Well done for making it to Day 8 of our free 10-day Bug Bounty Beginner Course! You have worked hard and been consistent great job! I am your trainer and brother, Dipanshu Kumar. We are going deeper into exploiting complex bugs today, refining your talents to take on increasingly difficult weaknesses. Continue your fantastic work.
We will be diving deeper into exploitation today. We will start by focusing on exploiting well-known CMS platforms knowing what they are and utilizing the appropriate resources to find weaknesses. Tomorrow We will go into the OWASP Top 10 bugs, which cover the most prevalent and important flaws you will find in the bug bounty community. Let us begin!
Focus on understanding the structure, plugins, and misconfigurations of CMS platforms when exploiting them. Focus on common entry points such as vulnerable file uploads, outdated plugins, and weak authentication. Use automation techniques to speed up the discovery process, but always conduct investigation by hand to identify more serious flaws. Numerous options for escalation and exploitation can be unlocked by gaining access to the admin panel.
Starting CMS Exploitation
Before Exploiting, You Need To Understand What Is CMS ?

A content management system (CMS) is a technology that enables non-programmers to generate, manage, and edit digital information, typically for websites. With an easy interface, users can more easily build new pages, edit text, upload images, and arrange information.
For example, a CMS enables you to construct a blog or business website without the need for technical knowledge. To administer your website, all you need are templates and tools.
Top CMS Examples
WordPress

The most well-known and widely used CMS is WordPress. Because of its great accessibility, beginners as well may easily construct blogs, portfolios, company websites, and even online storefronts. With a wide range of themes and plugins, WordPress allows users to personalize their websites without knowing any code. It has a large support group and is open-source.
Joomla

In terms of complexity, Joomla is a flexible CMS that is in the middle of WordPress and Drupal. It is known for its adaptability and capacity to manage complex websites with unique architecture.
Drupal
Large, enterprise-level websites are ideal for Drupal’s scalability and capability. It provides advanced capabilities including variable user rights, scalability for sites with large traffic, and unique content kinds. It is a popular option for developers building unique, high-security websites, while being more complicated and requiring technical know-how.

Wix
With the help of the drag-and-drop website builder Wix, beginners can easily and quickly construct websites without knowing any code. It is a complete package that offers templates for a range of websites, such as e-commerce sites, blogs, and portfolios. Wix is an all-around solution for creating websites as it also manages hosting and domain registration.
Shopify
Shopify is an e-commerce-focused CMS. It is made to make creating online stores simple and offers everything from payment processing to product administration. Additionally, Shopify provides a range of applications and themes to help personalize your store.

This should have given you a solid understanding of what a CMS is, and since I have given so many examples, the foundation should be clear as you move forward. You will be able to handle web development and vulnerability testing on CMS-based websites more easily if you are familiar with these systems.

Learning CMS Exploitation
We shall now study the section on exploitation. Following a review of the basics, we will get into the specifics of CMS platform exploitation, focusing technology, plugins, tools, and more to help you in identifying effectively exploiting vulnerabilities.
CMS Exploitation : WordPress
One popular command-line tool for checking WordPress websites for vulnerabilities is WPScan. By identifying problems like out-of-date plugins, themes, weak passwords, and more, it helps security researchers and bug bounty hunters in locating security flaws in WordPress websites.


Make sure WPScan is installed before using it. WPScan is compatible with Windows, Linux, and macOS. The installation steps are as follows:
sudo apt update
sudo apt install wpscaBasic Command: Scanning a Website


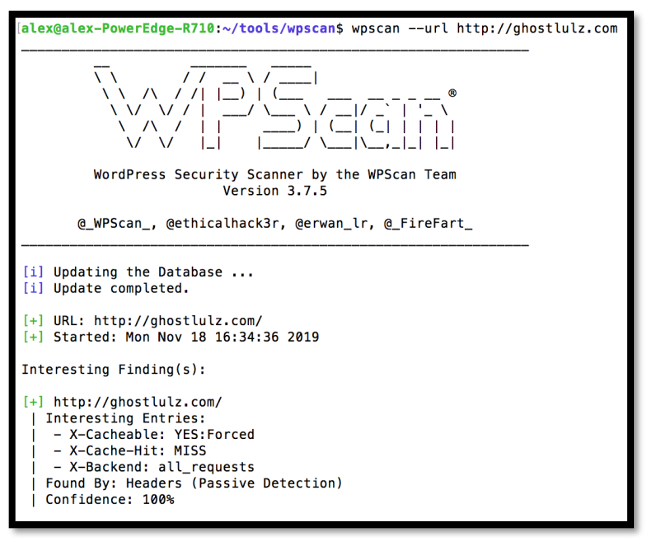
Basic Command: Enumerating Plugins, Enumerating Users,
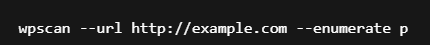



Full WPScan Command Example
wpscan --url http://example.com --enumerate ap --enumerate u --enumerate p --plugins-detection mixed
Directory Listing
Another thing I find all the time is directly listing on the uploads folder. Always make sure to check “/wpcontent/uploads/” .

