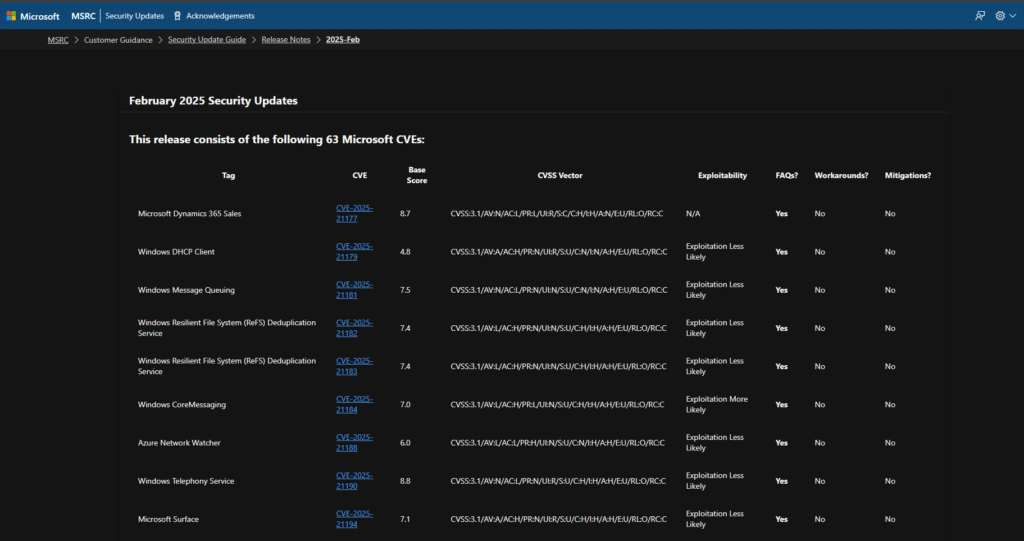
As usual, Microsoft delivered the Tuesday patch, fixing 63 security issues that affected its software products, including two vulnerabilities that it claimed were being actively exploited in the wild. Updates for actively exploited zero-day vulnerabilities have been made available by Microsoft. Federal agencies have three weeks, until March 4th, to put the mitigations into effect, according to CISA.
Three of the sixty-three vulnerabilities have been classified as Critical, fifty-seven as Important, one as Moderate, and two as Low in severity. Apart from this, Microsoft has fixed 23 bugs in its Edge browser, which is based on Chromium, since last month’s Patch Tuesday update.
Let’s Talk About The Flaws
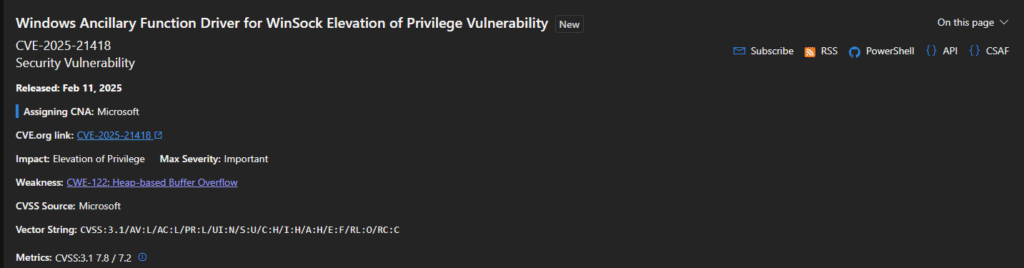
- CVE-2025-21418 (CVSS score: 7.8) – Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2025-21391 (CVSS score: 7.1) – Windows Storage Elevation of Privilege Vulnerability
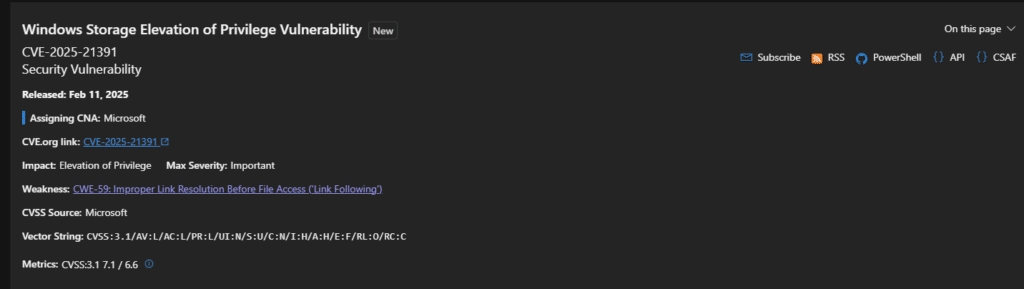
“An attacker would only be able to delete targeted files on a system,” Microsoft said in an alert for CVE-2025-21391. “This vulnerability does not allow disclosure of any confidential information, but could allow an attacker to delete data that could include data that results in the service being unavailable.”
This vulnerability, known as CVE-2025-21391, gives attackers the ability to increase privileges, remove data, and stop services from working. The severity is 7.1 out of 10.
