously evolving, with new ads appearing daily,”
What Is This Malware Campaign About ?
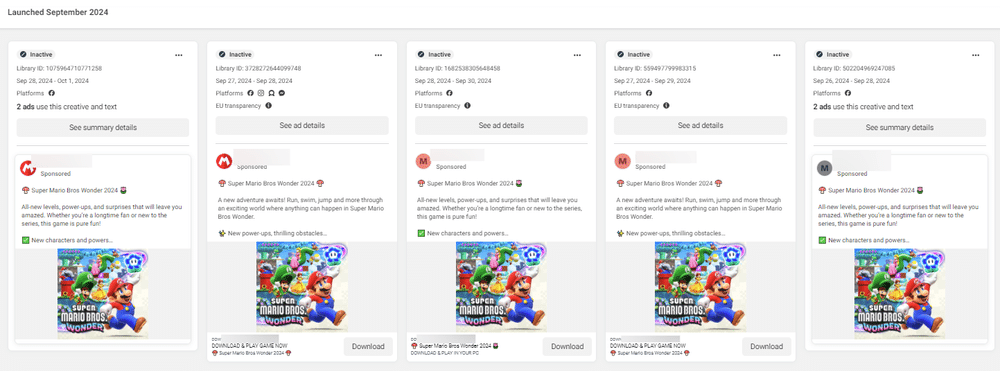
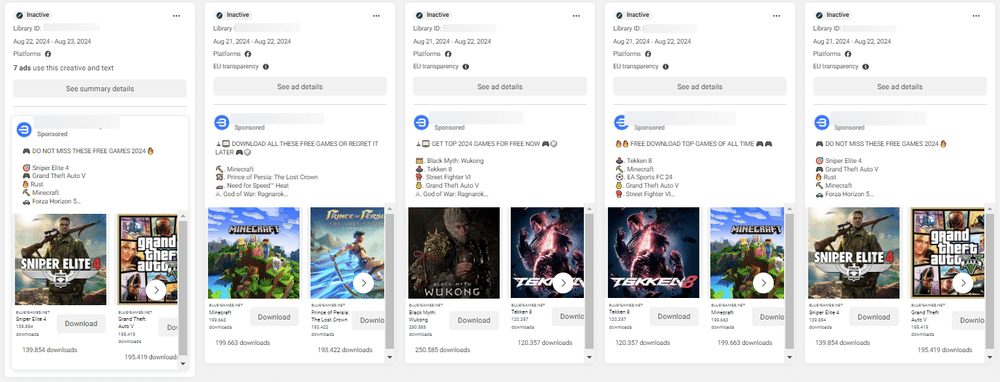
The campaign that began in September stood out due to the malicious samples that were distributed. The threat actors’ general mimicry approach, which was employed by the cybercriminals, allowed them to impersonate a wide range of software tools related to productivity, video or photo editing (Capcut, Canva, Adobe Photoshop), virtual private networks (Express VPN, VPN Plus), movie streaming services like Netflix, instant messaging apps like Telegram, and even video games. Malware distributed through social media ads is not a new development in criminal cyberspace.

These advertisements, which mostly target older males, typically run for weeks. According to Bitdefender, they were using two strategies by providing infected samples directly. Reusing malicious domains that mimicked a generic video game download platform was the second strategy.
Compromise Indicators
Malware Hosting Domains
hxxps://krouki.com
hxxps://kimiclass.com
hxxps://goodsuccessmedia.com
hxxps://wegoodmedia.com
hxxps://socialworldmedia.com
hxxps://superpackmedia.com
hxxps://wegoodmedia.com
hxxps://eviralmedia.com
hxxps://gerymedia.com
hxxps://wakomedia.comC2 Domains
hxxps://musament.top
hxxps://enorgutic.top
hxxps://untratem.top
hxxps://matcrogir.top
hxxps://ubrosive.top
hxxps://wrust.top
hxxps://lucielarouche.com
hxxps://ostimatu.topHow are they distributing the software ?
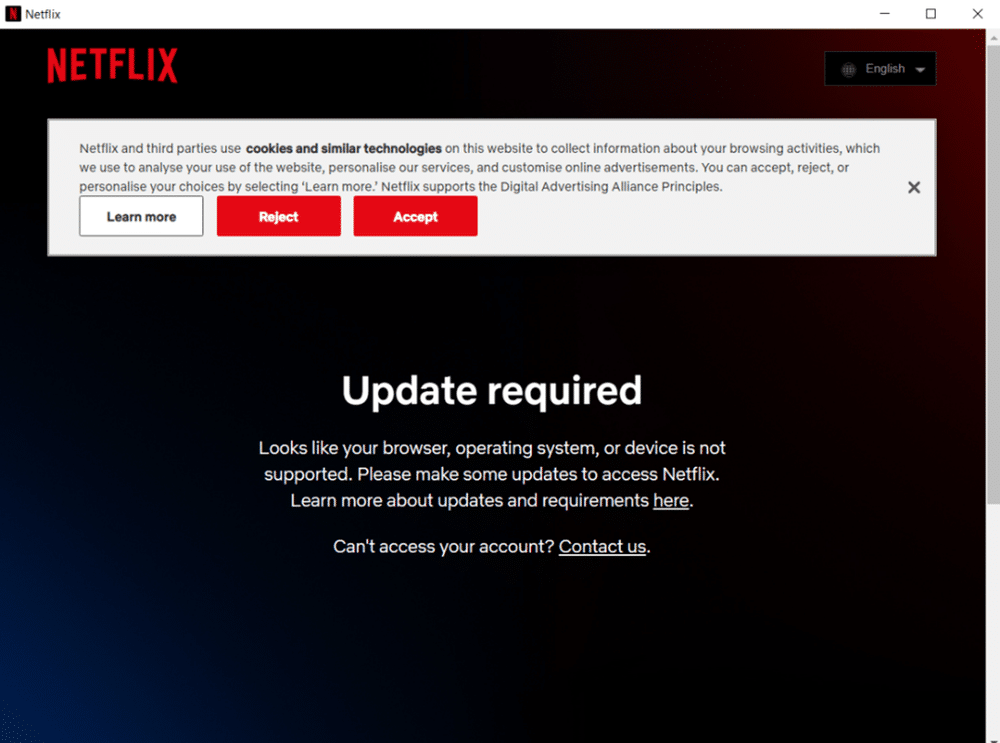
Usually, the advertisements refer to a link that permits the direct download of dangerous software or point to a MediaFire link.

The examples are available as a.zip file that includes an Electron application. Depending on the sample, the extracted archive’s format may vary, but the infection technique is always the same: malicious software will be dropped and executed by the Javascript code that was placed in the
It is difficult for the victim to recognise that they have been compromised because the malware operates in the background while a decoy app, which frequently imitates the ad-promoted software, seems to be operating correctly.
SYS01 Infostealer
Harvesting Facebook credentials, particularly Facebook Business accounts, is one of SYS01InfoStealer’s main objectives. After gaining access to these accounts, hackers use the compromised accounts to distribute more harmful advertisements in addition to taking use of the personal information.
It seems that gathering information about Facebook profiles, particularly corporate sites, is the aim of the SYS01 infostealer. The malware has the ability to get fresh instructions from the command and control servers in real time and update them dynamically. The victims’ information may be sold on the dark web or utilised for other illegal purposes.


