(Fake Solidity Addon) A serious threat on X was reported, where a serious issue regarding installation of unknown VS Code Plugins which could easily exploit your windows system.Let’s see what happened with the researcher and what did he report.
Identification Of Illicit Plugin On VS Code Marketplace
According to researcher Lorenz Lehmann’s report, He installed a malicious extension with a single click. Fortunately, as his computer does not run Windows, he was unharmed.
He said that hackers are becoming increasingly advanced and do not only target amateurs. Here’s how they accomplish it and how to keep your coins safe.
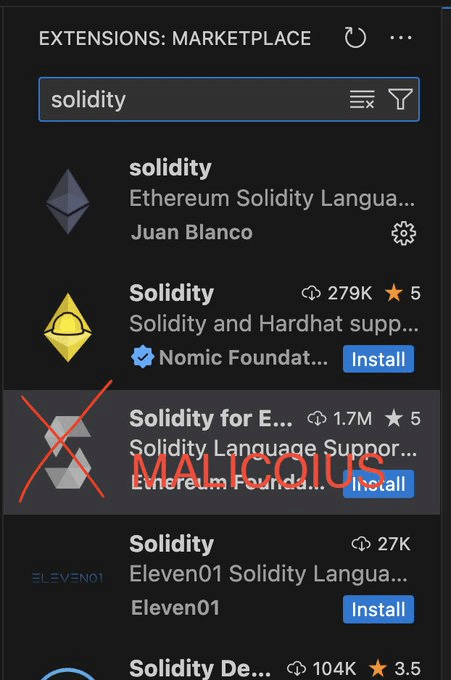


Fake Addon for Solidity on Market Place
Do you want to learn Solidity programming? It sounds great to have an easy VS Code addon for formatting code. After finding the most often used package, select Install and there you are compromised in a matter of seconds.
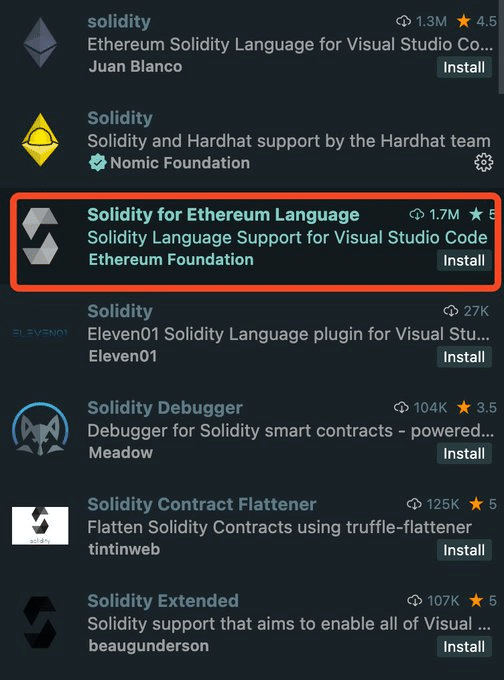
Users of VScode, please make sure you did not accidentally install this fake Solidity extension. Both the Juanblanco and the Nomic ones are genuine.
The faked extension code is obviously unusable and severely obfuscated. It appears to be limited to windows. Even though the installs are most likely bots, make sure to check to see if it is installed; if it is, remove and report it.

Although the fake extention displayed had such excellent quality examples

How was this work done on the backend ?
The first cause for concern is that, although having an unknown developer, this extension has received 1.7 million downloads (more than any other) and a flawless rating of 5 stars in just one day of launch.Everything looks normal after downloading and extracting the malicious extension, with the exception of an obfuscated "extension.js" file that launches automatically after installation.


We can observe that “extension.js” initiates an invisible download of a 5MB file called “1.cmb” from a Russian server after passing it through a de-obfuscator. Sadly, “1.cmb” is likewise purposefully obscured, which makes it considerably more difficult to decipher what is actually happening.To track which activities are being performed, we can reformat the code and add echo log commands with a short Python script. We then use a virtual machine (VM) to run it.


The log file shows that the script eventually errors, but we can see how it operates:
- The attack is executed fully in memory,
- leaving no evidence on the disc,
- making it challenging for anti-malware software to identify.

It depends on PowerShell for its execution. similar to a fileless malware assault. In order to protect VMs from reverse engineering, the script even recognises them..
The extension is no longer in effect



