Gobuster For Hackers
In the realm of web security assessments, enumerating files and directories of a web server marks the initial step towards identifying potential vulnerabilities. Gobuster, renowned for its speed and efficiency, emerges as a go-to tool for this purpose. In this guide, we will delve into the usage of Gobuster For Hackers, exploring its functionalities and nuances.
Installing Gobuster
To harness the power of Gobuster, begin by installing it on your Linux machine. If you’re using Parrot OS, Gobuster is likely already installed. However, for other Linux distributions, execute the following command in the terminal:
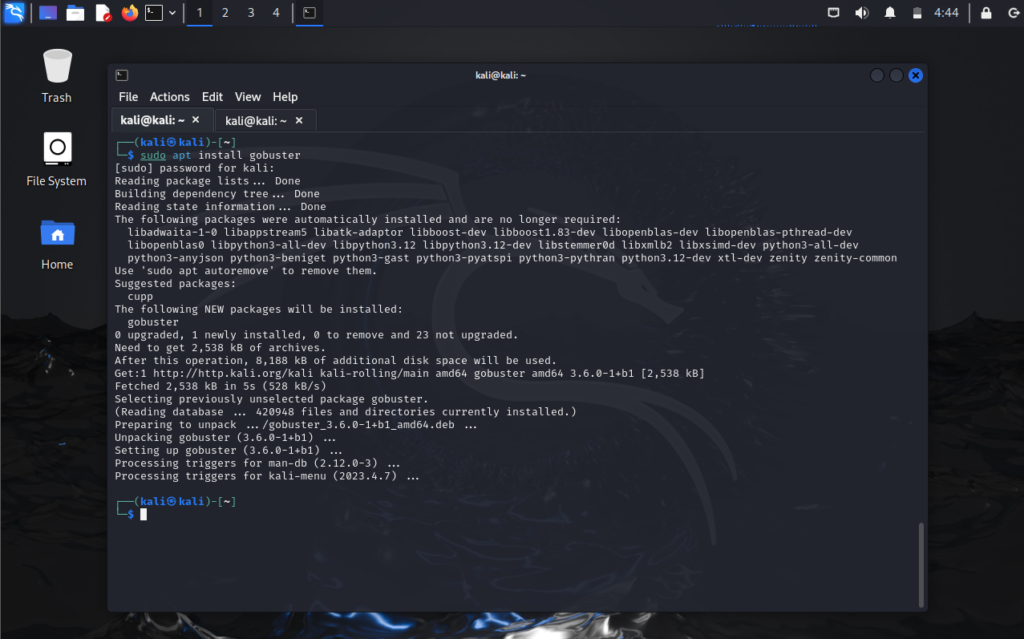
sudo apt install gobusterOnce installed, verify the installation by typing gobuster in the terminal.
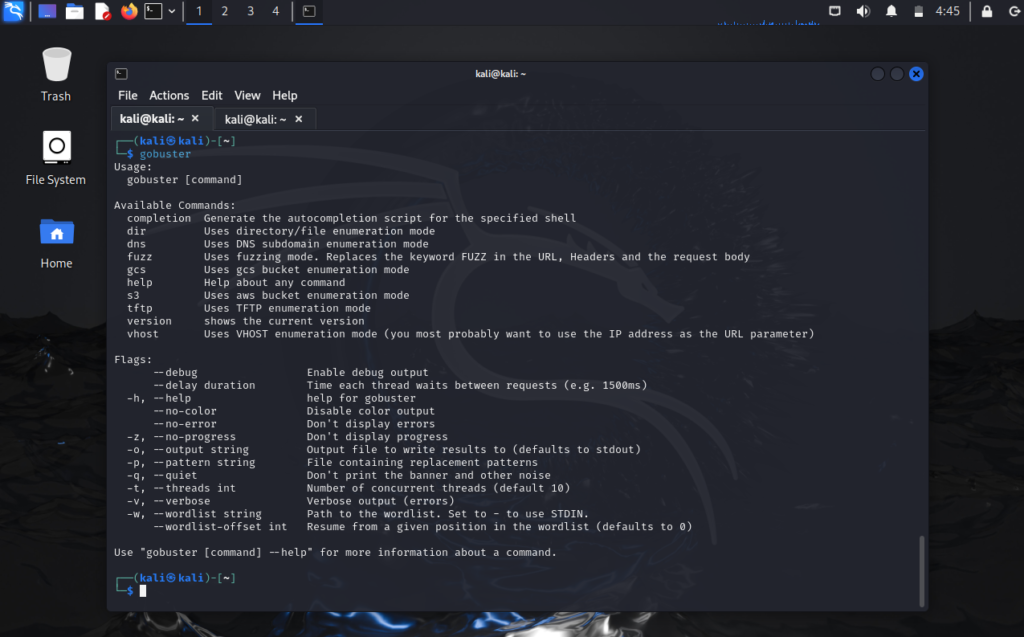
~# gobusterAdding an Additional Wordlist
While Gobuster comes with pre-installed wordlists, adding an extra one can enhance your enumeration capabilities. Let’s install a common wordlist from GitHub:
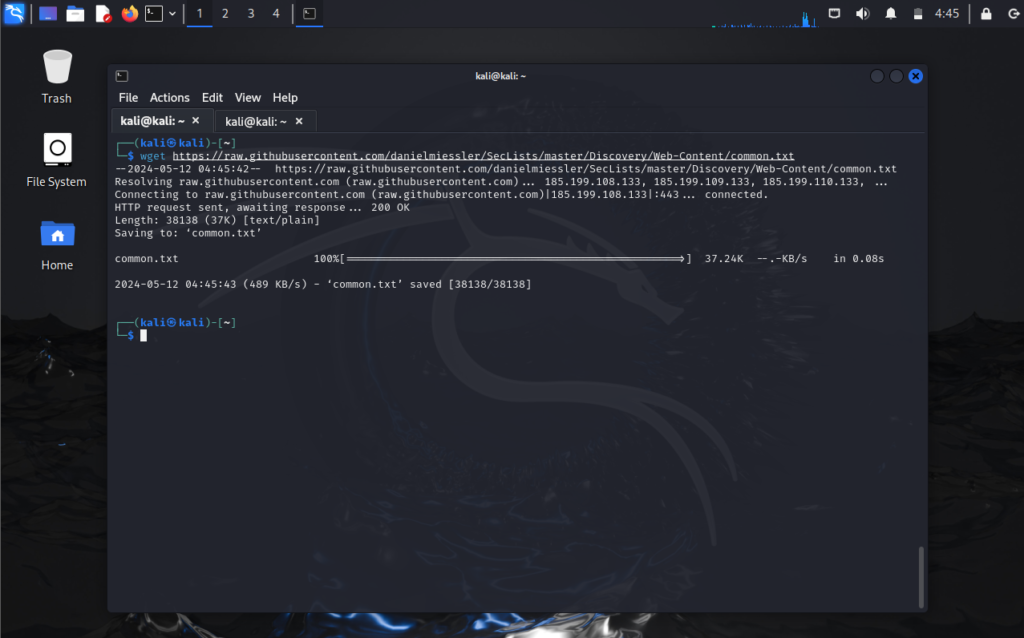
~# wget https://raw.githubusercontent.com/danielmiessler/SecLists/master/Discovery/Web-Content/common.txtWeb Enumeration
Now, let’s delve into web enumeration using Gobuster. Begin with a simple scan on a target website using the common wordlist:
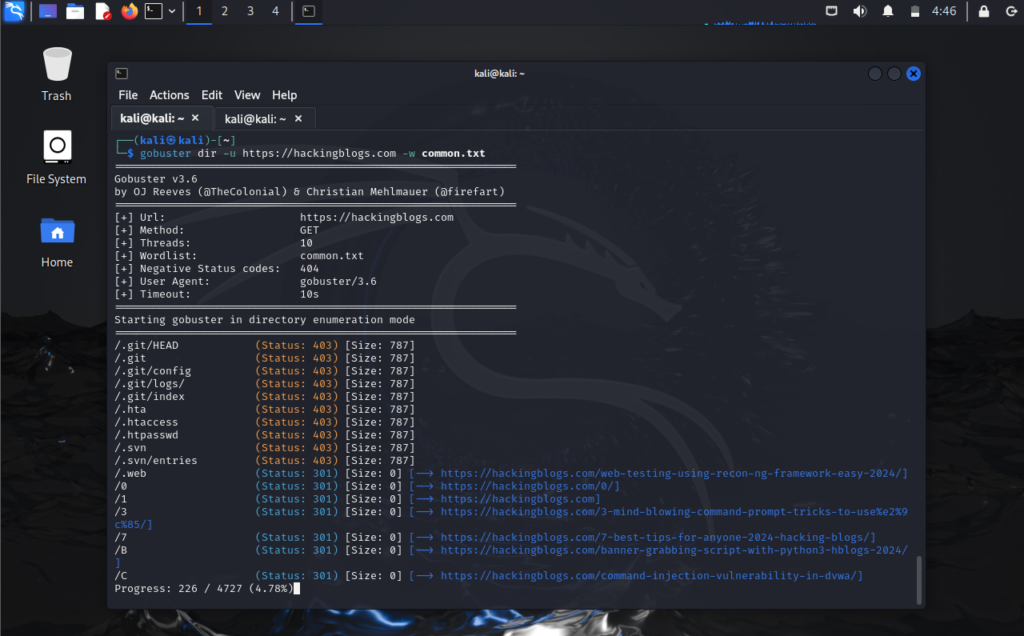
gobuster dir -u http://hackingblogs.com -w common.txtFiltering Results for Efficiency
For larger websites, filtering results based on specific status codes can save time and streamline the enumeration process. For example:
