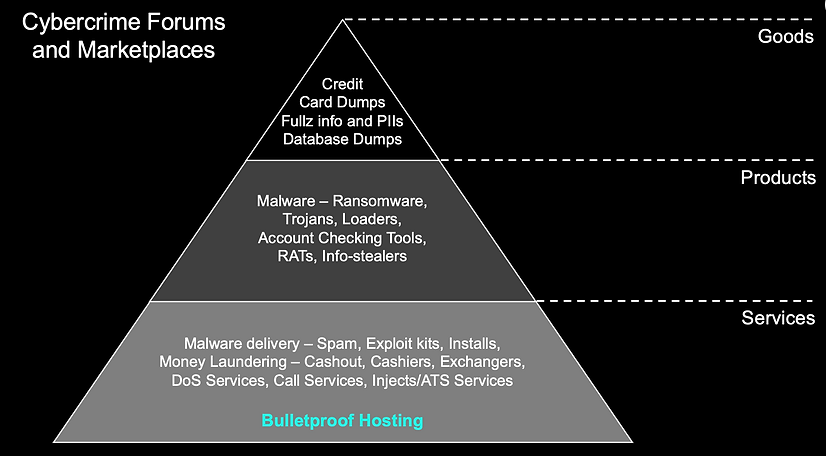
Hackingblogs: Before it is too late, you should learn about bulletproof hosting, or BPH. This technology is being used by hackers worldwide to host illicit marketplaces, distribute malware, and conduct phishing attacks. I will explain this in great detail for you in this post.
Why should we care about BPH and what is their role in the cybercriminal ecosystem?
A BPH is a particular kind of hosting service that enables users to purchase domains and rent servers in secret for the purpose of engaging in illicit or grey market activity. Cybercriminals can use a BPH to facilitate various activities such as hosting illicit markets, operating Command-and-Control servers (C2), distributing malware or spam, scanning networks for vulnerabilities, and initiating phishing operations.
BPH can be used by state-sponsored organisations to host websites that spread misinformation, by extremist groups to further their ideologies, and by hacktivists to perform denial-of-service assaults.
Recognising Threat Actors’ Need for BPH via LockBit
Operation Cronos was successful on May 7, 2024, when M. Dmitry Khoroshev, the head of the LockBit ransomware gang, was deanonymized by law enforcement. Several cybersecurity and intelligence firms released their findings regarding M. Khoroshev and LockBit is infrastructure at the same time.
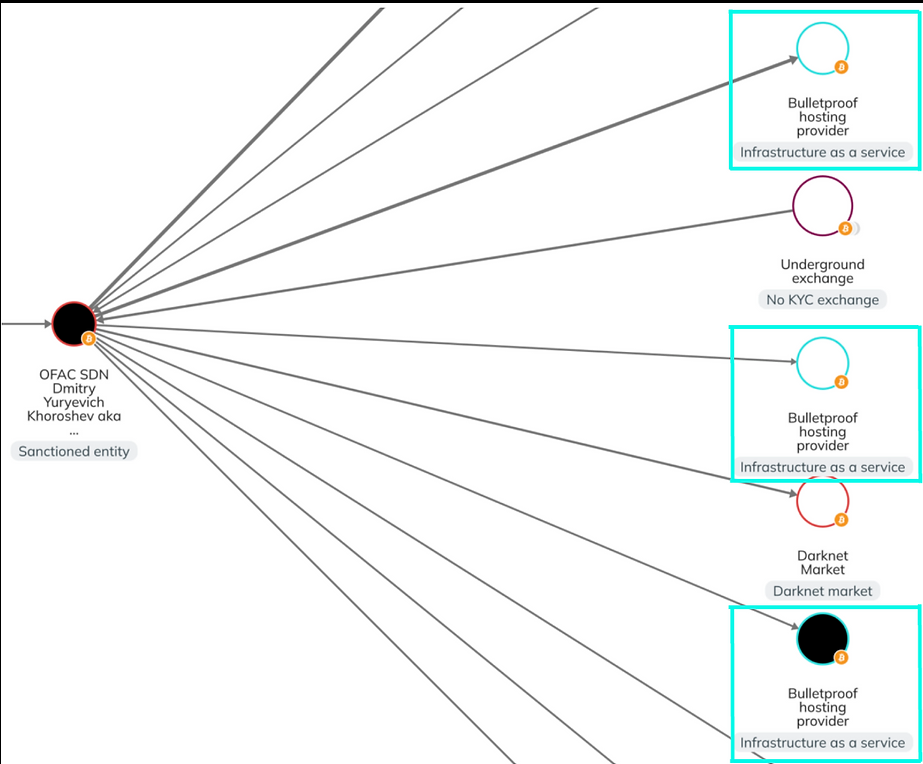
A company called Chainalysis, which specialises in blockchain analysis, released one noteworthy article. Their analysis of cryptocurrency transfers from LockBit is wallets to other criminal organisations’ wallets exposed links between LockBit and darknet markets, bulletproof hosting services (BPH), and underground exchanges.
