Corporate networks are being initially accessed through the exploitation of CVE-2024-38094. As part of the July Patch Tuesday package, Microsoft discovered a Microsoft SharePoint remote code execution (RCE) vulnerability and classified it as “high-severity“. Rapid7 finds that attackers planted a webshell on a vulnerable SharePoint server by gaining unauthorised access through CVE-2024-38094.
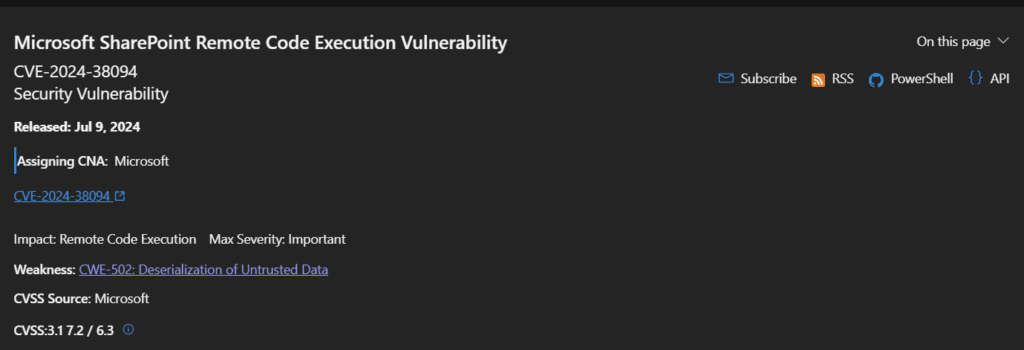
A Look On CVE-2024-38094 : Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft SharePoint, a popular web-based platform that serves as an intranet, document management, and collaboration tool and can easily interface with Microsoft 365 apps, is affected by the high-severity (CVSS v3.1 score: 7.2) RCE vulnerability CVE-2024-38094.
“An authenticated attacker with Site Owner permissions can use the vulnerability to inject arbitrary code and execute this code in the context of SharePoint Server,”
CISA did not disclose how the vulnerability was used in attacks when it added CVE-2024-38094 to the Known Exploited Vulnerability Catalogue last week.
Rapid7 : Investigation
“Our investigation uncovered an attacker who accessed a server without authorization and moved laterally across the network, compromising the entire domain,”
Team Rapid7
According to them, during their investigation, they discovered an attacker who gained unauthorised access to a server and then proceeded horizontally throughout the network, compromising the entire domain. For two weeks, the attacker went unnoticed. Rapid7 identified CVE 2024-38094, a vulnerability in the on-premise SharePoint server, as the first point of entry.
Rapid7 started looking into questionable activities involving the execution of processes connected to a Microsoft Exchange service account. The Horoung Antivirus (AV) programme, which was not permitted in the environment, was installed by the service account in this case. The attacker’s flexibility to pursue follow-on goals was made possible by overriding the system’s existing security measures, which links this malicious conduct to Impairing Defences (T1562).
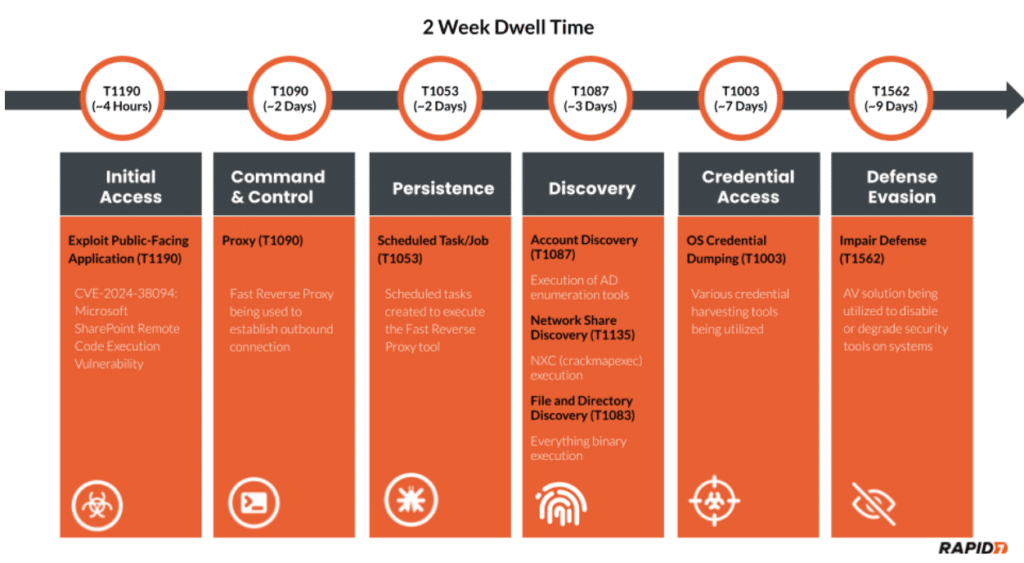
Evidence suggested that more than one system was involved in the malicious behaviour for this compromised Exchange service account. The domain controller was the source of the illegal behaviour a week earlier.The domain controller analysis showed that the attacker authenticated via Remote Desktop Protocol (RDP) using this Exchange service account.
The attacker then used the GUI to create an exclusion for a malicious binary called msvrp.exe and disable Windows Defender Threat Detection (WDTD) on the system. Although it had nothing to do with VMware, the malicious binary was located in the C:\ProgramData\VMware\ subdirectory.
Implication Of The Vulnerability : Initiation Of A WebShell
POST /_vti_bin/client.svc/web/GetFolderByServerRelativeUrl('/BusinessDataMetadataC atalog/')/Files/add(url='/BusinessDataMetadataCatalog/BDCMetadata.bdcm
POST /_vti_bin/DelveApi.ashx/config/ghostfile93.aspx Remote code execution (RCE) from an external source is possible on Microsoft SharePoint-running computers due to this vulnerability. The attacker used this vulnerability to drop a webshell onto the system Ghostfile93.aspx was the name of the webshell that produced multiple HTTP POST requests from the same external IP address associated with the exploit string in the log data. The attacker used the webshell for hours before utilising the local administrator account to log in to the system.
Proof Of Concept
The PoC Is Available on the telegram group Hackingblogsgroup


