Hackingblogs : While actively participating in a bug bounty programme for a global company, @vitooficiall found a significant vulnerability: SQL Injection. Through weak application fields, malicious commands are inserted into a database, enabling unauthorised access or data manipulation.
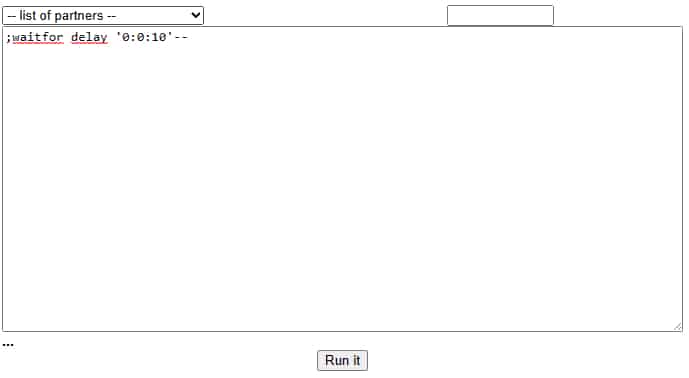
In this instance, a field intended to receive lists of names had the vulnerability. Although it was initially a case of blind SQL Injection, which meant direct data extraction was not possible, they were able to exploit the weakness by introducing malicious commands instead of legal names.
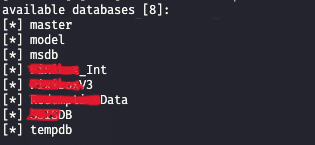
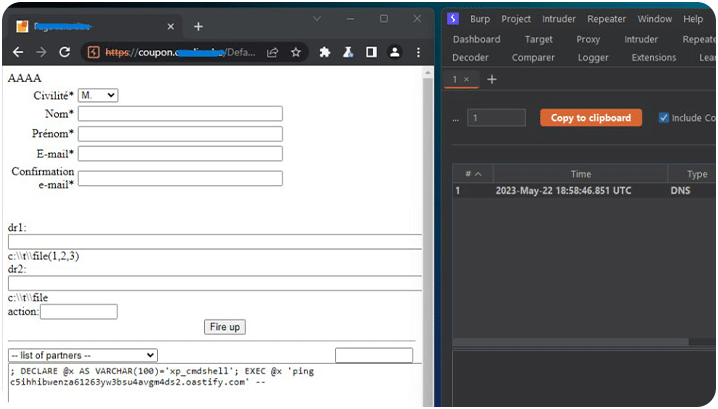
To overcome this limitation, they utilized sophisticated techniques like Time-based SQL Injection and out-of-band methods to successfully extract sensitive information from the company’s databases.
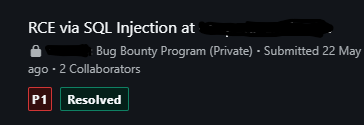
But there objective was to increase the significance of this finding. They worked hard to create a payload that would execute commands directly on the application server, and after a while they were able to accomplish Remote Code Execution (RCE) on the server.
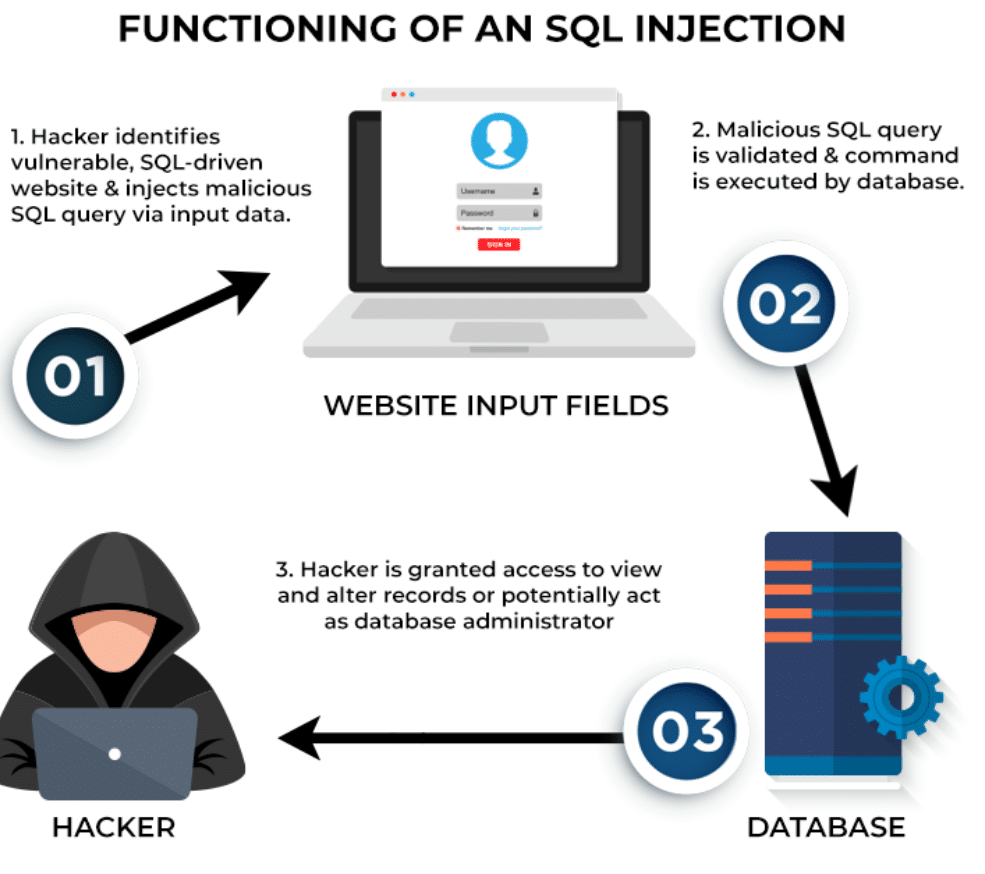
What is Sql Injection
Hackers can use SQL injection to change websites so they can access or manage data kept in databases. They achieve this by infiltrating malicious commands into information-input areas such as search bars and login boxes. Data security requires developers to provide code that prevents these threats.
