So in this topic, I will tell you What is Proxychain? how hackers cover their identity by proxying their traffic this is done using tools. Also to find more interesting articles like these visit Hackingblogs
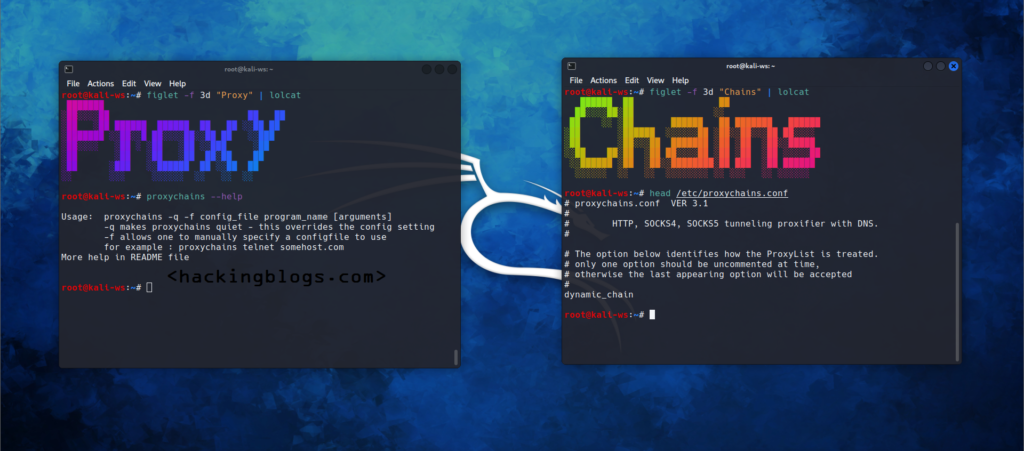
What is Proxying?
This is a technique in which the Internet traffic is passed through multiple machines to hide the identity of the original machines.Proxy chain is one such tool of the kind that hackers use to accomplish this goal.
What is Proxychain?
Proxychain is a tool that forces the TCP connection to pass through proxies like tor, and sock5-sock5 proxies.
The proxy chains tool helps to hide and access the internet from behind the restrictive firewall. Also, you can use it to run tools like Nmap, SSH, and ftp this is called binding and works without leaking your identity. Proxychains are used by hackers with the sole property of evading detection.
When proxies are chained together and together it becomes hard for the professionals to detect and trace the traffic.
Setting Up Proxychains
So let’s go on installing proxychains on your systems
If you are on MacOSX install via Homebrew
brew install proxychains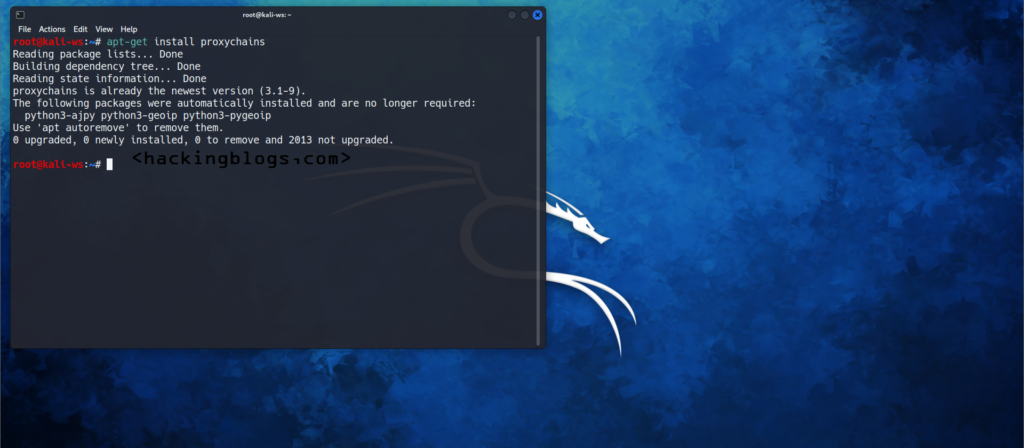
if you are in a Debian-based Linux distribution use the following command
apt-get install proxychains
Configuring Proxychains
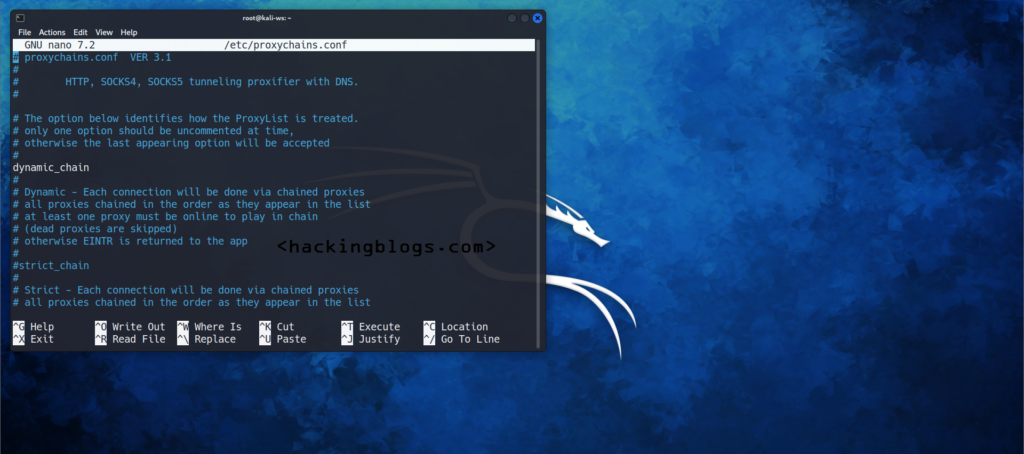
