Is Your email hacked ?A lot of time it seems to appear in the news and you find out millions and millions of credentials are being sold on the dark web become conscious is there my data also present you know how to check it if it is present or not awesome tutorial I will be talking on a very interesting topic or how to check if your email has been hanged or cracked somewhere.
Also don’t forget to check other gold content for you as a hacker to learn on our official site hackingblogs.com we bring new and updated content just for you now without further time being taken let us get started
Is Your email hacked ? Let’s Check
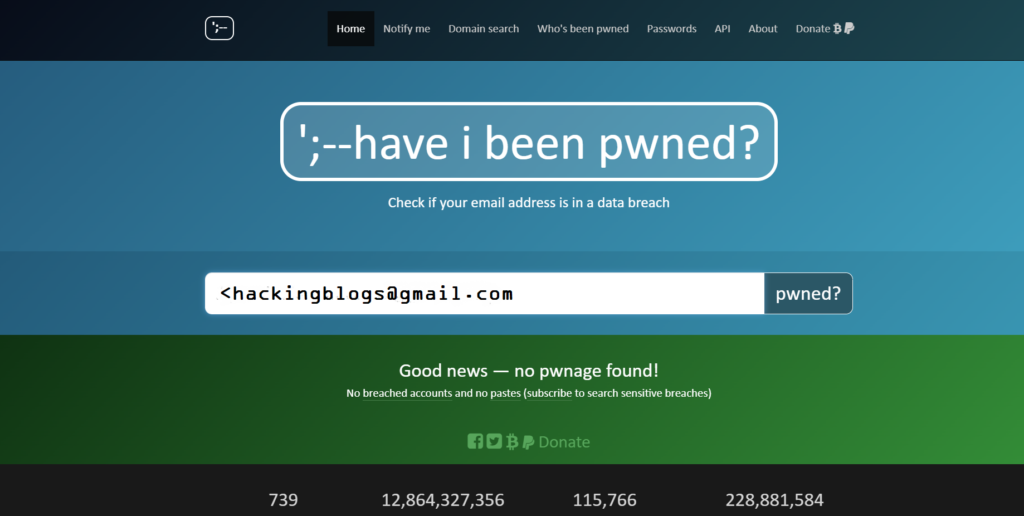
haveibeenpwned.com
This is a very interesting website because it tells you Is your email hacked ? or not in any of the data breaches this is a very good website that generates results only after checking public leaks 60000 unique visitors a day to this website contains 4.8 million accounts over 251 data breaches so this will be a very helpful website to check if your email has been hacked.
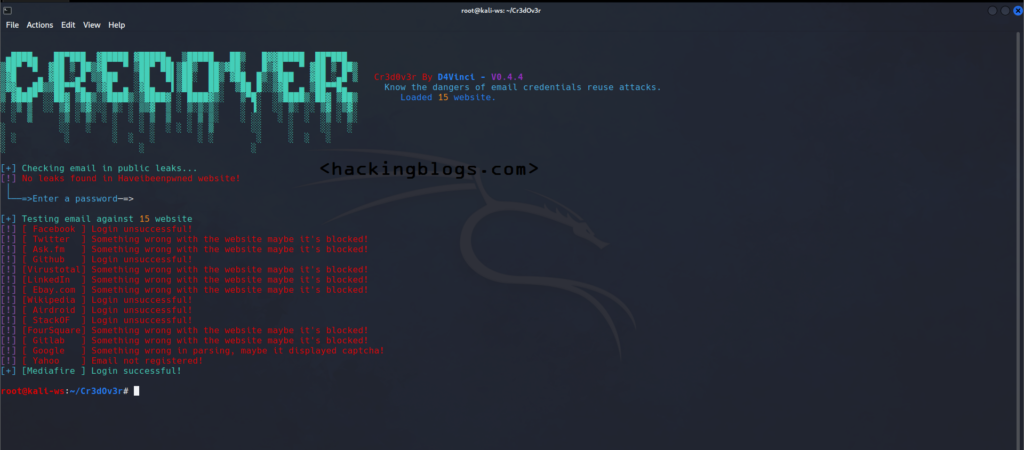
cr3d0v3r tool
So this tool basically generates true results it also shows the result from the mentioned website Is your email hacked ? or not it will start checking seven different websites on which your website account is working with your old password
if your email address was compromised before then simply check on which website your account is working after the collection of all the information change the password from that particular website in which your email has been worked on late install this tool by cloning the following GitHub repository.
Installation
git clone https://github.com/D4Vinci/Cr3dOv3r.gitcd Cr3dOv3rpython3 -m pip install -r requirements.txtpython3 Cr3d0v3r.py -hFrequently Asked Questions
-
What is haveibeenpwned?
– Haveibeenpwned is a website that allows you to check Is your email hacked ? or has been compromised in a data breach.
-
How does haveibeenpwned work?
– Haveibeenpwned works by collecting and analyzing data from known data breaches and allows users to search for their email addresses or passwords in these breached datasets.
-
Is haveibeenpwned safe to use?
– Yes, haveibeenpwned is a reputable and secure website that is widely used by individuals and organizations to check for potential data breaches.
-
Can I check multiple email addresses on haveibeenpwned?
– Yes, you can check multiple email addresses on haveibeenpwned by entering each email address separately in the search bar.
-
What should I do if my email address shows up in a data breach on haveibeenpwned?
– If your email address shows up in a data breach on haveibeenpwned, it is recommended to change your password for the affected account and enable two-factor authentication if available.
-
Can I check if my password has been compromised on haveibeenpwned?
– Yes, you can check if your password has been compromised on haveibeenpwned by entering it in the password search feature on the website.
-
Is haveibeenpwned free to use?
– Yes, haveibeenpwned is free for individual users to check if their email addresses and passwords have been compromised in data breaches.
-
Does haveibeenpwned store my email address or password?
– Haveibeenpwned does not store email addresses or passwords entered by users during the search process. It only checks them against its database of known breaches.
-
Can organizations use haveibeenpwned to check their employees’ email addresses?
– Yes, organizations can use haveibeenpwned’s enterprise services to monitor and check their employees’ email addresses for potential data breaches.
-
How often is haveibeenpwned updated with new data breaches?
– Haveibeenpwned is regularly updated with new data breaches as they are discovered and reported, ensuring that users have access to the latest information about potential compromises.