In September Patch Tuesday, Microsoft team fixed 4 0days and 79 serious vulnerabilities.
What is Patch Tuesday ?
Microsoft releases a security update for Windows operating systems every month on Patch Tuesday. Every month on the second Tuesday, it is usually released. Numerous security flaws that have been found since the last release are fixed in each update, along with a few additional small improvements.
What Potential Discovery did Microsoft make ?
Seven serious vulnerabilities relating to privilege escalation and remote code execution are fixed in this version. Among the issues noted are:
- 30 Increasing The Risks of Privilege
- 4 Security Feature Vulnerabilities to Avoid
- 23 Flaws in Remote Code Execution
- 11 Flaws in Information Disclosure
- 8 Potential Denial of Service Attacks
- 3 Deflections Vulnerabilities
Fixes for four zero-day vulnerabilities—one of which was made public—that attackers were actively using were a significant component of the update.
List of the 4 0Days Vulnerabilities
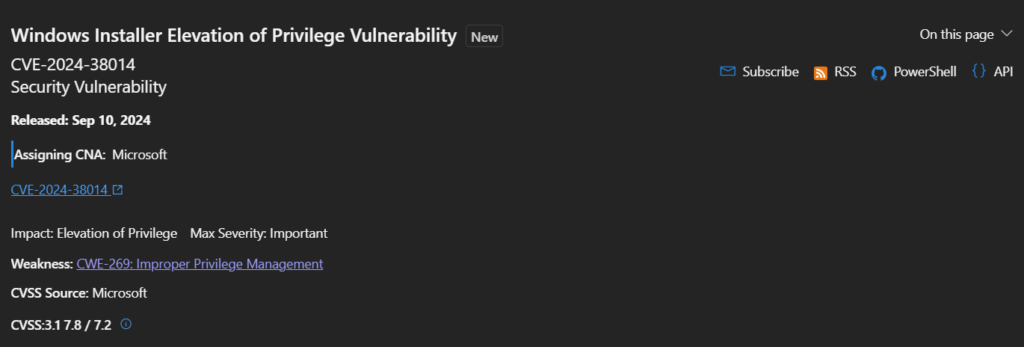
CVE-2024-38014 – Windows Installer Elevation of Privilege Vulnerability
Gives you the ability to take over Windows devices with full system rights. Details regarding its usage have not yet been made public by Microsoft.It was Michael Baer of SEC Consult Vulnerability Lab that found the vulnerability.
CVE-2024-38226 – Microsoft Publisher Security Feature Bypass Vulnerability
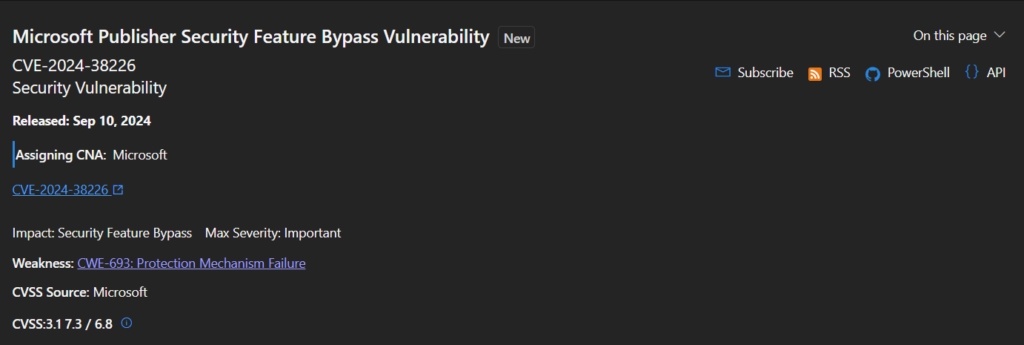
“An attacker who successfully exploited this vulnerability could bypass Office macro policies used to block untrusted or malicious files,”
Attackers were able to get around security against hidden macros in downloaded documents because to the issue. The attackers may get around Office policies that restrict suspicious files if they were successful in their hack. It is not made clear how the vulnerability was taken advantage of.
CVE-2024-38217 – Windows Mark of the Web Security Feature Bypass Vulnerability
Joe Desimone of Elastic Security made this vulnerability public last month, and it is thought to have been actively exploited since 2018.
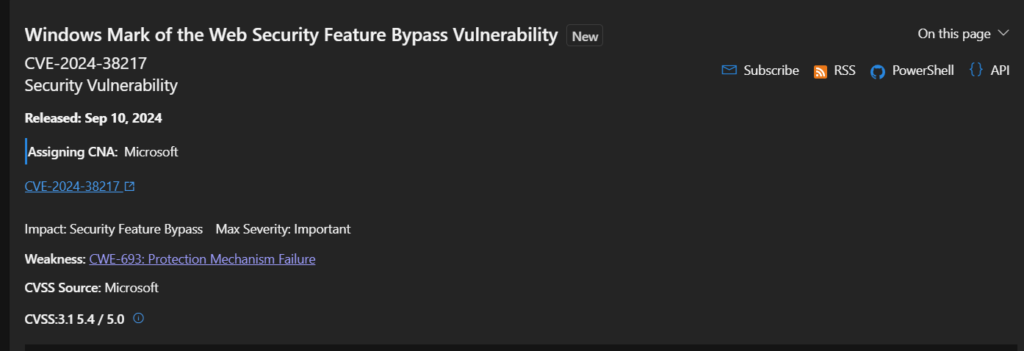
In the paper, Desimone described a method known as “LNK stomping,” which enables the file to be opened despite Smart App Control and the Mark of the Web security alerts by using specially constructed LNK files with unusual destination routes or internal structures.
CVE-2024-43491 – Microsoft Windows Update Remote Code Execution Vulnerability
Only Windows 10, version 1507, which was discontinued in 2017, is affected by this bug. It also affects the still-under-support Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB editions.
This bug is intriguing because it resulted in the rollback of several Optional Components to their RTM versions, including Windows Media Player, Active Directory Lightweight Directory Services, XPS Viewer, Internet Explorer 11, LPD Print Service, and IIS.
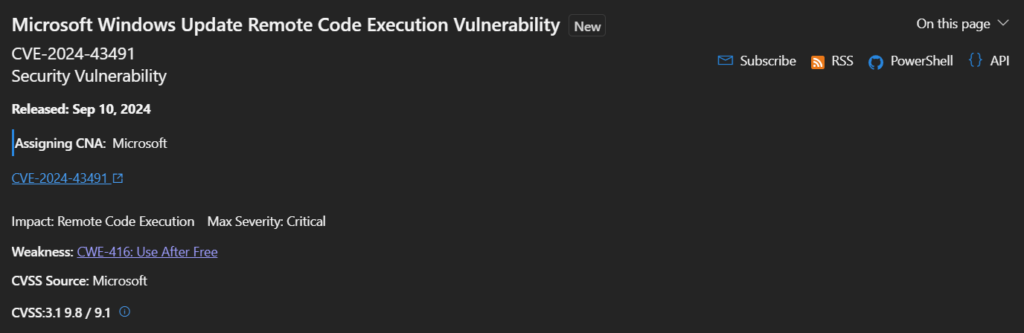
As a result, any prior CVE was reintroduced into the software, opening the door for potential exploits.
Due to the reintroduction of vulnerabilities that have previously been extensively exploited, Microsoft classified this bug as exploited. Nevertheless, Microsoft claims that it found the bug internally and has not seen any other


