A major security vulnerability in the most recent version of WhatsApp for Windows lets hackers send attachments that contain PHP and Python scripts that execute quietly when the person who received them opens them.
This problem reminds me of a vulnerability that was found in April in Telegram for Windows. Though they later fixed it, the developers at the time first ignored the problem. Attackers were able to transfer a Python file with the.pyzw extension through Telegram’s messenger, thereby evading security alerts and remotely executing code.

Finding the Vulnerability
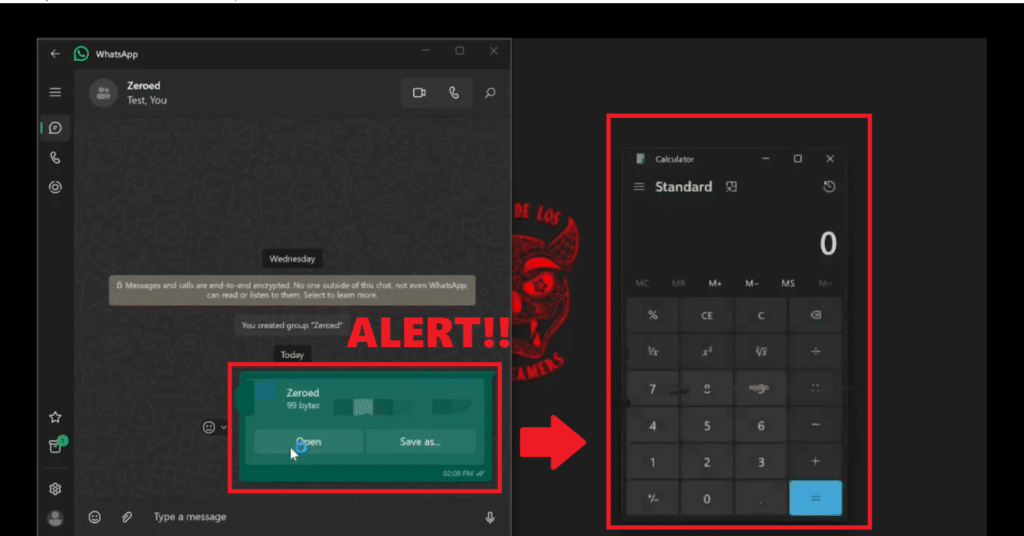
While exploring with file types that might be linked to WhatsApp conversations to determine if the app supports any of the dangerous ones, security researcher Saumyajeet Das discovered the vulnerability. When forwarding a potentially hazardous file, like.EXE, WhatsApp displays it and presents the user with two choices: Save As or Open.

BleepingComputer’s additional investigation supported Das‘ conclusions and revealed that PHP scripts were not included in WhatsApp’s blacklist.
Python needs to be installed on the victim’s machine in order for an attack to be successful, which limits the pool of possible targets to researchers, software developers, and advanced users. This restriction, however, does not lessen how serious the issue is.
It is interesting that WhatsApp restricts a lot of other potentially harmful file formats. For example, the application shows a warning and gives the user only two options: “Open” or “Save As” when attempting to send files with the extensions.EXE,.COM,.SCR,.BAT, or Perl. The only way out for users with such files is to save them to disc and execute them from there when they try to open them.
Every time one of them tried to open them by clicking “Open” directly from the program, an error occurred. They could only be executed after being saved on disc.

In an interview with BleepingComputer, Das revealed that he discovered three file types—.PYZ (Python ZIP app),.PYZW (PyInstaller programme), and.EVTX (Windows event Log file)—that the WhatsApp client does not prevent from opening.
Tests conducted by BleepingComputer verified that WhatsApp does not prevent Python files from running and found that PHP scripts have the same effect.
The recipient only needs to click the “Open” button on the file they have received in order for the script to run if all the necessary resources are available.
Das contacted Meta on June 3 to report the issue, and on July 15 the company responded, stating that another researcher had already brought attention to the problem.
The researcher contacted BleepingComputer to report that the problem was still reproducible on Windows 11, v2.2428.10.0, and that it was still present in the most recent WhatsApp update for Windows.
“I have reported this issue to Meta through their bug bounty program, but unfortunately, they closed it as N/A. It’s disappointing, as this is a straightforward flaw that could be easily mitigated,”
Das Concluded
“We’ve read what the researcher has proposed and appreciate their submission. Malware can take many different forms, including through downloadable files meant to trick a user.”
“It’s why we warn users to never click on or open a file from somebody they don’t know, regardless of how they received it — whether over WhatsApp or any other app.
Team, Meta
Additionally, the company official disclosed that WhatsApp has a mechanism in place to alert users when they get messages from individuals who are not on their contact lists or whose phone numbers are registered in a foreign nation.
However, if an attacker manages to take control of a user’s account, they can distribute malicious scripts, which are simpler to run directly from the messaging app, to every contact on the list.
Additionally, threat actors may exploit these attachments to distribute malicious files by posting them in both private and public chat rooms.
WhatsApp had not yet provided an explanation for why the PHP extension wasn’t restricted at the time of publication. As of right now, users of Windows versions of WhatsApp are encouraged to take extra care while opening attachments, particularly if they contain PHP or Python scripts.