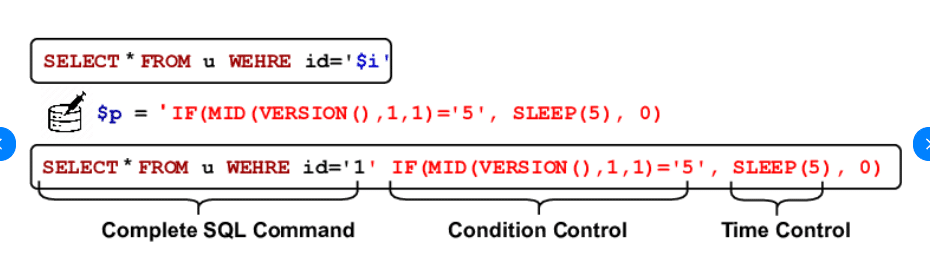
What is Time Based Sql Injection
When an application does not show the attack’s results right away, hackers can still retrieve data from a database by using a technique called time-based SQL injection.
A website or app that communicates with a database—for example, when you log in or search for products—often sends queries to the database to obtain data. Hackers utilise these queries’ vulnerabilities to their advantage by introducing unique commands that delay the database’s response.
Rather than merely requesting product details, they may, for instance, inject a command telling the database to hold off on answering for a little while. Through measuring the response time of the website, hackers can determine the success or failure of their injected order.
Even in cases when the website does not explicitly display the findings, hackers can still obtain information indirectly by using this strategy. Developers need to create secure code that prohibits arbitrary commands from altering database queries in order to prevent time-based SQL injection.
What is Remote Code Execution
An important cybersecurity flaw known as remote code execution (RCE) allows attackers to take control of a computer or server remotely and execute commands, giving them unauthorised access.
