Nuclei – Basic Guide for Hackers
This is Nuclei – Basic Guide for Hackers . Nuclie is a fast vulnerability scanner in the space of bug bounty hunting. The best feature it offers is pre written scripts by your fellow hackers that are referred as templates. All that this tool requires is a .yaml files and we are good to use this amazing tool.
Installing nuclei
You can install nuclie by following this github link and cloning it on your system https://github.com/projectdiscovery/nuclei
git clone https://github.com/projectdiscovery/nuclei
Or
go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latestIf you are on kali Linux just type
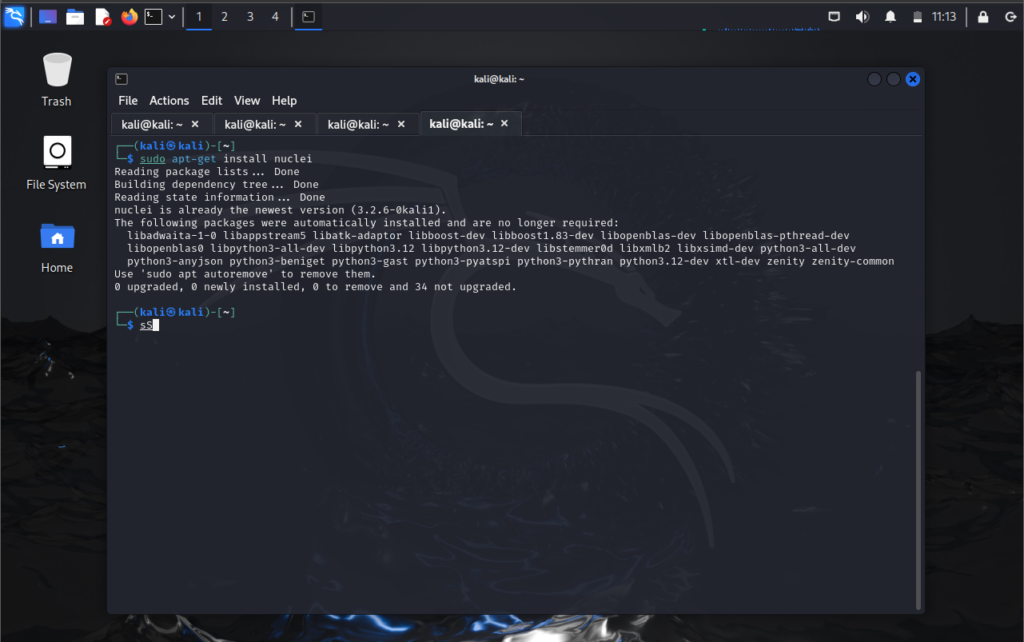
sudo apt-get install nucleiBasic usage of nuclei tool
To verify your tool has been installed let’s run the help command
nuclei --help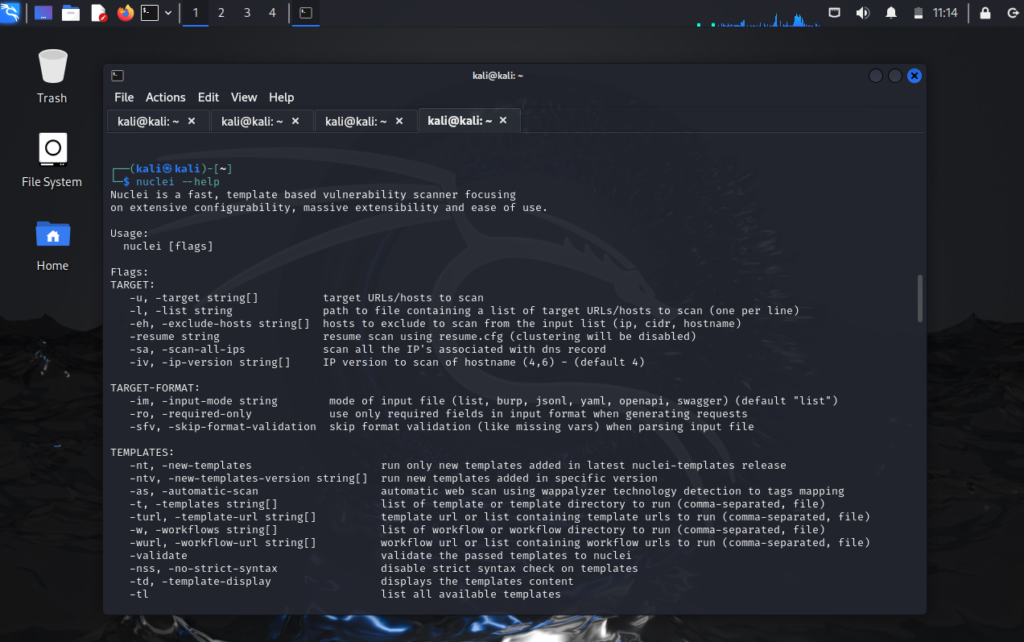
Note: What are this .yaml files if you have seen the previous nmap blog I have been telling you about nmap scripting engine that contains lot of nmap script these are similar pre-written scripts for scanning the host.
