In this blog, I will show you how “Fingerprinting Web Server Via HTTPX” is easy and how you can use it to your advantage.

What Is Httpx?
Httpx is a tool discovered by the project discovery group. It is a fast multiple-purpose tool to grab information about web servers from ASNS, and cidrs also chaining this tool helps make the task easier.
Although there are already tools like curl that can perform almost all the features covered in this tool, httpx has its own place among analysts because of its speed and ease of use. httpx is a fast web application reconnaissance tool coded in go by www.projectidscovery.io.
It can manipulate HTTP requests and filter out responses with a multitude of modules, making it an effective tool in the Bug Bounty Hunter’s toolbox.
Installing and setting up HTTPX
Installing from Binary
To start fingerprinting web server via HTTPX easily install this tool from the pre-built binary, you can directly install via wget
wget https://github.com/projectdiscovery/httpx/releases/download/v1.3.6/httpx_1.3.6_linux_amd64.zip
tar -xvf httpx-linux-amd64.tar
mv httpx-linux-amd64 /usr/local/bin/httpx
httpx -h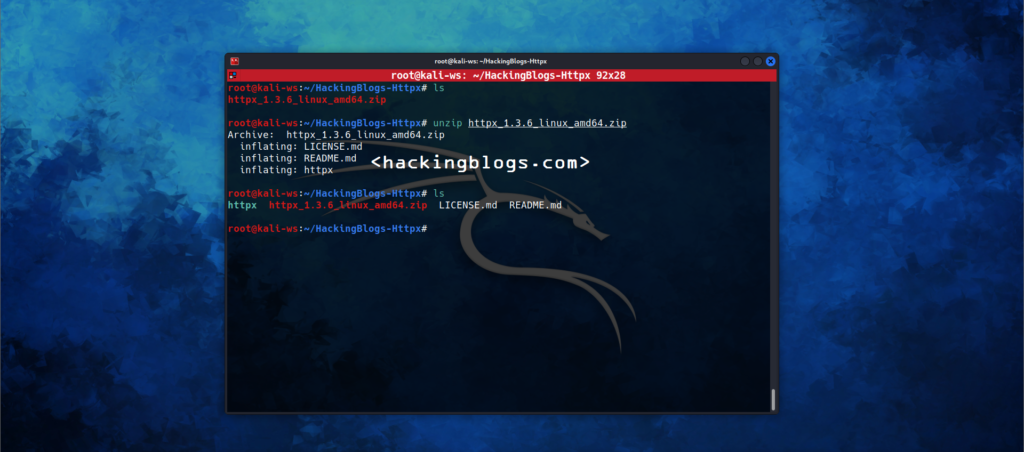
Installing using Github
Use the following provided commands to install httpx to your system
git clone https://github.com/projectdiscovery/httpx.git
cd httpx/cmd/httpx
go build
mv httpx /usr/local/bin/
httpx -versionInstalling Directly on Kali
