Hackingblogs : A critical vulnerability was found (CVE-2024-38428) on wget a linux command line tool. This Vulnerability has CVSS Base core of 10.0 which is indeed very high.

Because to a major vulnerability that allows attackers to carry out unspecified attacks, CERT-Bund recommends users of wget versions <=1.24.5 to take immediate action. Users of wget on Linux or Windows are advised to stop using the programme until an updated version is issued.
CVE-2024-38428
Understanding what is Wget ?
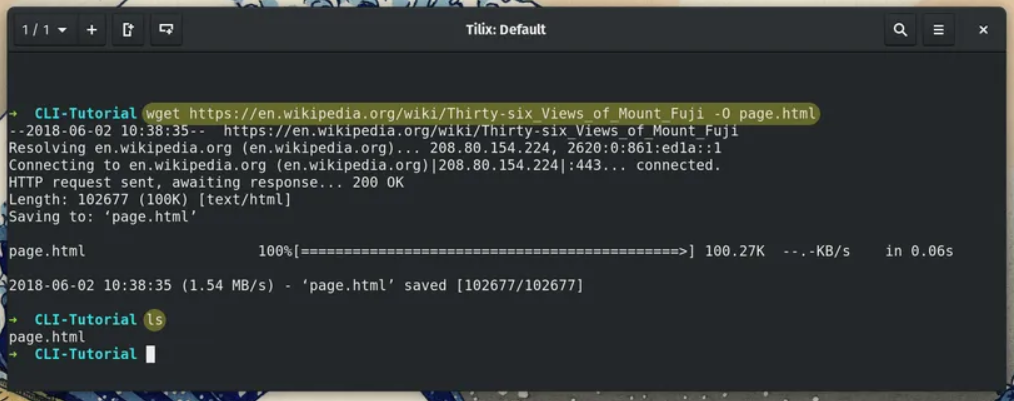
Wget is a linux command line tool which is free and open source by the GNU Project helping users to dowload files using the linux terminal.The wget tool supports http and https and ftp. It is a non-interactive command line tool that may be used in contexts like cron jobs and terminals that do not support X-Windows, and it can be simply integrated into scripts and scheduled processes.
A high Severity Vulnerability was found. The German Cert-Bund declared about a critical flaw was found on wget on June 17,2024.This flaw detected has a very high severity of rating 10.0.
Nist Description
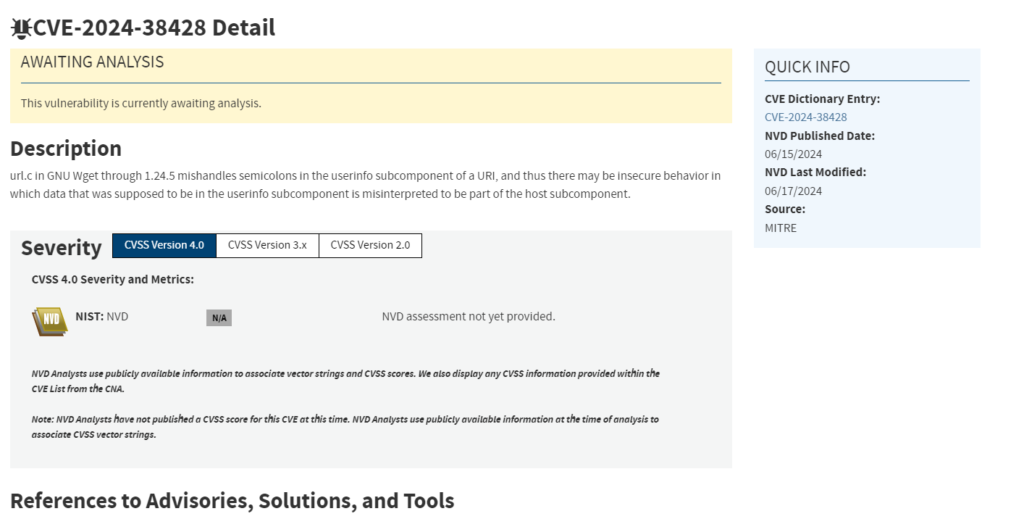
The Nist Describes the flaw as the following “url.c in GNU Wget through 1.24.5 mishandles semicolons in the userinfo subcomponent of a URI, and thus there may be insecure behavior in which data that was supposed to be in the userinfo subcomponent is misinterpreted to be part of the host subcomponent.”
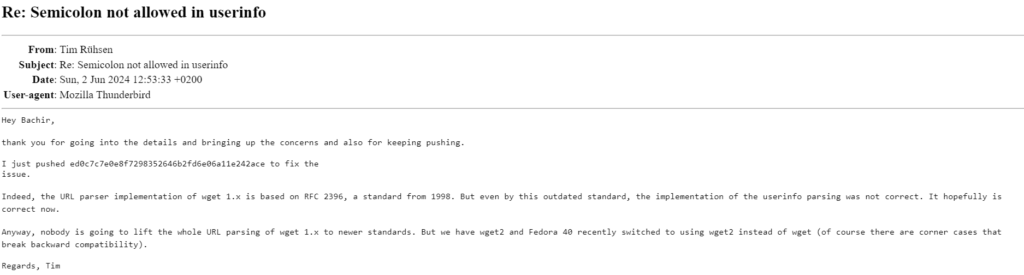
Tim Rühsen Mentions :
“I just pushed ed0c7c7e0e8f7298352646b2fd6e06a11e242ace to fix the issue.
