Linux systems are vulnerable to multiple unpatched vulnerabilities, as revealed by security researcher Simone Margaritelli. Attackers can execute remote code on Linux computers that use the CUPS (Common Unix Printing System) printing system due to a serious vulnerability.
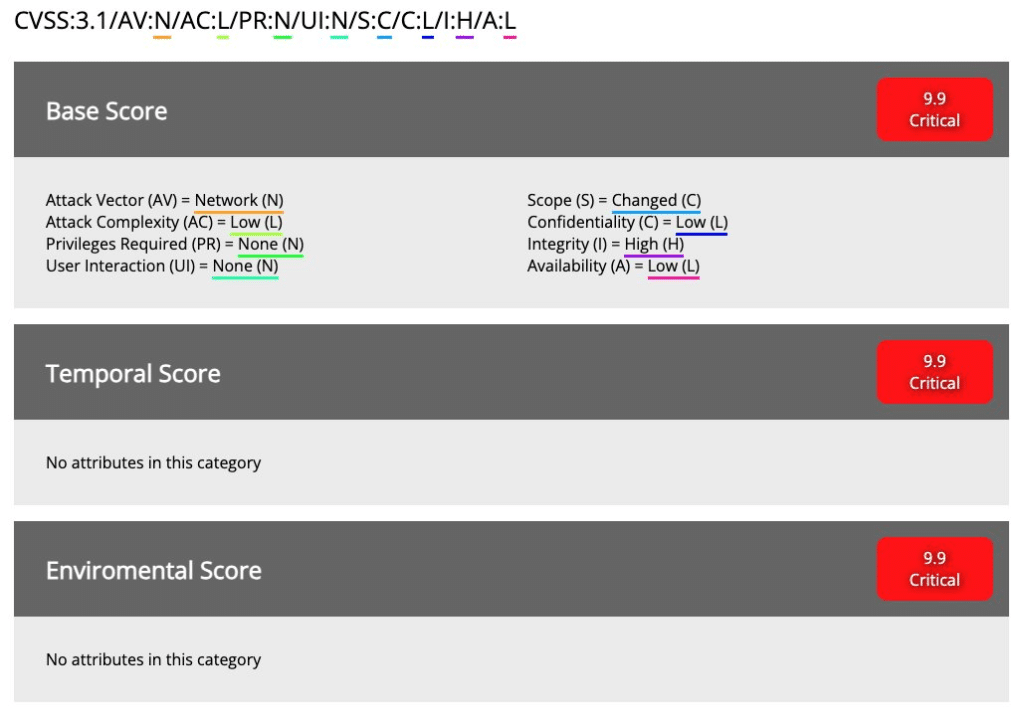

CUPS, It can listen on UDP port 631 if the cups-browsed daemon is activated, which is not the case on most computers, according to Margaritelli’s findings. Additionally, it will by default enable remote connections to be established from any networked device to establish a new printer.
What is CUPS ?
As cups-browsed finds new printers and adds them to the system automatically, it is in fact a component of the CUPS system. Before the user had a choice or be informed, Linux simply added anything it discovered on a network.
Findings on the Flaw
The researcher used netstat -anu in a terminal while setting up Ubuntu on a fresh laptop to see which services were listening on UDP ports. After examining the output, to which he noticed.

The 0.0.0.0 portion, according to him, is particularly strange since it indicates that any process that is listening on port 631 is also listening on and responding to any network interface you may have, including LAN, WAN, and VPN. Investigating using a lsof -i:631, which verified CUPS on 631 tcp in addition to this other process, cups-browsed Finally, ps aux | grep "cups-brow" verified that this process executes as root.


This service is expecting a UDP packet in the pattern HEX_NUMBER HEX_NUMBER TEXT_DATA. If the allowed function for the given source IP returns true, further actions will take place.
He found that it was possible to construct an illegal PostScript Printer Description (PPD) printer that could be manually advertised to a UDP port 631-based exposed cups-browsed service. The foomatic-rip filter adds the command to run while printing, which causes a device to run commands in order to output a print job appropriately.
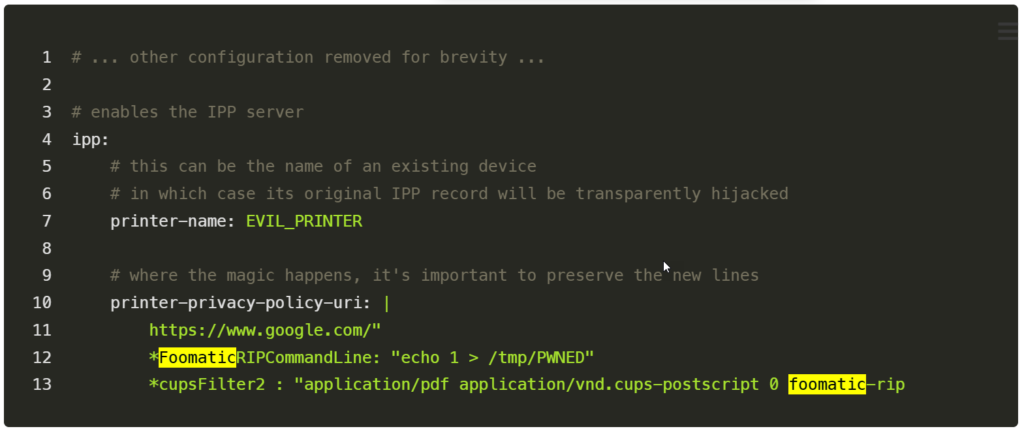
In this video, you can see the researcher on his attacker PC (on the left) attacking the brand-new laptop, which is running cups-browsed 2.0.1 on a fully patched Ubuntu 24.04.1 LTS, and obtaining command execution using the first version of this exploit:
Mitigation Steps
In order to break the attack chain, Red Hat disclosed mitigation steps that require administrators to use the following commands to halt the cups-browsed service’s operation and prevent it from starting upon reboot:

sudo systemctl stop cups-browsed
sudo systemctl disable cups-browsedUsers of Red Hat can also use the following command to check if their computers are running cups-browsed:
sudo systemctl status cups-browsedThe system is safe if the outcome shows “Active: inactive (dead),” indicating that the exploit chain has been broken. The system is vulnerable if the result is “running” or “enabled” and the configuration file /etc/cups/cups-browsed.conf has the value “cups” for the “BrowseRemoteProtocols” directive.


