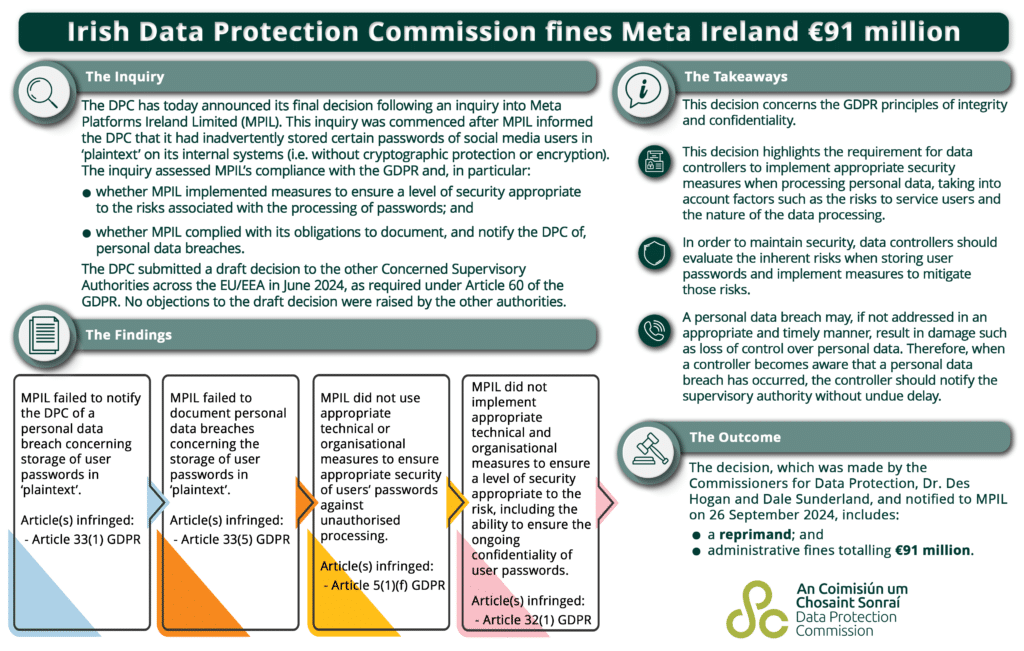
Violation Of GDPR Rules : Meta was Fined $100M For Storing Password In Plaintext
(GDPR )Did You know that , according to the Data Protection Commission, Meta exposed the data of millions of Facebook users by breaking multiple GDPR regulations. In addition to failing to put in place the proper organisational and technical security measures to guard user data against illegal access, DPC Ireland claimed that Meta also neglected …
Violation Of GDPR Rules : Meta was Fined $100M For Storing Password In Plaintext Read More »