“This vulnerability could allow an attacker to delete data, including data that results in the service being unavailable,”
CISA added in its advisory.
The Windows Ancillary Function Driver for WinSock is the source of a heap-based buffer overflow vulnerability. Advanced Windows networking functions are managed by this central component. Successful exploiters of this vulnerability, known as CVE-2025-21418, are granted SYSTEM privileges. There are currently no alternative mitigations or solutions available, and the exploit code is functional. Microsoft assigned a 7.8 out of 10 severity rating to this defect.
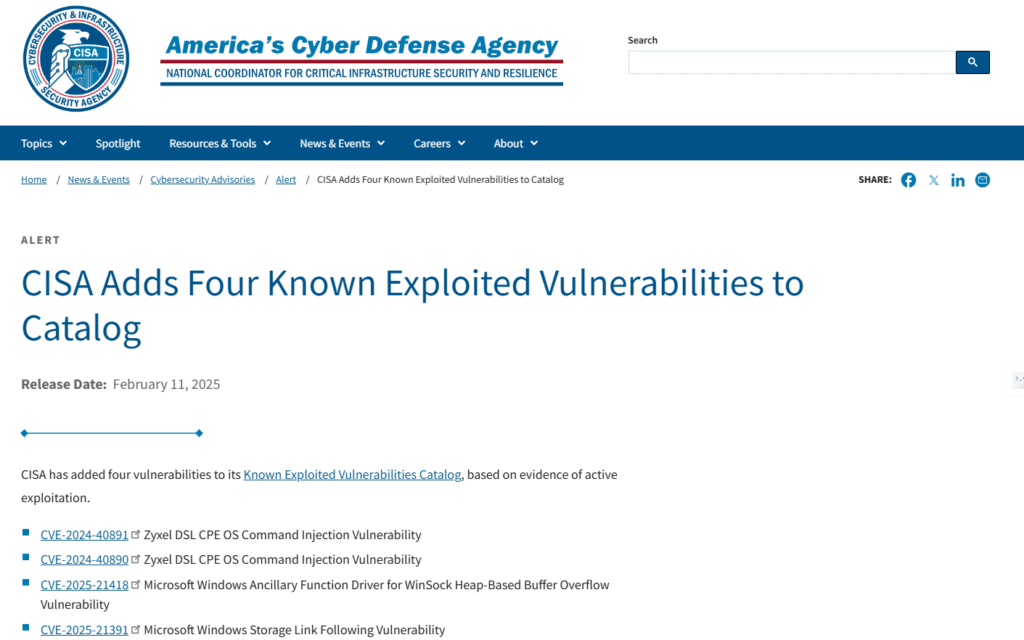
Whether the Lazarus Group is also connected to the misuse of CVE-2025-21418 is unknown at this time. Both vulnerabilities have been added to the U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalogue, and federal agencies must implement the fixes by March 4, 2025.
These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise. BOD 22-01 requires Federal Civilian Executive Branch (FCEB) agencies to remediate identified vulnerabilities by the due date to protect FCEB networks against active threats. See the BOD 22-01 Fact Sheet for more information.
Although BOD 22-01 only applies to FCEB agencies, CISA strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice. CISA will continue to add vulnerabilities to the catalog that meet the specified criteria.
Said CISA In There Advisory
Microsoft High Performance Compute (HPC) Pack Remote Code Execution Vulnerability : CVE-2025-21198
CVE-2025-2119, a remote code execution (RCE) vulnerability in the High Performance Compute (HPC) Pack, is the most serious of the vulnerabilities Microsoft fixed in this month’s update. By submitting a specifically constructed HTTPS request to the Linux compute node or the targeted head node, an attacker might take advantage of this vulnerability and perform RCE on other clusters or nodes that are connected to the targeted head node.
