Hackingblogs Exclusive : There is a breach at BSNL. This is the second such incidence in the last six months. Let us examine the specification in greater depth.

BSNL is Hacked
The well-known BSNL Bharat Sanchar Nigam Limited, however, suffered a significant data breach due to a malicious actor gaining access to a variety of sensitive information, including the users’ SIM card details, home addresses, registration information, and vital security keys, such as their International Mobile Subscriber Identity (IMSI) Number.
According to the threat actor, BSNL has been compromised. goes by the name KiberPhant0m, and it contains more than 278 GB of data from the official BSNLS telecom operation. Some of the data are snapshots, which might be used for extortion or other serious crimes. The data could even be misused for a million-dollar clone.
This is the state-owned telecom operator’s second data breach in the last six months; the first one was reported by ET in December of last year.

The compromising material, which Gaur describes as Complex and Critical and which goes beyond ordinary user information to target the key operational systems of BSNL, has a 5000$ public prize tag attached to it by the thread actor. The operational data that has been accessed in detail may be utilised to execute more sophisticated cyberattacks. As of the time of publication, BSNL had not responded to any inquiries about this incident.
Gaur highlights the gravity of the situation by saying that attackers might simply get beyond security safeguards on financial accounts with access to SIM card information in authentication credentials, leading in huge financial losses and identity theft for customers.
In order to lessen the impact right away, he also emphasised the significance of auditing access logs and securing network endpoints.
Additionally Gaur stressed the implementation of enhance security measures such as frequent security audits and the adoption of Advanced thread detection technology to prevent similar incidents in the future.
Techniques For Violation
Within a closed Telegram group, KiberPhant0m revealed screenshots and in-depth explanations of a security Bridge, naming the telecom company in question. By taking advantage of a single weak point in the company’s internal infrastructure—a router that granted the hacker root super user privileges—the hacker was able to access the entire network and obtain a significant quantity of data.
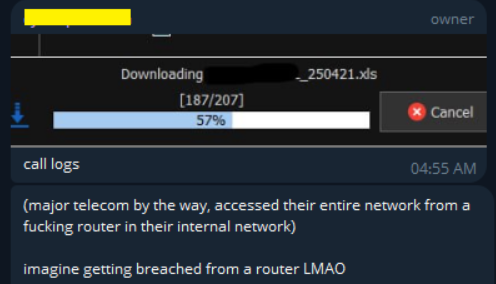
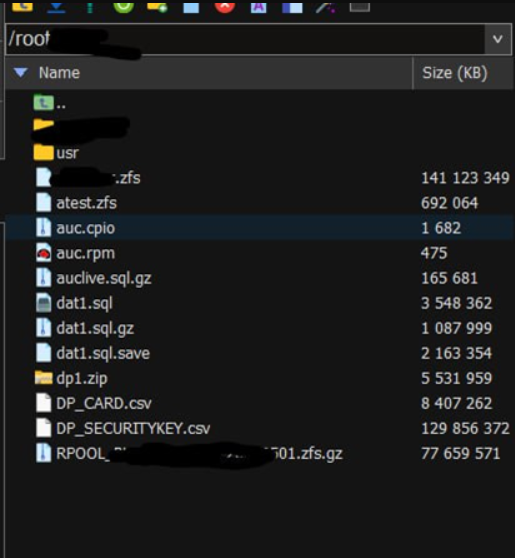
The hacker continues to access and retrieve new data on a regular basis from the bridge, which aggregates records dating back to 2013. This continuous access enables the hackers to continue extracting new information, increasing the effect of the breach.
Frequently Asked Question ?
How did the hacker named “kiberphant0m” gain access to the Asian telecom company’s network?
The hacker gained access through a single compromised router within the company’s internal infrastructure, which allowed for extensive data exfiltration.
What kind of data and network access was compromised in this cyber breach?
The breach included LAN access, decryption library for key integrity, call logs, databases, SIM card cloning capability, national ID information, source code, HLR database access, AUC codes, and more.
How much data was compromised in the breach, and what is the hacker offering for sale?
Over 250 GB of data was compromised, with the potential for up to 1 TB more. The hacker is offering all obtained data, login credentials, root access to machines, and detailed instructions for maintaining network control for a price range of $150,000 to $10,000,000 USD.
How can the identity of the telecom company be disclosed by the hacker?
The identity of the telecom company will only be disclosed upon proof of funds exceeding $150,000 USD.
What cybersecurity measures are recommended in light of this breach?
Regular security audits, advanced encryption techniques, employee training, and incident response planning are recommended to mitigate vulnerabilities and protect against potential threats.
How can organizations safeguard their data and network infrastructure in the digital landscape?
Organizations can safeguard their data and network infrastructure by implementing comprehensive cybersecurity measures, conducting regular security audits, using advanced encryption techniques, providing employee training, and having a robust incident response plan in place.