Indeed, the URL parser implementation of wget 1.x is based on RFC 2396, a standard from 1998. But even by this outdated standard, the implementation of the userinfo parsing was not correct. It hopefully is correct now.
Anyway, nobody is going to lift the whole URL parsing of wget 1.x to newer standards. But we have wget2 and Fedora 40 recently switched to using wget2 instead of wget (of course there are corner cases that break backward compatibility“
Versions afftected Via this flaw
All the GNU Wget version up to 1.24.5 is flawed that is incorrectly handling the semicolons in the userinfo subcomponent of a url.
Consequence:
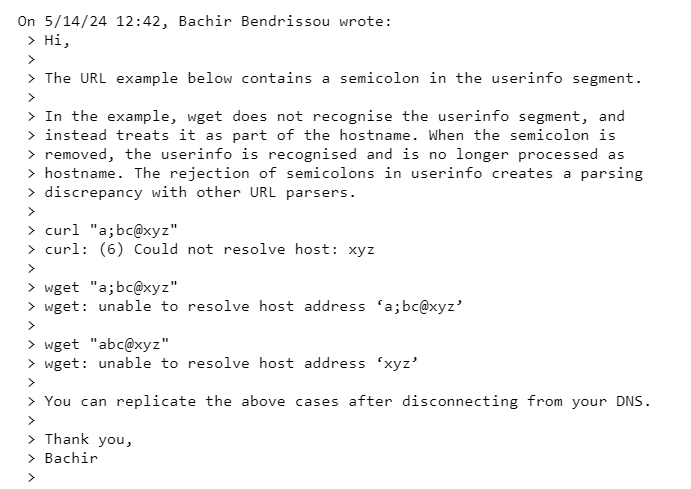
Because of this problem, data that should be saved in the userinfo subcomponent may be incorrectly viewed as part of the host subcomponent, which could lead to potentially harmful behaviours. The defect was discovered on June 2, 2024, and Tim Rübsen goes into detail about it in a post on the gnu.org mailing list titled Re: Semicolon not allowed in userinfo.
Potential Threat that the flaw brings
First off, the way wget 1.x currently operates deviates from the RFC 3986 URI standard, which permits semicolons in the userinfo section. Maintaining adherence to this extensively recognised standard is crucial for both interoperability and correctness.

Because of the way wget 1.x handles semicolons in the userinfo segment of a URL, there could be security flaws that allow sensitive data to leak, phishing and spoofing attacks via host header manipulation, and man-in-the-middle attacks caused by improper DNS resolution.
Frequently Asked Questions
Q1: What is CVE-2024-38428?
A1: CVE-2024-38428 is a particular vulnerability diagnosed within the wget utility, a popular command-line device used for downloading files from the internet.
Q2: How does CVE-2024-38428 have an effect on wget customers?
A2: This vulnerability can probably be exploited by means of malicious actors to execute arbitrary code or perform other unauthorized moves on a user’s device.
Q3: Who determined CVE-2024-38428?
A3: The CVE-2024-38428 vulnerability became recognized through security researchers who concentrate on identifying and reporting software program vulnerabilities.
Q4: Can CVE-2024-38428 be patched?
A4: Yes, the builders of wget have released a patch to deal with this vulnerability. Users are recommended to replace their version of wget to the cutting-edge release to mitigate the chance of exploitation.
Q5: Are all versions of wget affected by CVE-2024-38428?
A5: No, handiest sure variations of wget are liable to CVE-2024-38428. Users ought to test with the legitimate wget website or their package deal supervisor for records on which variations are affected.
Q6: What steps can customers take to protect themselves from CVE-2024-38428?
A6: Users need to replace their model of wget to the ultra-modern release, often test for security updates, and workout warning whilst downloading documents from untrusted resources.
Q7: Can CVE-2024-38428 be exploited remotely?
A7: Yes, CVE-2024-38428 can doubtlessly be exploited remotely through an attacker who sends a mainly crafted request to a vulnerable version of wget.
Q8: Are there any recognised instances of CVE-2024-38428 being exploited in the wild?
A8: As of now, there had been no mentioned instances of CVE-2024-38428 being exploited within the wild. However, it’s miles essential for customers to take precautions to defend themselves.
Q9: What are the ability results of CVE-2024-38428 being exploited?
A9: If CVE-2024-38428 is correctly exploited, an attacker could gain unauthorized access to a user’s machine, installation malware, scouse borrow sensitive records, or perform other malicious movements.
Q10: Where can customers locate greater facts approximately CVE-2024-38428 and its impact?
A10: Users can confer with the legitimate CVE database, security advisories from the wget builders, and official cybersecurity websites for greater statistics on CVE-2024-38428 and the way to shield themselves.


