As this crash course is coming close to an end , we will be going into more complex subjects, which is in fact different from the typical bug bounty teaching. Hackingblogs.com is what you are reading, and I am Dipanshu Kumar, your professor. Now let us begin!
Our focus today will continue where we left off yesterday. In addition to examining some well-known CMS platforms, such as WordPress, Joomla, Wix, and Drupal, we took a look at what CMS is. We also talked about how to use tools at the industry level to take advantage of them. We will explore additional methods of attacking CMS platforms in greater detail today. After we finish this section, we will turn our attention to exploiting the OWASP Top 5 flaws.

There are hundreds of different CMSs so it wouldn’t be practical for me to mention every single one of them. The vast majority of sites are going to be running WordPress, Joomla, and Drupal but you still might run into other CMSs. If you come across a CMS you haven’t seen before the first step is to go to exploit db and see if it has any known CVEs:
What IS Exploit DB ? Aka Exploit Database


The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software, developed for use by penetration testers and vulnerability researchers. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and present them in a freely-available and easy-to-navigate database. The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away.
An essential tool for penetration testers, ethical hackers, and bug bounty hunters is the Exploit Database (Exploit-DB). It is an extensive collection of freely available exploits, vulnerability information, and security-related data that is mostly used for testing and taking advantage of known flaws in applications and systems.
Key Features Of Exploit-DB
| Feature | Description |
|---|
| Vulnerability Database | A vast collection of publicly available exploits and vulnerabilities, with details on affected systems and proof-of-concept (PoC) code. |
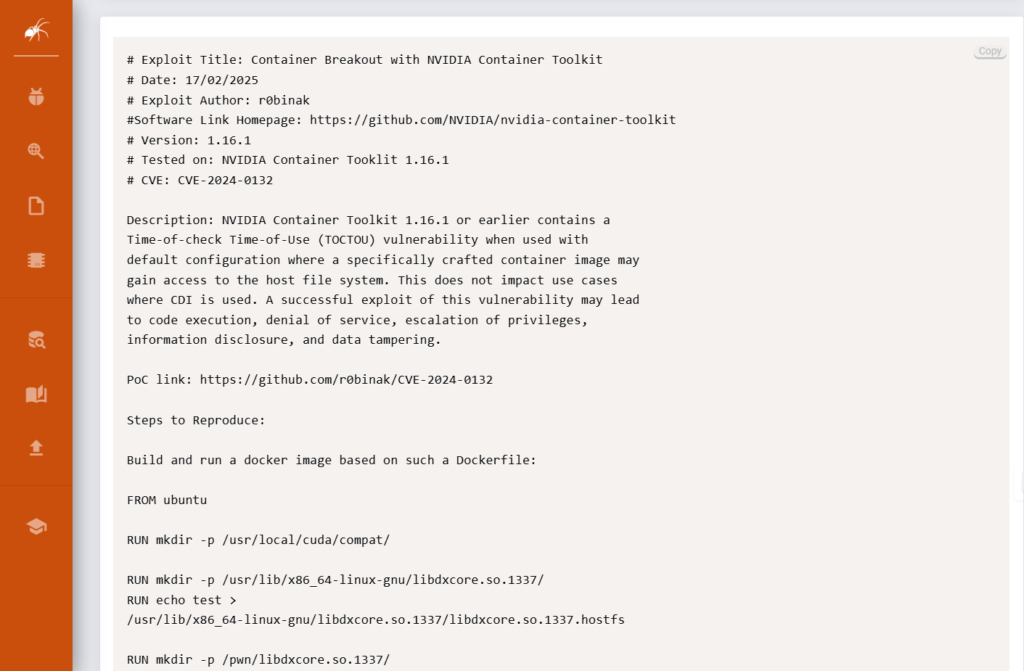
| Searchable Platform | Allows users to search exploits based on software version, CVE ID, vulnerability type, and more. |

