Bulletproof Hosting(BPH), Hacker’s illegal Weapon Part 1
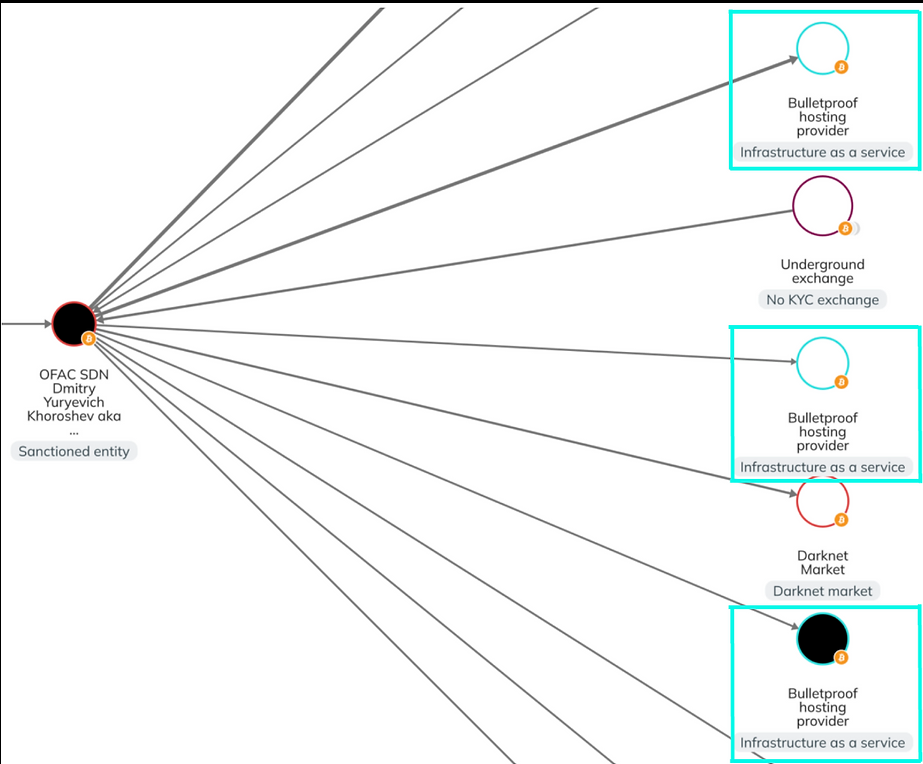
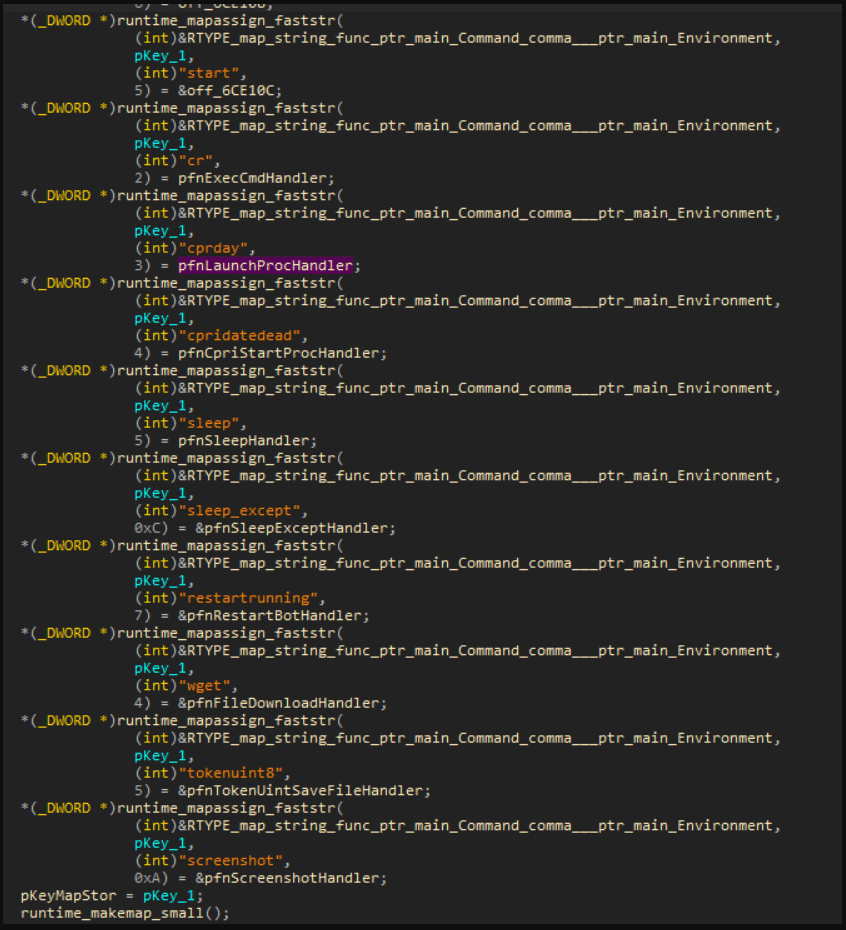
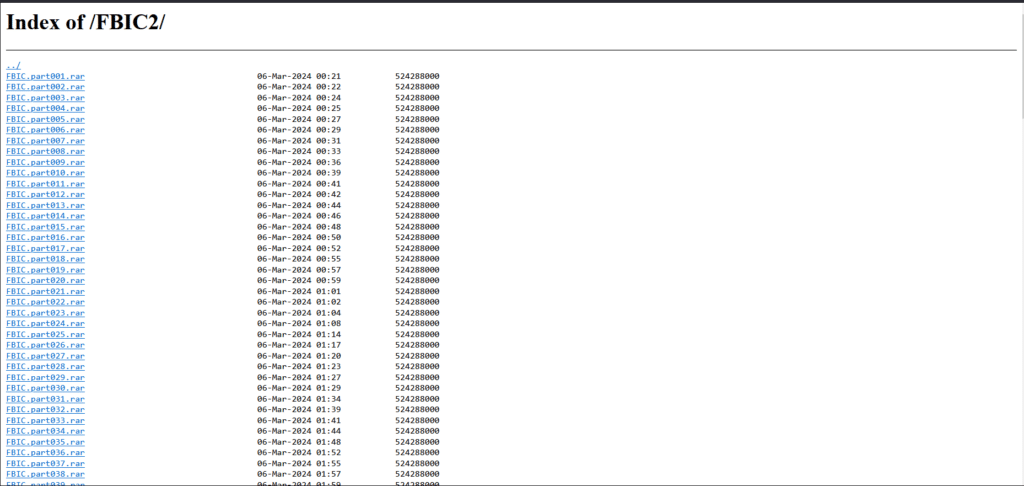
Hackingblogs: Before it is too late, you should learn about bulletproof hosting, or BPH. This technology is being used by hackers worldwide to host illicit marketplaces, distribute malware, and conduct phishing attacks. I will explain this in great detail for you in this post. Why should we care about BPH and what is their role […]
Bulletproof Hosting(BPH), Hacker’s illegal Weapon Part 1 Read More »