Let’s do basic scanning
nuclei -u https://hackingblogs.comAs you might see the scan results indeed gives a good amount of detail on txt-records, caa-fingerprint , nameservers and much more.
Well then let’s see how you can use and run templates against target we will be running the /http/osint template on our site .
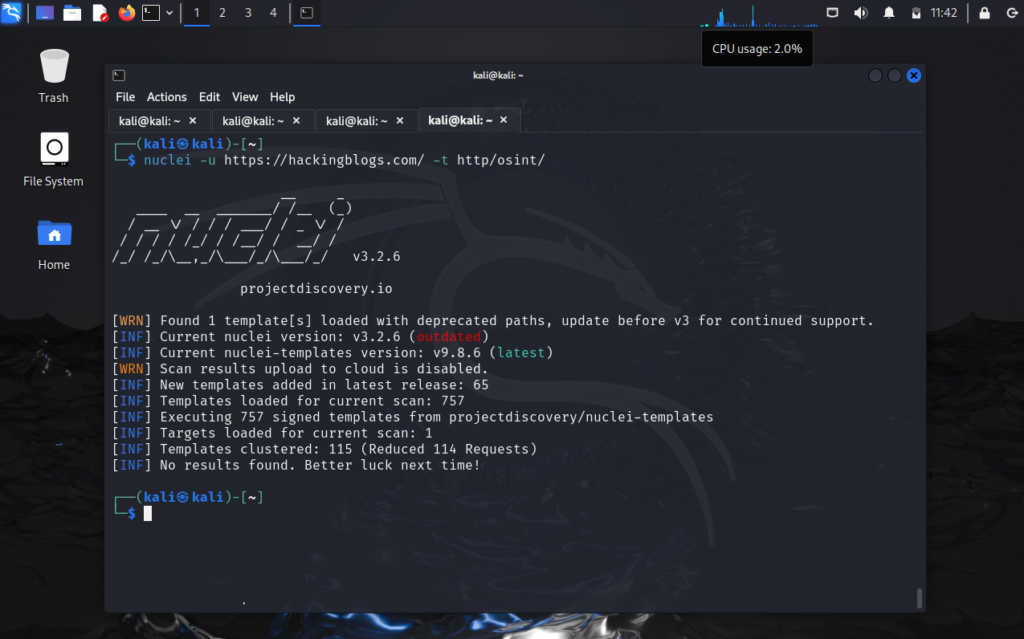
Well so far there is no interesting data that we see but the method remains the same to use templates.
Using Others templates
So in order to use someone’s else templates we will be using the following method.