| Proof of Concept (PoC) | Many entries come with PoC code or demonstration methods that show how to exploit specific vulnerabilities. |
| Publicly Available | Open-source and free to access, making it widely available for anyone interested in cybersecurity. |
| Exploit-Related Tools | Includes tools related to exploiting vulnerabilities, some of which automate the exploitation process or enhance specific types of attacks. |
| Comprehensive Information | Each entry includes detailed information on the vulnerability, affected software, CVE ID, severity, and sometimes exploit code. |
| Community Contributions | Open-source contributions from the community, continuously updating the database with new exploits and findings. |
Integrating Our CMS Exploitation Aim With Exploit DB
Checking for known vulnerabilities should be your first course of action when you come across a CMS that you are unfamiliar with. Exploit-DB, a comprehensive database that contains publicly available exploits and vulnerabilities, is an excellent place to start. This can give you information about possible flaws in the CMS you are using.
Here’s what you can do:
- Visit Exploit-DB:
I would look for something similar if I came across Magento as a target CMS:
Magento site:exploit-db.com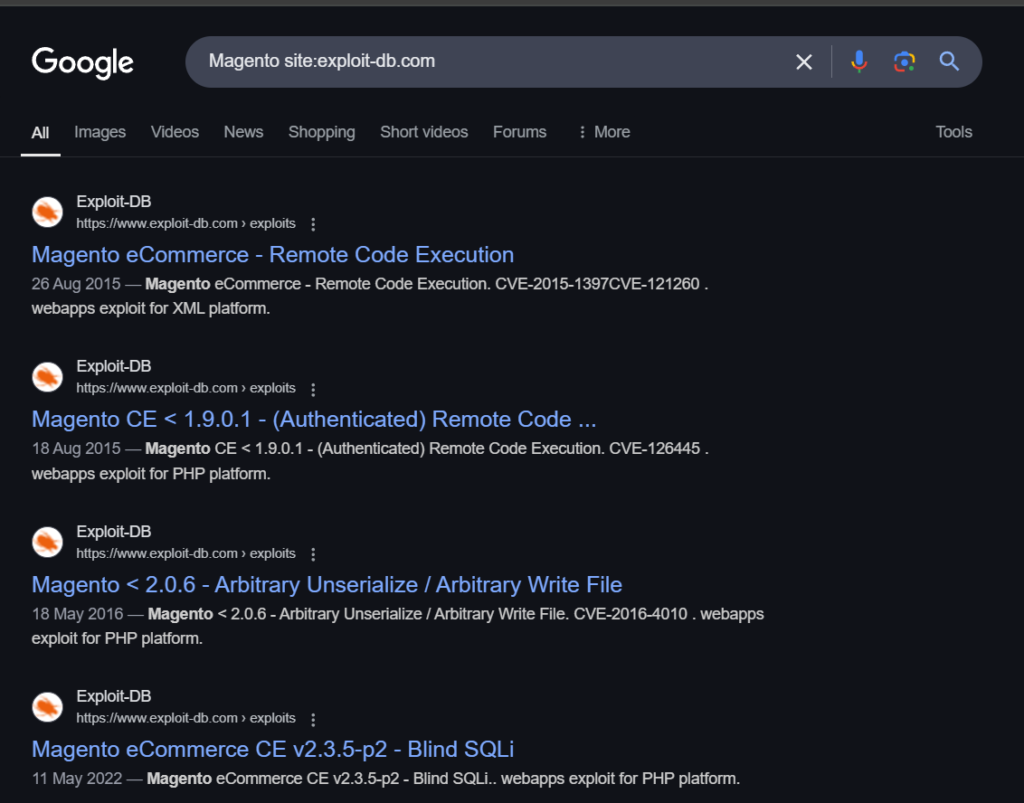

Results from this search will include exploits for previous versions of Magento as well as any recently found security holes that might be dangerous. A list of exploits with CVE identifiers, such as CVE-2021-1234, may be published. This allows you to verify the specifics of the vulnerability’s function and determine whether a Proof of Concept (PoC) is available.
Once relevant exploits have been identified, carefully review the PoC code to figure out whether the vulnerability applies to the Magento version you are testing. To find out if the CMS is vulnerable, you can test the exploit on your target (with their consent, of course).