gobuster dir -u https://hackingblogs.com/category -w common.txt -s 200,301This command filters results to display only status codes 200 (OK) and 301 (Moved Permanently), omitting zero-byte responses and irrelevant data.
Tips for Beginners
It is best for novices to begin with smaller websites in order to understand the subtleties of Gobuster’s work. Playing around with your own website can reveal important details about the enumeration procedure. Recall that the process of learning is just as significant as the final goal.
Conclusion
To sum up, Gobuster For Hackers is a strong ally in the field of web enumeration since it provides speed, effectiveness, and customisable settings. Cybersecurity aficionados can improve their comprehension of web security landscapes by using Gobuster’s ability to find potential flaws and secret channels. When you set out on your adventure with Gobuster, do not forget to experiment, explore, and most of all, relish the learning process.
Using a methodical approach that includes installation instructions, web enumeration methods, filtering tactics, beginner’s advice, and a closing note, this tutorial seeks to provide readers with the skills and resources required to do efficient web enumeration using Gobuster.
Frequently Asked Questions
- What is Gobuster?
Gobuster is a command-line tool used for directory and file brute-forcing on web applications. - How do I install Gobuster?
You can install Gobuster by downloading the binary from the official website or by using package managers like apt or brew. - What are some common options used with Gobuster?