CMS Exploitation : Joomla


Install
git clone https://github.com/rezasp/joomscan.git
cd joomscan
perl joomscan.plUsing Joomscan
Usage: joomscan.pl [options]
--url | -u <URL> | The Joomla URL/domain to scan.
--enumerate-components | -ec | Try to enumerate components.
--cookie <String> | Set cookie.
--user-agent | -a <user-agent> | Use the specified User-Agent.
--random-agent | -r | Use a random User-Agent.
--timeout <time-out> | set timeout.
--about | About Author
--update | Update to the latest version.
--help | -h | This help screen.
--version | Output the current version and exit.Do default checks...
perl joomscan.pl --url www.example.com
or
perl joomscan.pl -u www.example.com
Enumerate installed components...
perl joomscan.pl --url www.example.com --enumerate-components
or
perl joomscan.pl -u www.example.com --ec
Set cookie
perl joomscan.pl --url www.example.com --cookie "test=demo;"
Set user-agent
perl joomscan.pl --url www.example.com --user-agent "Googlebot/2.1 (+http://www.googlebot.com/bot.html)"
or
perl joomscan.pl -u www.example.com -a "Googlebot/2.1 (+http://www.googlebot.com/bot.html)"
Set random user-agent
perl joomscan.pl -u www.example.com --random-agent
or
perl joomscan.pl --url www.example.com -r
Set proxy
perl joomscan.pl --url www.example.com --proxy http://127.0.0.1:8080
or
perl joomscan.pl -u www.example.com --proxy https://127.0.0.1:443
Update Joomscan...
perl joomscan.pl --updateCMS Exploitation : Drupal
DroopScan is a Drupal website security scanner. It is intended to find common problems, configuration errors, and vulnerabilities in Drupal-based websites.
Droopscan Command Example

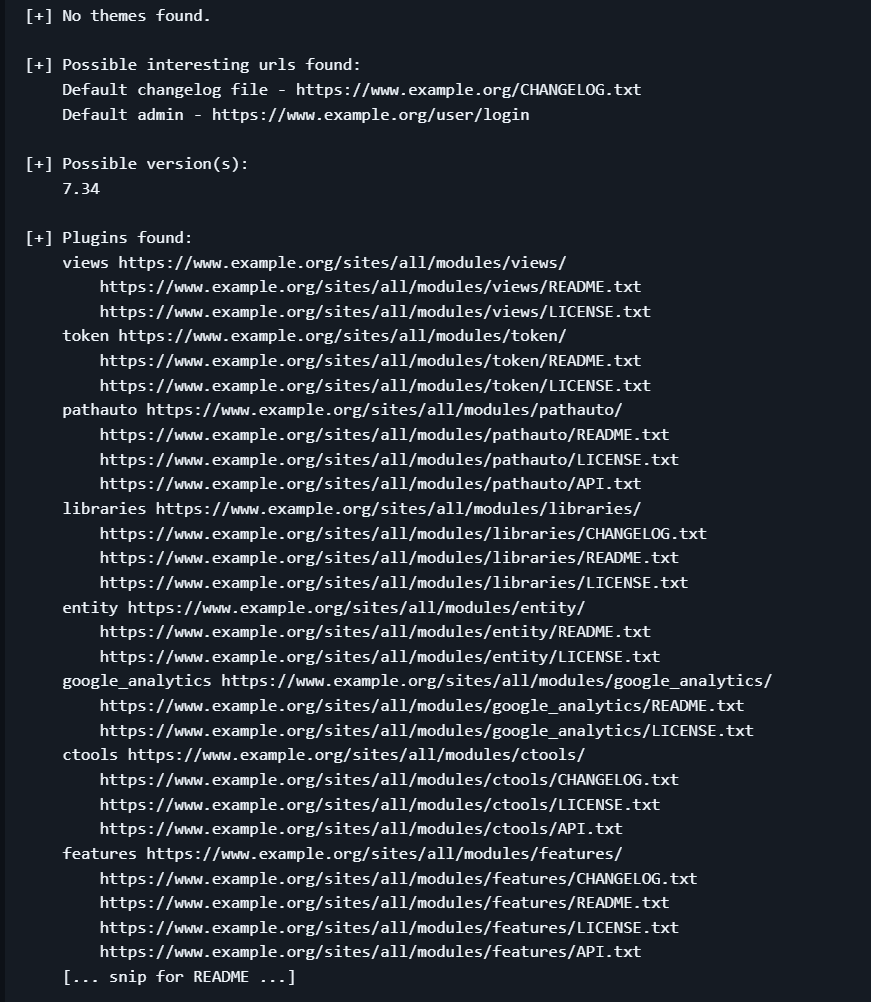
Using Droopscan
You can specify a particular host to scan by passing the -u or --url parameter:
droopescan scan drupal -u example.org
You can also omit the drupal argument. This will trigger “CMS identification”, like so:
droopescan scan -u example.org
Multiple URLs may be scanned utilising the -U or --url-file parameter. This parameter should be set to the path of a file which contains a list of URLs.
droopescan scan drupal -U list_of_urls.txt
The drupal parameter may also be ommited in this example. For each site, it will make several GET requests in order to perform CMS identification, and if the site is deemed to be a supported CMS, it is scanned and added to the output list. This can be useful, for example, to run droopescan across all your organisation’s sites.
droopescan scan -U list_of_urls.txWe will explore how to integrate CMS exploitation with Exploit DB tomorrow, discover and list PoCs (Proof of Concepts), and use them to our benefit. To help you improve, we will also go over the complex OWASP top 10 bugs. The last session of our 10-day Bootcamp will be this one!
Furthermore, you may receive two items rather than just one. I do not want to sacrifice the content’s quality. My objective is to ensure that everyone receives complete, accurate information that will be genuinely beneficial. Please be patient with me, readers of HackingBlogs; I am committed to give you the greatest and most useful information.


