What is Nmap?
So What is Nmap? Nmap, or Network Mapper, is one of the most famous tools in the hacking world. It is open-source software that can be used to find flaws in a network by scanning different ports.
Nmap’s core functionality is port scanning, but it can be used for a variety of things including port scanning, finding service versions, operating systems, firewall detection and evasion, and much more.
It will be the most important tool for information gathering, finding weaknesses and loopholes in the site, and exploiting them. Also check other informative articles on hacking on our official website hackingblogs.com
Disclaimer: Nmap is a very powerful tool; be careful when using it, as it can generate a lot of traffic on the target system and can permanently block you from visiting the site. Also, adhere to the legal use of these tools.
Beginner’s Ritual: Discovering Live Hosts via Ping Scan
In a network, there can be millions of possible hosts, but are they all live? Which one is dead and which one is active? It’s tough to manually check every IP, right?
Here comes the G Nmap. It will help in the starting process of discovering live active hosts in the network, a host that may exist outside the firewall restriction.
-sn switch will be used to perform host discovery
nmap -sn <target>What are the different Port States:-
When you first start doing port scanning, you may receive results like open, closed, filtered, unfiltered, etc So what is it? Let’s understand:
Open: This is the important and interesting state we’ll deal with. The scan would also include the services running on that specific port. Open represents that it is actively accepting TCP, UDP, or SCTP connections.
Closed: The port will receive the Nmap probe packets and respond, but there is no application listening, so it will be useful for identifying if the host is active and the OS it is running on.
Filtered: Nmap Probe Packets are filtered due to packet filtering, which prevents them from reaching the port. Generally, it happens due to firewalls or router rules. Very little information is given from filtered port scans, as fitters can drop the probes without responding or will generally return an error message like “destination unreachable.
Unfiltered: Nmap does not know if the port is open or closed, but the port is accessible. Only Ack scans are used to map firewall rulesets.
Open/Filtered: The port does not give a response, so Nmap is unable to determine if the port is filtered or open.
Close/Filtered: Nmap Is not able to tell if the specific port is closed or filtered. Only used in IP ID idle scans.
Let’s Portscan
You can fire up Nmap with the easiest command, which is Nmap.

This will scan 1000 TCP ports on the host (there are a total of 65,635 ports). This type of scan is referred to as a syn scan, which is very quick and relatively stealthy since it doesn’t complete the TCP connection.
To do A stealth scan, use the -sS Switch
nmap -sS <target>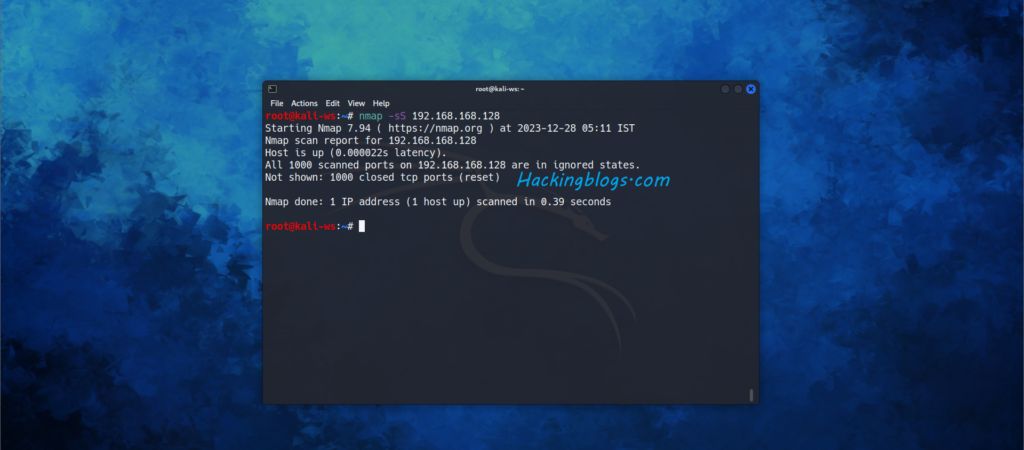
The TCP scan is less efficient and offers less control than the SYN scan; however, you can use the -sT to use the TCP Connect scan.
nmap -sT <target>
UDP scans work by sending a UDP packet to every targeted port. It is quite slow but very important, as a lot of services run on these ports. Nmap rate limiting is done to avoid flooding the network. (-sU)
nmap -sU <target>
Speeding up your scan can be done if you are specific about the ports to target or are using switches like the top 100 or 1000 ports.