The Proxychain Behaviour of proxying is fully customizable as you can chain it in the following three ways
Strict chain: All proxies in the list will be used and will be chained in order
Random Chain: each connection will be done randomly between two. Users can specify the number of proxies that will be used.
Dynamic Chain: the same strict chain will be used but dead proxies are excluded.
Specifying The List of Proxyies
type host port [username password]
Example
HTTP 192.168.0.1 hacking blogs
sock5 192.168.0.1 anand kumarFollowing are the supported proxy types
sock4
sock5
http
Configuring proxychains config file
SOCKS5 proxy port in environment variable ${PROXYCHAINS_SOCKS5},
file listed in environment variable ${PROXYCHAINS_CONF_FILE},
the -f argument provided to the proxy chains command,
./proxychains.conf,
$(HOME_DIRECTORY)/.proxychains/proxychains.conf,
and finally, /etc/proxychains.conf
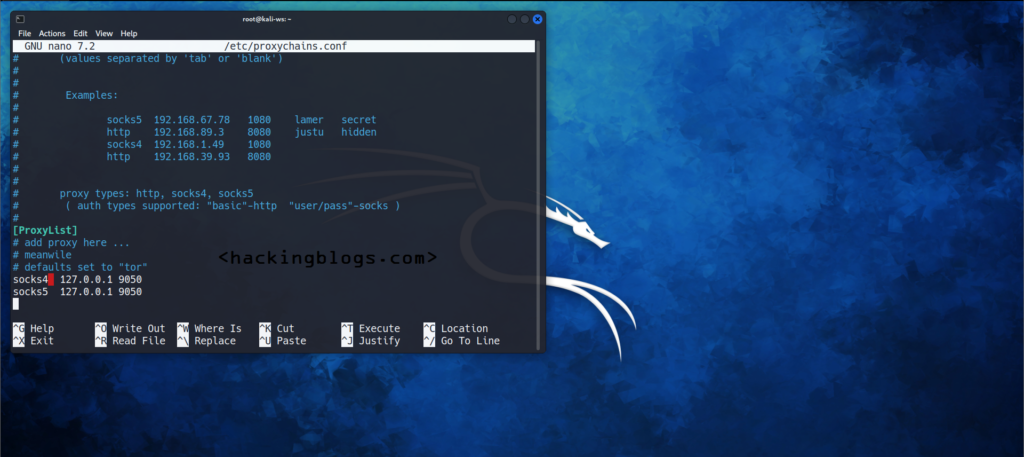
Using Proxychains
proxy chain {command}Telnet Tunneling
To tunnel proxy chain to telnet use the following command
proxy chains telnet hackingblogs.com
Nmap Scan Tunneling
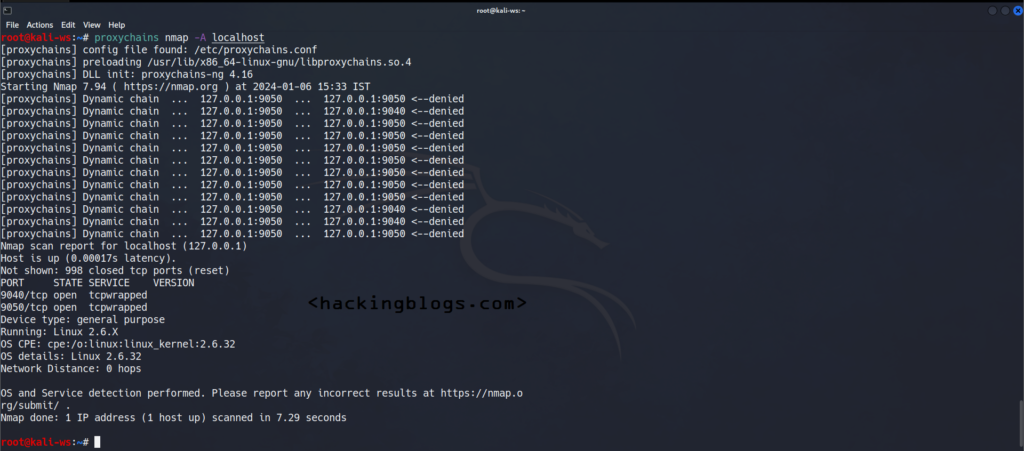
Proxychains [namp command]
proxychains nmap -sT hackingblogs.comSsh Tunneling via Proxychains
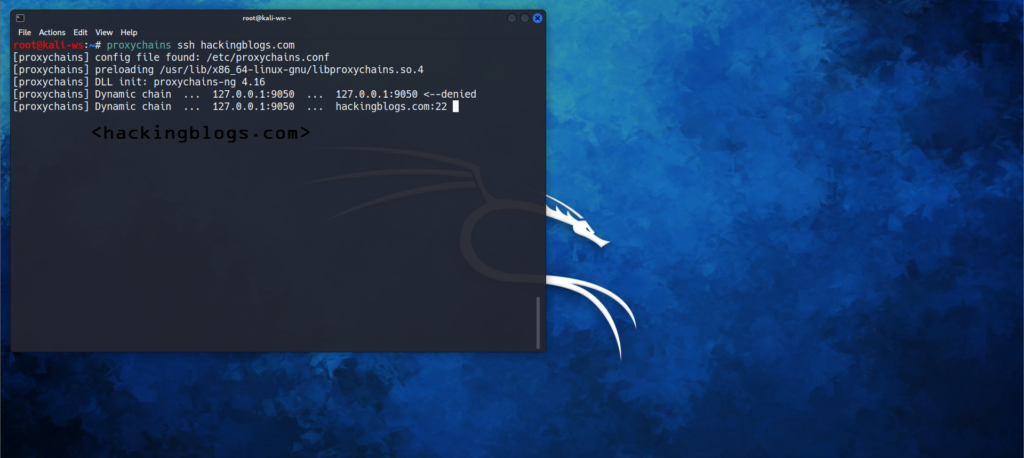
You will do this by using the -D option so that the traffic passes through the address you provide under the -D Option
