Hey there amazing Hackers! In this guide, i’ll walk you through the basics of DNS brute force and subdomain enumeration using two awesome tools – Fierce and Nmap. Do not worry if you don’t know how to use this tool i have made detailed guide on using Nmap and the rest will be covered using this blog

Setting up Your Environment for hacking
Let’s first ensure that we have the necessary utilities installed on our systems. Open your hacking terminal and let’s get started!
# To Install Nmap
sudo apt-get update
sudo apt-get install nmap
Clone SecLists repository (We will be utlising this for Brute Force)
git clone https://github.com/danielmiessler/SecLists.git
Understanding DNS Brute Forcing
So what is DNS brute forcing ??
DNS brute forcing is like trying to guess hidden website addresses. We use long word lists to help us guess or in terms of hacking brute force these addresses. Seclists(folder in seclist), which is found in SecLists, is a great collection for our brute forcing. Let’s clone it:
Using Nmap for DNS Brute Forcing
Nmap is a versatile tool. We’ll use it for DNS brute forcing for more in depth knowledge of nmap checkout this blog on Nmap:
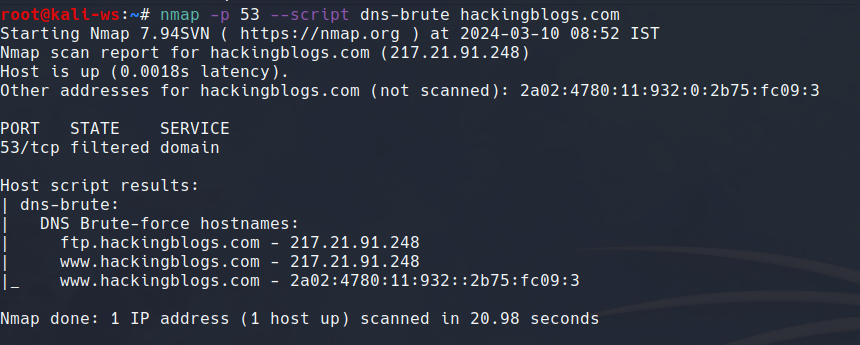
# Run Nmap DNS brute force (replace <domain> with your target domain)
nmap -p 53 --script dns-brute <domain>
Nmap will try to guess subdomains for you the dns-brute script is one of the scripts from the nmap-scripting engine later i will teach you how to design your own scipts via NSE
Subdomain Enumeration with Fierce
Fierce is utlised when you want to bruteforce subdomain this tools comes very handy especially when you are doing recon on your target. Let’s give it a try:
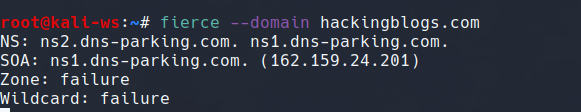
# Run Fierce (replace <domain> with your target domain)
fierce -dns <domain>
Fierce will automatically check for all zone transfers(click the link if you dont know what is zone transfer) and lists subdomains.
Practical Tips to note when you do someting similar
- Word Lists: Always use good word lists like SecLists for effective brute forcing.
- Tool Alternatives: Experiment with DNS Map. It’s a handy tool for subdomain enumeration as well.
- Delay Settings: Adjust the delay between requests. For example, use
-d 5for a 5ms delay.
Conclusion
That’s it, folks! DNS brute forcing is a very essential for you as a hacker to learn. Make sure to check out different tools, adjust settings, and play around with word lists. The key is to keep the hardwork and practice! Remember, the hacking community is all about learning and sharing. If you have questions, drop them in the comments. Stay tuned for more beginner-friendly guides. Also don’t forget to check another cool blogs on this website i keep updating the content and making hacking an easy way to learn for all.
Happy hacking, and see you in the next guide! 🚀
Frequenty Asked Questions
- Firstly, what is a brute force DNS attack?
A malicious attempt to guess or force entrance into a DNS server by attempting every conceivable combination of domain names in an attempt to obtain private data or bring down a website is known as a DNS brute force assault. - What is a DNS brute force assault and why is it using the Fierce tool?
Fierce is a DNS reconnaissance tool that helps find potentially attackable domains or subdomains, which can help with DNS brute force attacks - Are DNS brute forcing laws in place?
No, DNS brute forcing is prohibited and can have serious repercussions, such as fines and criminal prosecution. - How do brute force DNS attacks operate?
Sending a lot of queries to a DNS server in an effort to guess the right domain name or subdomain is how a DNS brute force attack operates. - What are some telltale indicators of a DNS brute force attack?
Increased network latency, unauthorized DNS record modifications, and abnormally high traffic volumes on the DNS server are some typical indicators of a DNS brute force attack. - How can I defend against brute force assaults on my DNS server?
Use secure passwords, set up firewall rules, keep an eye on network activity, and update your server software to safeguard your DNS server against brute force attacks. - Is it possible to utilize the Fierce tool for ethical hacking?
Yes, ethical hackers can utilize the Fierce tool to find and address DNS infrastructure vulnerabilities on a network. - What could happen if a DNS brute force assault is successful?
If a DNS brute force attack is successful, confidential data may be accessed without authorization, network security may be jeopardized, and a company’s reputation may suffer. - Are there any legitimate ways to attack DNS addresses other than just using brute force?
Indeed, ethical hackers do not need to conduct illicit brute force assaults to find and fix vulnerabilities in a network’s DNS infrastructure; instead, they can use penetration testing tools and techniques. - How can I alert the relevant authorities about a possible DNS brute force attack?
In the event that you believe a DNS brute force assault is targeting your network, get in touch with the network administrator, your ISP, or law enforcement to report the attack and ask for help in containi