In addition to finding single exploits you want to search GitHub to see if there is a tool that can scan for all the possible vulnerabilities and misconfigurations.
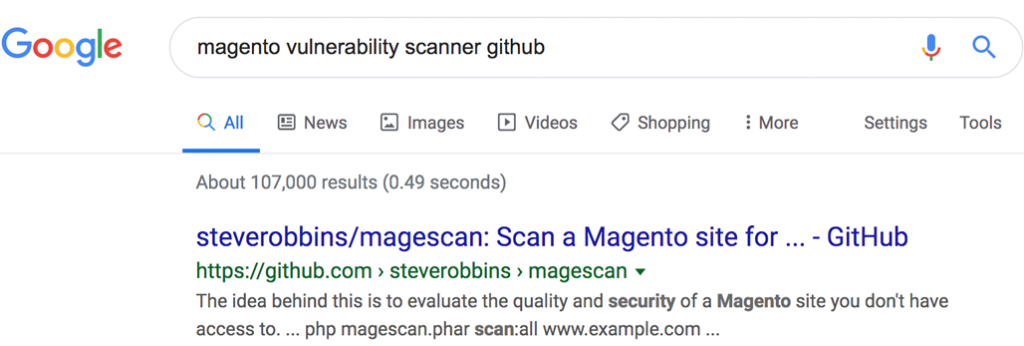
It turns out that Magescan, a vulnerability scanner for Magento, simplifies the procedure:
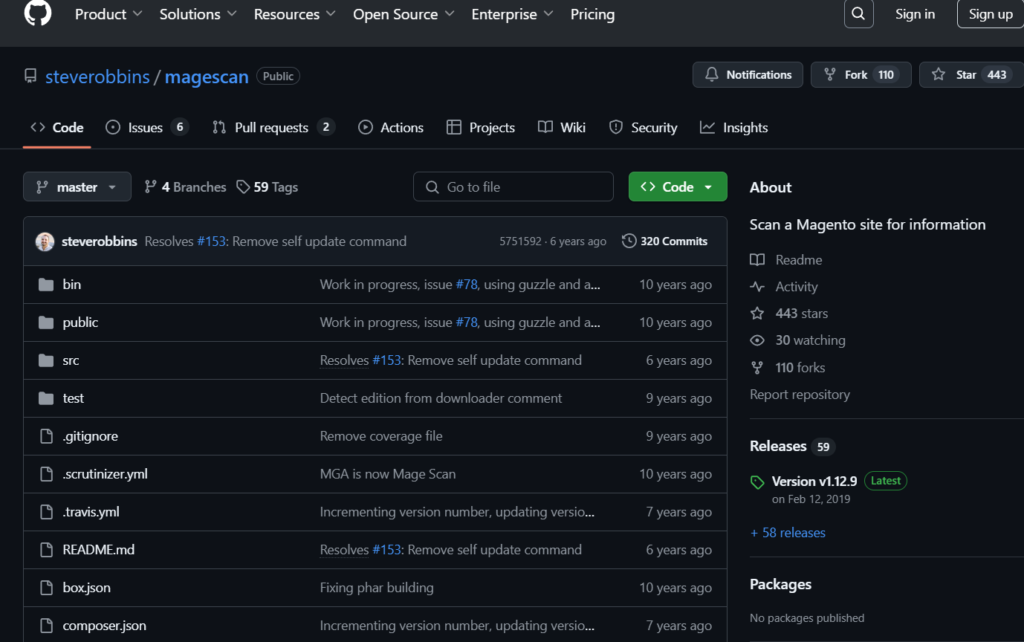
Make sure to use this process whenever you come across a CMS framework you don’t recognize.
Exploiting OWASP
Introduction to OWASP

The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
Do Keep An Eye on The Owasp 2025 Which will be published in the first halh of 2025 after 4 years the last top 10 are from 2021.

OWASP Top 10 (2021)
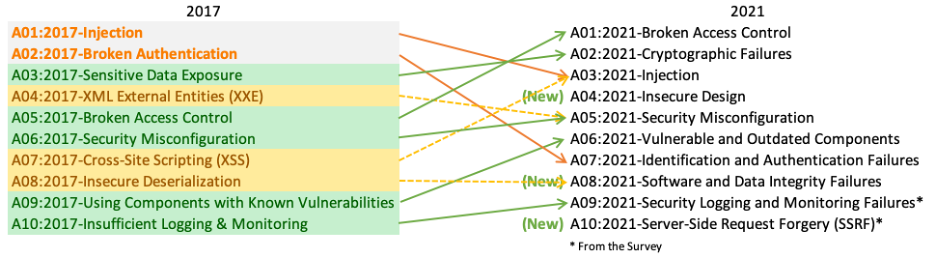
A01:2021: Access Control Is Broken
94% of apps have this problem, making it the most common one. When users have access to places they shouldn’t, it occurs. It is the top problem right now.
Cryptographic Failures (A02:2021)
Moving up to #2, this was previously referred to as Sensitive Data Exposure and deals with poor encryption that makes sensitive information public.
A03:2021: Injection
94% of apps are still affected by this problem, which includes SQL injection. With Cross-site Scripting (XSS) added, it is currently at #3.
A04:2021: Vulnerable Structure
Design issues that pose security vulnerabilities are the subject of this new category. It promotes the use of threat modeling and secure design concepts.
A05:2021: Misconfigured Security
This problem, which affects 90% of apps, rose from #6. It has to do with insufficient software setup and configuration, which results in vulnerabilities.
A06:2021: Outdated and Vulnerable Components
This category went up from number nine. Using out-of-date software or components with known security flaws is the problem, which is difficult to check for.
Identification and Authentication Issues A07:2021
This category, once known as “Broken Authentication,” has fallen. It solves problems with the user identity verification process.
A08:2021: Failures in Software and Data Integrity
a new category that focuses on assuming that data and software upgrades are secure without doing any research. Insecure deserialization is one of the topics it discusses.
A09:2021: Monitoring and Security Logging Issues
This category, which focuses on poor logging and monitoring systems—both of which are critical for identifying attacks—rose to #9.
A10:2021 – Server-Side Request Forgery (SSRF)
a recent development in which hackers tricked a server into sending unwanted queries, potentially harming internal systems.
You will find a great explanation of all the problems on the following page, so you should definitely check it out. Our investigation into the weaknesses and the attack on the OWASP Top 10 will begin tomorrow. For the time being, feel free to Google CMS platforms, search for weaknesses, and find them. It would be a treasure for you as a hacker if you also read about the OWASP Top 10 on the official OWASP website.