| CVE | Title | Severity | CVSS | Public | Exploited | Type |
| CVE-2025-21418 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Important | 7.8 | No | Yes | EoP |
| CVE-2025-21391 | Windows Storage Elevation of Privilege Vulnerability | Important | 7.1 | No | Yes | EoP |
| CVE-2025-21194 | Microsoft Surface Security Feature Bypass Vulnerability | Important | 7.1 | Yes | No | SFB |
| CVE-2025-21377 | NTLM Hash Disclosure Spoofing Vulnerability | Important | 6.5 | Yes | No | Spoofing |
| CVE-2025-21379 | DHCP Client Service Remote Code Execution Vulnerability | Critical | 7.1 | No | No | RCE |
| CVE-2025-21177 | Microsoft Dynamics 365 Sales Elevation of Privilege Vulnerability | Critical | 8.7 | No | No | EoP |
| CVE-2025-21376 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | Critical | 8.1 | No | No | RCE |
| CVE-2025-21188 | Azure Network Watcher VM Extension Elevation of Privilege Vulnerability | Important | 6 | No | No | EoP |
| CVE-2025-21179 | DHCP Client Service Denial of Service Vulnerability | Important | 4.8 | No | No | DoS |
| CVE-2023-32002 * | HackerOne: CVE-2023-32002 Node.js `Module._load()` policy Remote Code Execution Vulnerability | Important | 9.8 | No | No | RCE |
| CVE-2025-21212 | Internet Connection Sharing (ICS) Denial of Service Vulnerability | Important | 6.5 | No | No | DoS |
| CVE-2025-21216 | Internet Connection Sharing (ICS) Denial of Service Vulnerability | Important | 6.5 | No | No | DoS |
| CVE-2025-21254 | Internet Connection Sharing (ICS) Denial of Service Vulnerability | Important | 6.5 | No | No | DoS |
| CVE-2025-21352 | Internet Connection Sharing (ICS) Denial of Service Vulnerability | Important | 6.5 | No | No | DoS |
| CVE-2025-21375 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-24036 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability | Important | 7 | No | No | EoP |
| CVE-2025-21368 | Microsoft Digest Authentication Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21369 | Microsoft Digest Authentication Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21279 * | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | Important | 6.5 | No | No | RCE |
| CVE-2025-21283 * | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | Important | 6.5 | No | No | RCE |
| CVE-2025-21342 * | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21408 * | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21383 | Microsoft Excel Information Disclosure Vulnerability | Important | 7.8 | No | No | Info |
| CVE-2025-21381 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21386 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21387 † | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21390 † | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21394 | Microsoft Excel Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21198 | Microsoft High Performance Compute (HPC) Pack Remote Code Execution Vulnerability | Important | 9 | No | No | RCE |
| CVE-2025-21181 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability | Important | 7.5 | No | No | DoS |
| CVE-2025-21392 | Microsoft Office Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21397 | Microsoft Office Remote Code Execution Vulnerability | Important | 7.8 | No | No | RCE |
| CVE-2025-21259 | Microsoft Outlook Spoofing Vulnerability | Important | 5.3 | No | No | Spoofing |
| CVE-2025-21322 | Microsoft PC Manager Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-21400 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Important | 8 | No | No | RCE |
| CVE-2025-24039 | Visual Studio Code Elevation of Privilege Vulnerability | Important | 7.3 | No | No | EoP |
| CVE-2025-24042 | Visual Studio Code JS Debug Extension Elevation of Privilege Vulnerability | Important | 7.3 | No | No | EoP |
| CVE-2025-21206 | Visual Studio Installer Elevation of Privilege Vulnerability | Important | 7.3 | No | No | EoP |
| CVE-2025-21351 | Windows Active Directory Domain Services API Denial of Service Vulnerability | Important | 7.5 | No | No | DoS |
| CVE-2025-21184 | Windows Core Messaging Elevation of Privileges Vulnerability | Important | 7 | No | No | EoP |
| CVE-2025-21358 | Windows Core Messaging Elevation of Privileges Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-21414 | Windows Core Messaging Elevation of Privileges Vulnerability | Important | 7 | No | No | EoP |
| CVE-2025-21347 | Windows Deployment Services Denial of Service Vulnerability | Important | 6 | No | No | DoS |
| CVE-2025-21420 | Windows Disk Cleanup Tool Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-21373 | Windows Installer Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-21350 | Windows Kerberos Denial of Service Vulnerability | Important | 5.9 | No | No | DoS |
| CVE-2025-21359 | Windows Kernel Security Feature Bypass Vulnerability | Important | 7.8 | No | No | SFB |
| CVE-2025-21337 | Windows NTFS Elevation of Privilege Vulnerability | Important | 3.3 | No | No | EoP |
| CVE-2025-21349 | Windows Remote Desktop Configuration Service Tampering Vulnerability | Important | 6.8 | No | No | Tampering |
| CVE-2025-21182 | Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | Important | 7.4 | No | No | EoP |
| CVE-2025-21183 | Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | Important | 7.4 | No | No | EoP |
| CVE-2025-21208 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21410 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21419 | Windows Setup Files Cleanup Elevation of Privilege Vulnerability | Important | 7.1 | No | No | EoP |
| CVE-2025-21201 | Windows Telephony Server Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21190 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21200 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21371 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21406 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21407 | Windows Telephony Service Remote Code Execution Vulnerability | Important | 8.8 | No | No | RCE |
| CVE-2025-21367 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | Important | 7.8 | No | No | EoP |
| CVE-2025-21253 | Microsoft Edge for IOS and Android Spoofing Vulnerability | Moderate | 5.3 | No | No | Spoofing |
| CVE-2025-21267 * | Microsoft Edge (Chromium-based) Spoofing Vulnerability | Low | 4.4 | No | No | Spoofing |
| CVE-2025-21404 * | Microsoft Edge (Chromium-based) Spoofing Vulnerability | Low | 4.3 | No | No | Spoofing |
| CVE-2025-0444 * | Chromium: CVE-2025-0444 Use after free in Skia | High | N/A | No | No | RCE |
| CVE-2025-0445 * | Chromium: CVE-2025-0445 Use after free in V8 | High | N/A | No | No | RCE |
| CVE-2025-0451 * | Chromium: CVE-2025-0451 Inappropriate implementation in Extensions API | Medium | N/A | No | No | RCE |