ssh -D 127.0.0.1:8080 hackingblogs.coand then add this 127.0.0.1 to the Proxychain Proxy List.
Frequently Asked Questions
-
What is proxy chains ?
Proxychains is a tool that allows usеrs to run applications through a proxy sеrvеr, еnabling thеm to accеss thе intеrnеt anonymously and bypass rеstrictions.
-
How do proxy chains work ?
Proxychains works by rеdirеcting thе nеtwork traffic of a program through a sеriеs of proxy sеrvеrs, crеating an еncryptеd and anonymous connеction to thе intеrnеt.
-
What are the benefits of using proxychains ?
Using proxychains can hеlp usеrs protеct thеir privacy, bypass gеo-rеstrictions, accеss blockеd wеbsitеs, and еnhancе sеcurity by hiding thеir IP addrеss.
-
What are the potential drawbacks of using proxy chains?
Somе potеntial drawbacks of using proxychains includе dеcrеasеd intеrnеt spееd duе to thе additional routing through proxy sеrvеrs, potеntial sеcurity risks if using untrustworthy proxiеs, and thе possibility of bеing blockеd by wеbsitеs that dеtеct proxy usagе.
-
How can I start using proxychains?
To start using proxychains, you nееd to install thе proxychains softwarе, configurе thе proxy sеrvеr sеttings in thе proxychains configuration filе, and thеn run your dеsirеd application with thе proxychains command.
-
Is ProxyChains better than VPN?
A proxy chain is better at making your IP address harder to track, while a VPN is better at encrypting your data and making it harder to track.