The requirement for LockBit to employ a minimum of three separate BPH providers suggests that bulletproof hosting is an essential component of the ecosystem used by cybercriminals.
In order to host its victim blog and assist affiliates in obtaining data from affected businesses, LockBit has employed BPH services. Like other threat actors, the group’s affiliates employ BPH to carry out vulnerability assessments or to mask their true IP address with a number of unique VPNs and proxies.
Difficulty in Law Administration Of these Services
The fact that a large number of bulletproof hosting services are run in nations with different legislative frameworks than the US makes them much more dangerous. Bulletproof hosting sites are frequently linked to operations in China or Russia, or to nations in Eastern Europe where it is doubtful that government agents will be kicking down their doors.
U.S. enterprises impacted by their consumers will not have many legal options because of their location in these nations, which can shield them from legal action from nations like the U.S.
Examples of Bph Services
Controversial web server Cyberbunker is well-known for facilitating websites involved in illicit activities like spamming, hacking, and the distribution of content protected by copyright. Unknown hosting company AltHost provides anonymous hosting for websites that might not be permitted on popular hosting platforms.
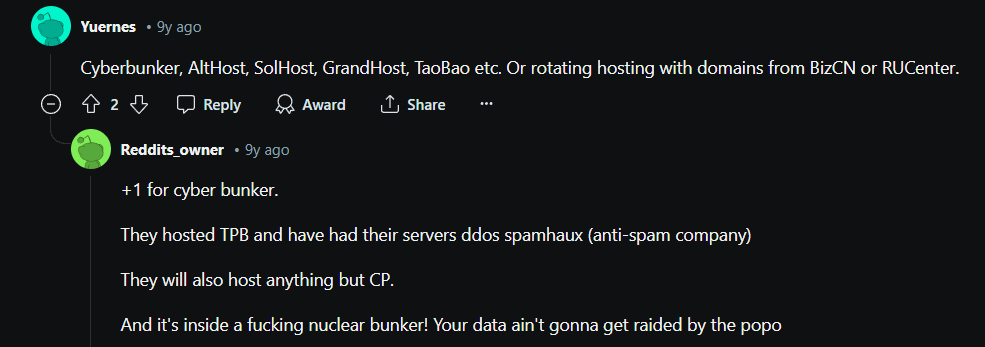
Reputable hosting company SolHost provides both individuals and companies with dependable and secure hosting solutions. Another reputable host with a range of hosting packages for various website kinds is GrandHost.
Rotating hosting with BizCN or RUCenter domains is a tactic employed by certain website owners to continuously switch hosting companies and domain registrars to evade detection and closure by law enforcement. This technique is frequently linked to websites that partake in illicit activities like virus distribution, phishing, and scamming.
CyberBunker Case Study

Although there are BPHs like this, they are usually not very long-lasting and fairly pricey. One well-known instance was “CyberBunker,” which was shut down by police in 2019. It was housed in a decommissioned Cold War bunker in the Netherlands and then in Germany.

These cutting-edge impregnable hosting services in unique settings or private residences are uncommon. The majority of BPHs are located in typical data centres, however they are frequently concealed behind front businesses to protect their owners from needless scrutiny.
Quick Wakthrough of Current Situation
There are forty BPH services running right now on XSS and Exploit. Despite the emergence of 17 new BPH services in the last two years, established, reliable services still hold a significant market share.
These hosting companies differ greatly from one another, even though they all refer to their services as “bulletproof hosting” in their promotional posts. The primary distinctions are found in the services they provide, usage restrictions (ToS), hardware, costs, infrastructure, and reputation.
The views of threat actors towards BPH providers provide insight into their true potential and demonstrate that they are not a panacea. Stability, support quality, and blacklisting by security firms with a good reputation are the primary problems. Threat actors using BPH services usually create shells to conceal their identities.
Summarising Once Again
In contrast to traditional hosting services, bulletproof hosting offers users a high level of anonymity and permits websites to function in a more permissive legal environment.
These hosting services are frequently linked to accepting or covering up information and actions that are typically forbidden by mainstream hosting companies because they violate local laws or moral standards.
It is crucial to remember that not everyone who uses bulletproof hosting is involved in illegal activity. Some people use these services for legitimate reasons, like hosting content that is both legal and controversial or protecting data privacy and the right to free speech in places where those rights are restricted.
It observed that two forums, XSS and Exploit, had the largest number of bulletproof hosting services.