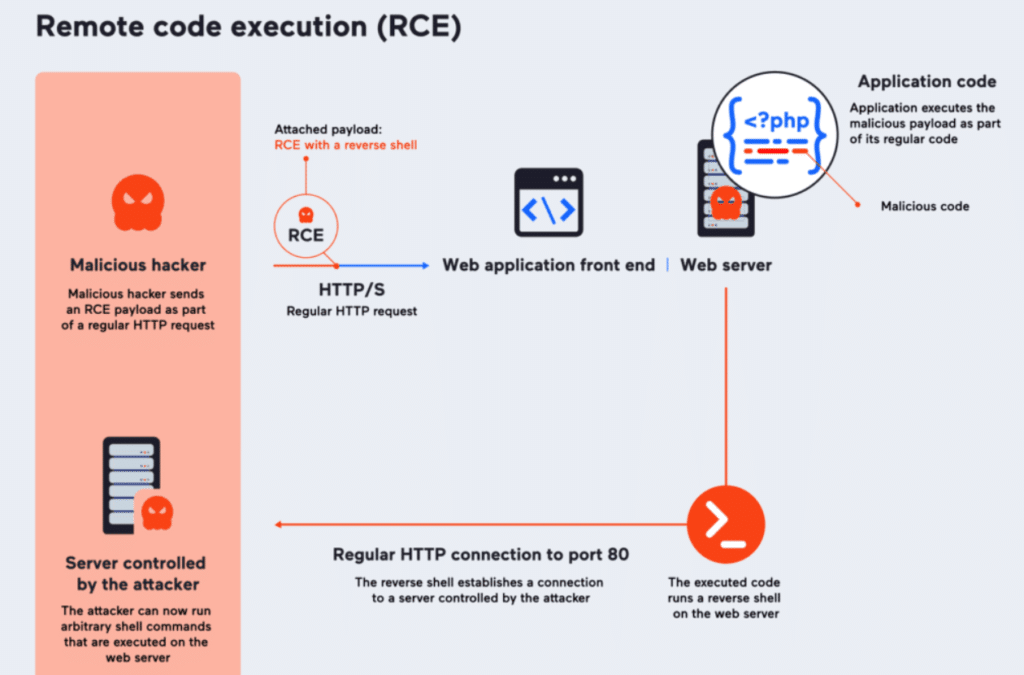
Security mechanisms, or “doors,” are built into computers and servers to keep out unauthorised users. Remote Code Execution (RCE) occurs when cybercriminals manage to get past these barriers and transmit commands that allow them to take control of the server or machine as if they were literally there.
To ensure that unauthorised commands cannot penetrate and take over their systems, developers must erect robust defences against RCE, such as frequent software updates and the use of security tools.
Conclusion
This big hack serves as a reminder of how crucial thorough security testing and timely vulnerability disclosure are. They made sure the business could quickly address and mitigate these vulnerabilities by reporting our discoveries to the bug bounty programme right away.
Frequently Asked Quetions
What is SQL injection?
SQL injection is a cyber attack where malicious commands are inserted into a website or application’s input fields to manipulate the underlying database, potentially gaining unauthorized access to sensitive information.
How does SQL injection work?
Hackers exploit poorly secured input fields (like login forms or search bars) by inserting SQL commands that trick the database into executing unintended actions, such as revealing data or even allowing control over the database.
What is time-based SQL injection?
Time-based SQL injection is a technique where attackers manipulate the response time of database queries to infer whether their injected commands were successful. This is used when direct data extraction isn’t possible through traditional methods.
What is Remote Code Execution (RCE)?
Remote Code Execution is a security vulnerability that allows attackers to execute commands on a system or server from a remote location. It can lead to unauthorized access and control over the affected system, similar to a digital break-in.
How does Remote Code Execution happen?
RCE occurs when hackers exploit weaknesses in software or applications, sending malicious commands remotely to bypass security measures and gain control over the targeted system.
How can developers prevent SQL injection attacks?
Developers can prevent SQL injection by using secure coding practices, such as parameterized queries, input validation, and sanitization of user inputs to ensure that no malicious SQL commands can be executed.
What are the consequences of SQL injection attacks?
SQL injection attacks can lead to unauthorized access to sensitive information (like usernames, passwords, or financial data), data manipulation, and even compromise of entire databases, resulting in financial losses and damage to reputation.
How can websites protect against Remote Code Execution?
Websites can protect against RCE by keeping software and applications updated with the latest security patches, using web application firewalls (WAFs), implementing strict access controls, and conducting regular security audits.
What are the signs that a website or application may be vulnerable to SQL injection?
Signs of SQL injection vulnerability include unexpected errors when entering certain characters in input fields, unusually slow response times, and unauthorized access to sensitive information through seemingly harmless user inputs.
Why is cybersecurity important for businesses and individuals?
Cybersecurity is crucial for protecting businesses and individuals from data breaches, financial losses, and reputational damage. It ensures the confidentiality, integrity, and availability of sensitive information in an increasingly digital world.