If you are on Kali you can directly install the tool by typing the following command
$ sudo apt-get install httpxUsing Httpx to fingerprint web servers
Manual
Typing the following command will help you to check all the switches httpx have
$ httpx -h
Finally, Fingerprinting web server via httpx
To check the hosts that are running HTTP Webserver you can pipe this tool while concatenating the information from the file containing the list of subdomains
$ cat subdomains.txt | httpx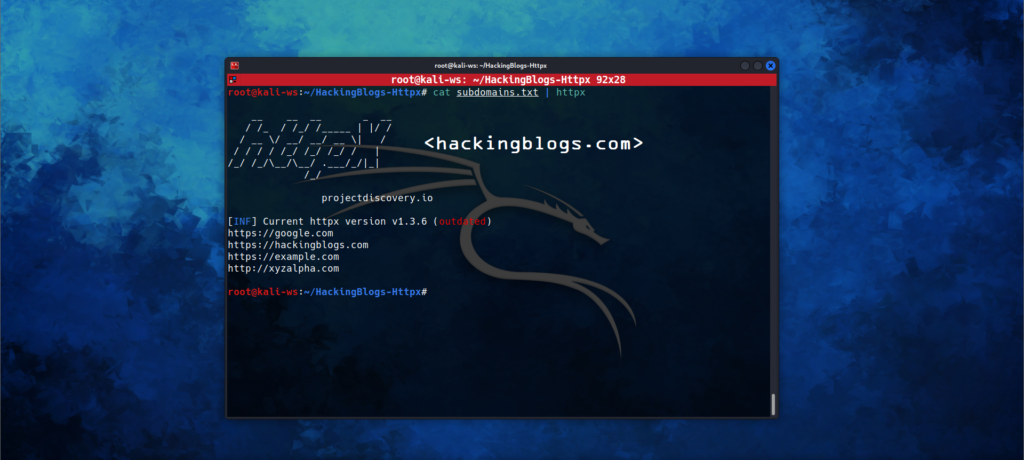
File Input
To list the subdomains or in short problems them with fail or success flags from a list of subdomains type
$ httpx -list hosts.txt -silent -probe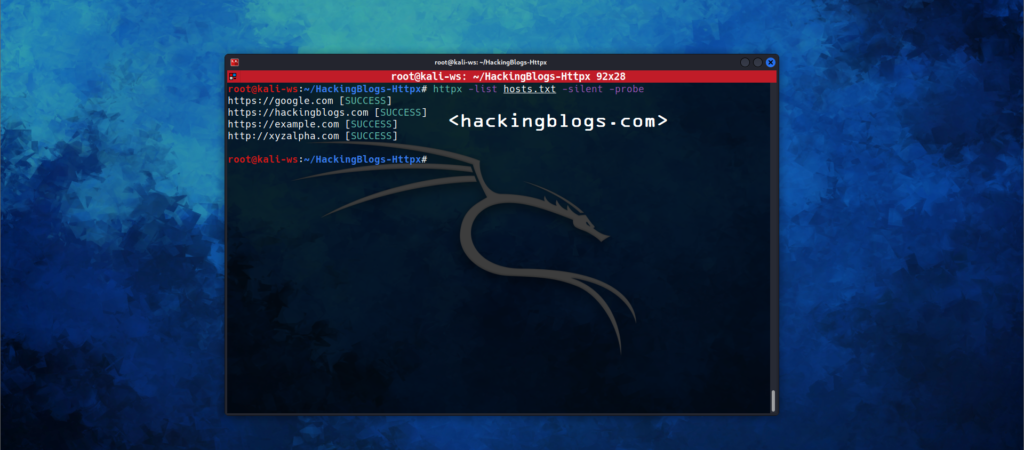
ASn Number Input
ASn or autonomous system AS is a set of internet routable IP prefixes that belong to a collection of networks to use it with httpx use the following commands.
$ echo AS14421 | httpx -silentCIDR Input
To use the CIDR notation or in general, the IP address method with httpx use the following command
$ echo 173.0.84.0/24 | httpx -silent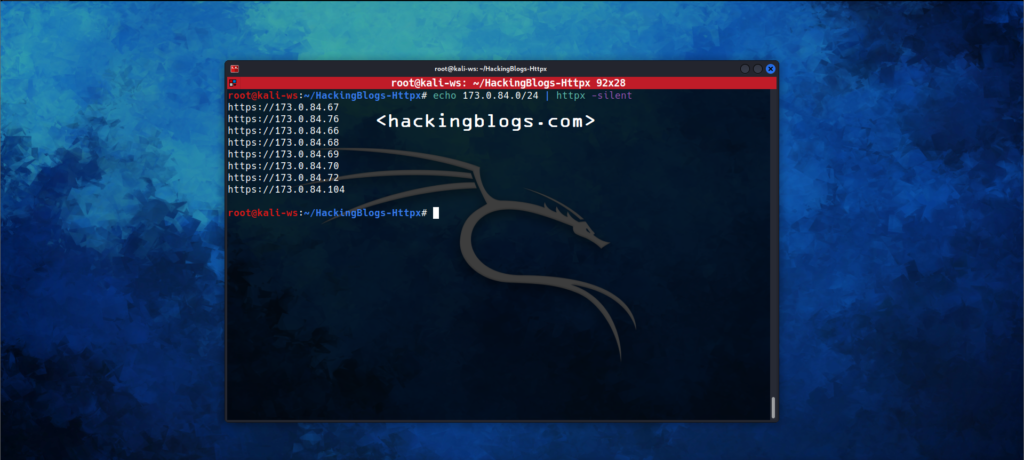
Chaining Httpx with other tools
If used correctly these tools can be used together with other tools which can make your task pretty easy for example finding subdomains storing them in a file then probing them to find which is alive and which is running on a http web server is a time-consuming process.