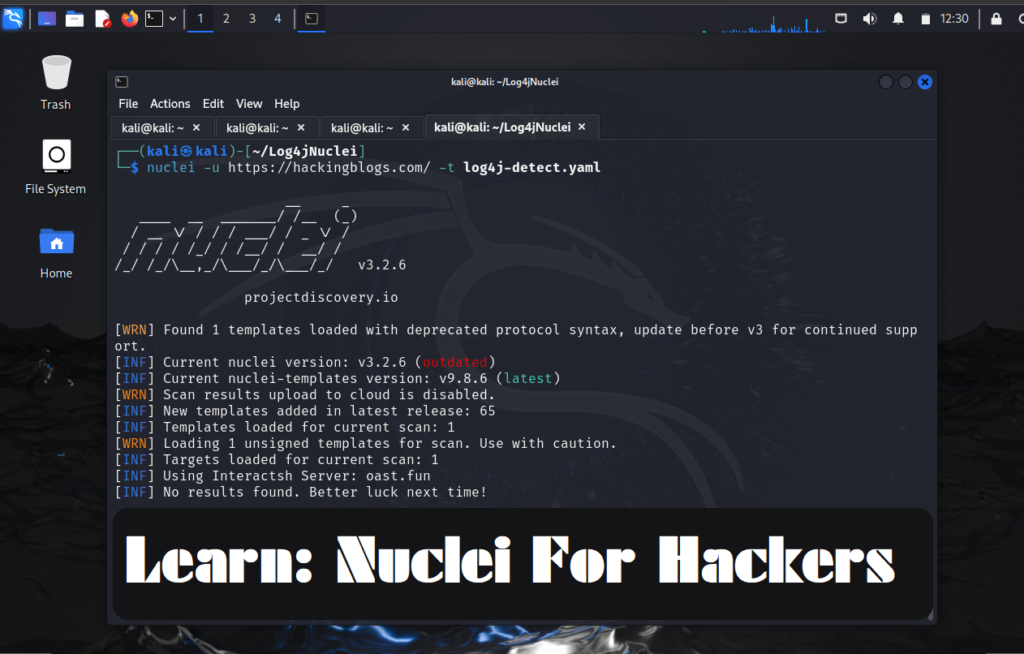
So you might be knowing about log 4j flaw which was quite popular during the covid times let us see how nuclei makes it easy for us to hack on.
You may install the github repo for the nuclei template
https://github.com/numanturle/Log4jNuclei
The .yaml file for log4j is now on our system ready to be used let’s see how we can run it .
So you can see here that we have run log4j on our site but there is no such eye raising results but you might find more templates and try running it and it will definetely help you guys.
Frequenty Asked Questions
- What is Nuclie tool for bug bounty?
Nuclie is a comprehensive tool designed for bug bounty hunters to streamline their workflow, automate certain tasks, and improve efficiency in finding vulnerabilities in web applications and websites. - How can Nuclie help bug bounty hunters?
Nuclie offers a wide range of features such as subdomain enumeration, port scanning, automated vulnerability scanning, and reporting tools that can help bug bounty hunters identify and exploit security flaws in target systems. - Is Nuclie tool free to use?
Yes, Nuclie is an open-source tool that is freely available for bug bounty hunters to download and use for their security testing activities. - Can Nuclie be used by beginner bug bounty hunters?
Yes, Nuclie is designed to be user-friendly and easy to use for bug bounty hunters of all skill levels, including beginners who are just starting their journey in the world of ethical hacking. - What programming languages are supported by Nuclie?
Nuclie is written in Python and supports various programming languages commonly used in bug bounty hunting, making it versatile and adaptable to different testing environments. - How frequently is Nuclie updated?
Nuclie is regularly maintained and updated by its developers to ensure that it remains current with the latest security trends and tools used by bug bounty hunters in the field. - Can Nuclie be integrated with other security tools?
Yes, Nuclie is designed to be interoperable with other security tools commonly used in bug bounty hunting, allowing users to create a custom workflow that suits their specific needs and preferences. - What kind of vulnerabilities can Nuclie help identify?
Nuclie can help bug bounty hunters identify a wide range of vulnerabilities such as SQL injection, cross-site scripting (XSS), server misconfigurations, and insecure API endpoints, among others. - Is Nuclie tool supported on all operating systems?
Nuclie is compatible with various operating systems such as Windows, Linux, and MacOS, ensuring that bug bounty hunters can use the tool on their preferred platform without any compatibility issues. - Where can I find documentation and support for Nuclie?
Nuclie offers comprehensive documentation, tutorials, and community support for bug bounty hunters who want to learn more about the tool and how to effectively use it in their security testing activities.