Some common options used with Gobuster include -u for specifying the target URL, -w for specifying the wordlist, -t for setting the number of concurrent threads, and -q for running in quiet mode. - How do I perform directory brute-forcing with Gobuster?
To perform directory brute-forcing with Gobuster, you can use the command “gobuster dir -u [target_url] -w [wordlist]”. - Can Gobuster be used for file brute-forcing as well?
Yes, Gobuster can be used for both directory and file brute-forcing. You can use the command “gobuster -u [target_url] -w [wordlist] -x [extensions]” to search for specific file types. - How can I customize the output format of Gobuster?
You can customize the output format of Gobuster using the -o flag followed by the desired output file path. For example, “gobuster -u [target_url] -w [wordlist] -o output.txt”. - Is Gobuster compatible with different web servers?
Yes, Gobuster is compatible with various web servers like Apache, Nginx, and IIS, making it a versatile tool for web application testing. - Can Gobuster be used for finding hidden directories on a website?
Yes, Gobuster is commonly used for finding hidden directories and files on web applications by brute-forcing different paths. - What are some potential risks of using Gobuster?
Using Gobuster to brute-force directories and files without authorization can lead to legal consequences and may violate the terms of service of the targeted website. - How can I ensure responsible use of Gobuster for ethical hacking purposes?
To ensure responsible use of Gobuster for ethical hacking purposes, always obtain proper authorization before performing any tests on a web application and adhere to legal and ethical guidelines.