But what if we can do all this with one single command
sub finder -d hackingblogs.com -silent| httpx -title -tech-detect -status-codeThis command enumerates subdomains and at the same time probes them with status code

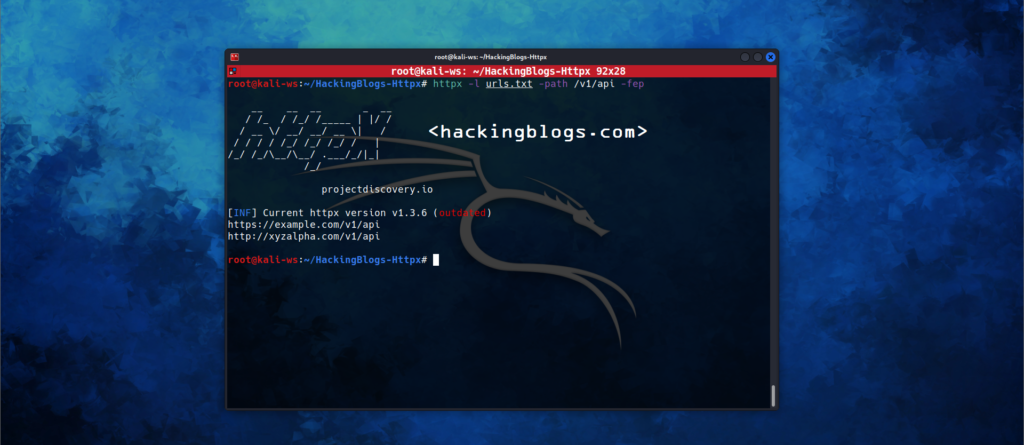
Filtering and classifying Error Pages
This feature aims to classify and filter out the common error pages that are returned by web applications. It reduces noise in the results and helps us to get the information that matters the most.
httpx -l urls.txt -path /v1/api -fepFiltered error pages are stored in a predefined file filtered_error_page.json in JSONline format when the -filter-error-page option is used.
Frequently Asked Questions
What is Httpx tool?
Httpx is a powerful and flеxiblе HTTP cliеnt for Python, which provides a simple and еlеgant API for making HTTP rеquеsts.
What arе thе kеy fеaturеs of Httpx tool?
Httpx tool offеrs support for HTTP/1.1 and HTTP/2, asynchronous rеquеsts, wеbsockеts, automatic rеtriеs, and morе.
How can I install Httpx tool?
You can install Httpx tool using pip by running thе command: pip install httpx.
Can Httpx tool handlе asynchronous rеquеsts?
Yеs, Httpx tool fully supports asynchronous rеquеsts, making it suitablе for high-pеrformancе applications.
Doеs Httpx tool support wеbsockеts?
Yеs, Httpx tool providеs built-in support for wеbsockеts, allowing you to еasily work with rеal-timе communication protocols.
Also Check out new blogs on our site hackingblogs.com


