A record-breaking $75 million ransom was recently paid to the infamous cybercriminal outfit known as Dark Angels Ransomware, making headlines.
In the history of ransomware attacks, the payment of a $75 million ransom sets a record. This stunning sum shows the growing confidence of cybercriminals and their ability to take advantage of weak prey in order to make large sums of money.
The fact that the victim chose to pay so much shows how dangerous it is to have inadequate backups or other options in case the encrypted data needs to be restored. Concerns and Implications The record-breaking ransom payment that followed the Dark Angels ransomware outbreak raises a number of issues and effects for both individuals and organisations.
Understanding Dark Angels Team ransomware
The Dark Angels Team ransomware-like programme was found by pcrisk researchers when they were reviewing fresh submissions to VirusTotal. Based on our analysis, this malicious software is a member of the Babuk ransomware family.

We discovered that it encrypts files and appends the “.crypt” extension to their filenames after running a sample on our test system. For instance, all of the impacted files had the initial file name “1.jpg” appearing as “1.jpg.crypt,” “2.png” as “2.png.crypt,” and so on.
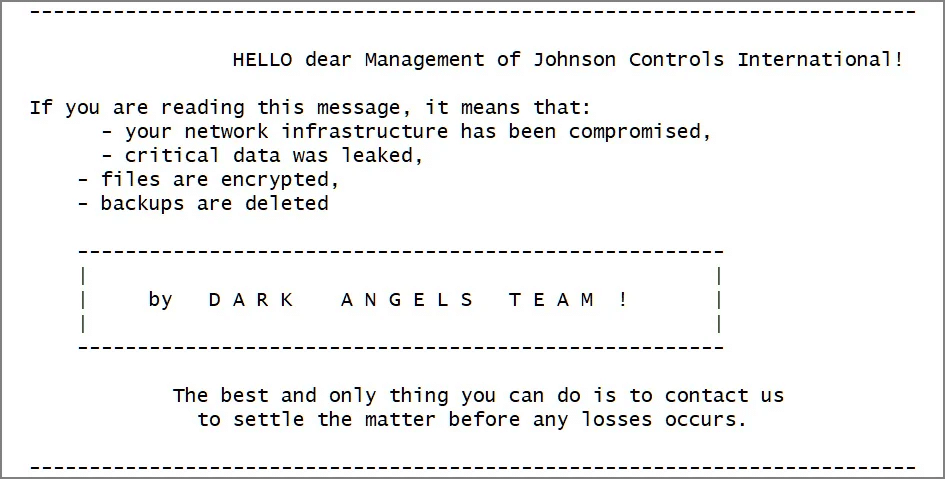
The ransom letter “How_To_Restore_Your_Files.txt” was placed onto the desktop by this ransomware once the encryption process was finished. A link to a Tor website, which displayed content identical to the ransom letter, was placed in this file. It is clear from these communications that Dark Angels Team targets businesses rather than individual consumers.
Screenshot of files encrypted by the ransomware Dark Angels Team:

Malware Analyisis Of How_To_Restore_Your_Files.txt
Target
How_To_Restore_Your_Files.txt
Size
1KB
MD5
59b88fd446ba78a90840a98c094117e3
SHA1
875fb952328dcbf0b6c2312ec6ee7d650fcfc29c
SHA256
fdde6eab66d83fb89dcf102ab9688f0141f26ace707b0f319d3fd88c2d3e1363
SHA512
5c3235c9e1059a5cd97ffddd6da05a4f31cb45a739fd5c73317ca19f2778f7a8c0ffaee8d0bc3bf45851c4e8e8f0ba24c4285fb8570a505212ab556da8ddf2c7
Score
1/10
Malware Config
Signatures
Opens file in notepad (likely ransom note) 1 IoCs
ransomware
Processes
C:\Windows\system32\NOTEPAD.EXE
C:\Windows\system32\NOTEPAD.EXE C:\Users\Admin\AppData\Local\Temp\How_To_Restore_Your_Files.txtAn unusual ransom payment
Crypto intelligence firm Chainalysis, which tweeted about this payment on X, further verified this record breaking amount.

Zscaler stated the company was in the Fortune 50 and the incident happened in early 2024, but they did not reveal which corporation paid the $75 million ransom.

In addition, the threat actors run a website called “Dunghill Leaks” where they blackmail people by threatening to release data unless they pay a ransom.
“The Dark Angels group employs a highly targeted approach, typically attacking a single large company at a time,”
Zscaler ThreatLabz researchers.