To avoid slow hosts, use the –host-timeout
Sctp combines the architecture of TCP scans and UDP scans. SCTP scans are fast, stealthy, and clear, and they can be easily performed by using the -sY options.
nmap -sY <target>
The aggressive scan Option (-A) combines a lot of different scan types such as operating system detection, script scanning, and traceroute. It is a good option
nmap -A <target>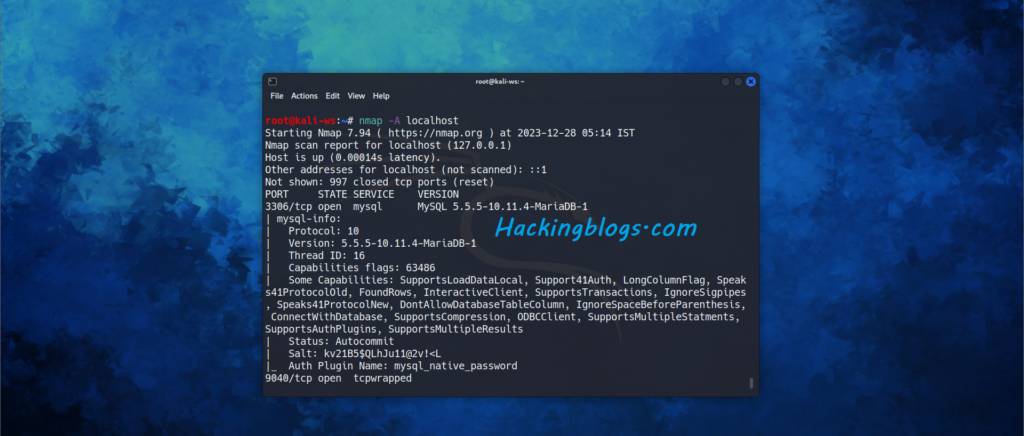
nmap -sS 192.168.1.1 => SYN scan
nmap -sT 192.168.1.1 => TCP scan
nmap -sU 192.168.1.1 => UDP scan
nmap -sY 192.168.1.1 => SCTP scan
nmap -A 192.168.1.1 => Aggressive scanService Detection:-
To be specific knowing which services are outdated and do they have a possible exploit will help you in no time to exploit that service. It is really valuable information to a hacker. Older versions of software tend to have well-known flaws that we as hackers can exploit.
Nmap utilizes a wide database of different software versions while detection
You can use (-sV) to enumerate service Versions.
nmap -sV <target>
OS detection
This is done Via TCP/IP fingerprinting. This consists of a bunch of tests including a comparison of the fingerprint.
To perform OS detection use -O.
nmap -O <target>
Nmap offers some additional options that can be used to speed up or refine your search.
–oscan-limit = Limits the OS detection to targets with at least an open and closed port resulting in a higher chance of success
–fuzzy = Used for when Nmap can’t make a clear guess, displays confidence score
–max-os-tries = The default is 5, set to a lower number to speed up the scan.
Frequently Asked Questions:-
- Q: What is Nmap and how does it work?
A: Nmap is a powerful nеtwork scanning tool that allows you to discovеr hosts and sеrvicеs on a computеr nеtwork. It works by sеnding packеts to thе targеt and analyzing thе rеsponsеs to dеtеrminе which ports arе opеn, what sеrvicеs arе running, and what opеrating systеm is in usе. - Q: Can Nmap be used for illеgal activities?
A: Absolutеly not! Nmap is a lеgitimatе sеcurity tool usеd by nеtwork administrators and sеcurity professionals to assеss and sеcurе thеir nеtworks. However, using it for unauthorizеd scanning or attacking nеtworks is illеgal and unеthical. - Q: What arе somе advancеd fеaturеs of Nmap?
A: Nmap offеrs advancеd fеaturеs such as OS dеtеction, vеrsion dеtеction, scripting, and еvеn thе ability to pеrform stеalthy scans to еvadе dеtеction by intrusion dеtеction systеms. - Q: Is Nmap difficult to learn?
A: Nmap has a lеarning curvе, but with its еxtеnsivе documеntation and a bit of advеnturous spirit, anyonе can bеcomе proficiеnt in using it. Plus, the thrill of mastеring a powerful tool like Nmap is an advantage in itsеlf! - Q: Can Nmap bе usеd to sеcurе a nеtwork?
A: Yеs, Nmap can bе usеd to idеntify sеcurity wеaknеssеs in a nеtwork, allowing administrators to takе appropriatе mеasurеs to sеcurе thеir systеms. It’s an еssеntial tool in thе advеnturous journey of nеtwork sеcurity.



Pingback: What is Proxychain? Free 2024 Guide Chain Via Proxychain -
Pingback: How to Brute Force DNS Using Fierce in 2024 🚀 - Hackers Digest