Threat actor Intelbroker(alias) has hacked Apple. In June 2024, there was a data breach involving its internal tools.

A post published on the Bridge forums by Intel Broker in June 2024 revealed the internal source code for three frequently used Apple tools for their internal website.

Insights On Apple

With its headquarters located in Cupertino, California, Apple is a worldwide technology giant that is well-known for its game-changing products, which include the iPhone, iPad, Mac, and Apple Watch. Although Apple is well known for its cutting edge technology and superb user experience in terms of security, no security is effective when knowledgeable users are utilising the system.
Tools made public during the hack.
Apple Connect SSO
Apple uses a single sign-on solution internally.
Apple hwe Confluence advance
The following utility offers advance settings for Apple’s internal Confluence setup.
Apple macro plugin
It is a plugin that is probably meant to improve internal macro features.
Intelbroker’s threat profile

The actor from the thread Uses the pseudonym Intel broker when participating in illicit forums.
Since joining in June 2023, Intel Broker has a stellar reputation with a reputation core of 350 and 797 posts.
The primary activity this thread activity deals with is the sale of valuable access and information on forums related to cybercrime.
Intel broker has previously claimed to have data taken from Europol and Amd hacks.
Intel Broker said in a dark web bridge forum post.
“I am sharing the internal source code to three of Apple’s commonly used tools for their internal site thanks for reading and enjoy,”
Analysis performed by AHCTS

The leak appears to consist of three repositories:
apple-hwe-confluence-datacenter-advanced-theme-master@2b322a08e3e- Files last modified April 27th 2024
appleconnect-sso-master@d8c514aa3f1- Files last modified September 27, 2016
applemacroplugin-master@83c95519e8a- Files last modified August 10, 2019
HMTS Custom Theme for Confluence
A specific style created for Apple’s internal Confluence instance is called HMTS (Hardware, Manufacturing, and Test Solutions) custom theme. By modifying Confluence’s functional and visual elements, it seeks to give the HMTS team a customised user experience. To this end, it makes use of a number of CSS stylesheets, JavaScript files, and image assets.
<properties>
<confluence.version>6.0.7</confluence.version>
<confluence.data.version>6.0.7</confluence.data.version>
<amps.version>6.2.4</amps.version>
<plugin.testrunner.version>1.2.3</plugin.testrunner.version>
<atlassian.spring.scanner.version>1.2.6</atlassian.spring.scanner.version>
<atlassian.plugin.key>${project.groupId}.${project.artifactId}</atlassian.plugin.key>
</properties>AppleConnect SSO Integration for Confluence and Jira
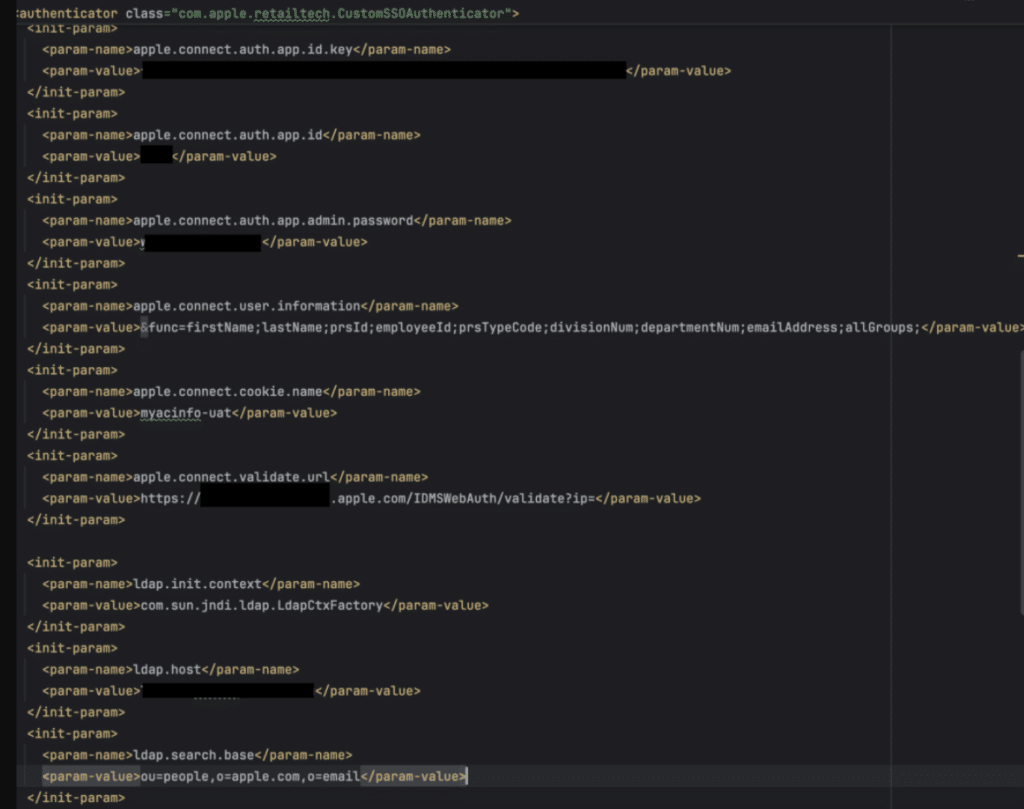
Confluence and Jira components are included in the appleconnect-sso plugin package. The purpose of these plugins is to replace the default Seraph authenticators with unique implementations that use AppleConnect SSO to authenticate users. This makes it possible for Apple workers to log in to Jira and Confluence with ease using their AppleConnect login credentials.
RadarViewer Macro Plugin for Confluence
The applemacroplugin-master@83c95519e8a directory contains the RadarViewer plugin, which is intended to give a macro for embedding radar visualisations into Confluence pages. Radar data integration and display are made possible by the REST services, web components, and configuration files included in this plugin.
<dependencies>
<dependency>
<groupId>com.atlassian.templaterenderer</groupId>
<artifactId>atlassian-template-renderer-api</artifactId>
<version>1.5.4</version>
<scope>provided</scope>
</dependency>
<dependency>AHCTS Takeaway
Significant cybersecurity risks are associated with the leak of the custom plugins created for Apple’s internal Confluence and Jira instances. However, the exposed code does not contain any tools that affect Apple end-user products or services, nor does it contain any actively exploitable threats. What is exposed are sensitive data and detailed configurations that could be used by malicious actors. It is still unclear where the leak came from, but it could have come from cPrime, the outside firm that developed these plugins, or from Apple’s internal systems.
The hack serves as a reminder of the value of safe development environments, strict access regulations, and thorough security audits in safeguarding private data and preserving the integrity of vital infrastructure parts.

Andrew On X “Analysing the #Apple Internal Tool Leak in Detail Watch this space for real-time updates on analysis once the write-up is finished!”


