The most recent PayPal-related fraud is an excellent example of the constantly developing strategies used by cybercriminals to trick innocent people. In a recent blog post, Carl Windsor, the Chief Information Security Officer (CISO) of Fortinet, detailed this concerning scam and called it a “phish-free phishing attack.” This type of phishing scam is far more difficult to identify than traditional ones because it does not rely on fake links or suspicious email addresses.
Understanding the working of this Attack
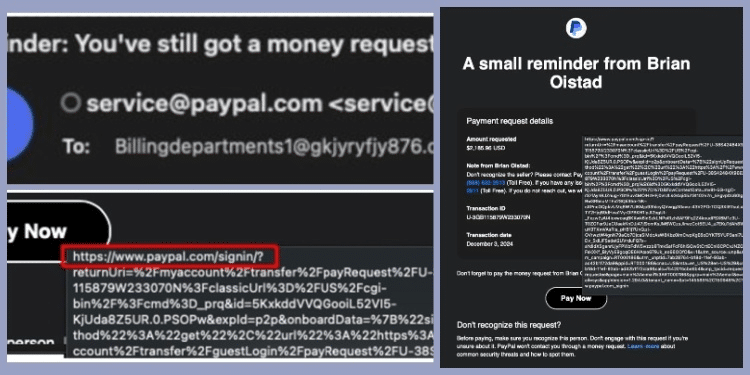
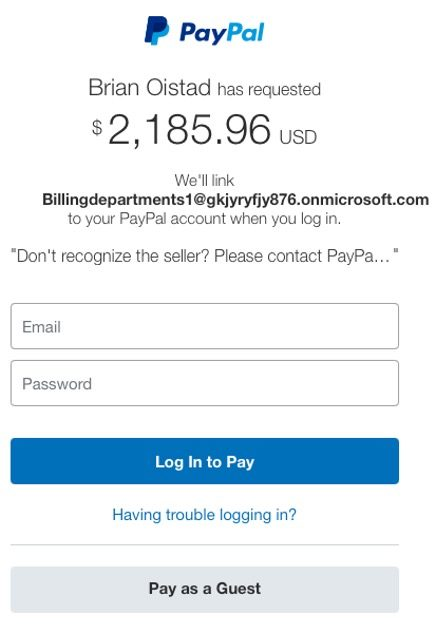
The scam starts with an email that seems authentic and is sent from "service[@]paypal.com," which is PayPal’s real email address. Even the most experienced internet users may be fooled by the email’s appearance of authenticity and use of a legitimate PayPal login URL. Windsor, who was the victim of this fraud, described the methods that the criminals employed:
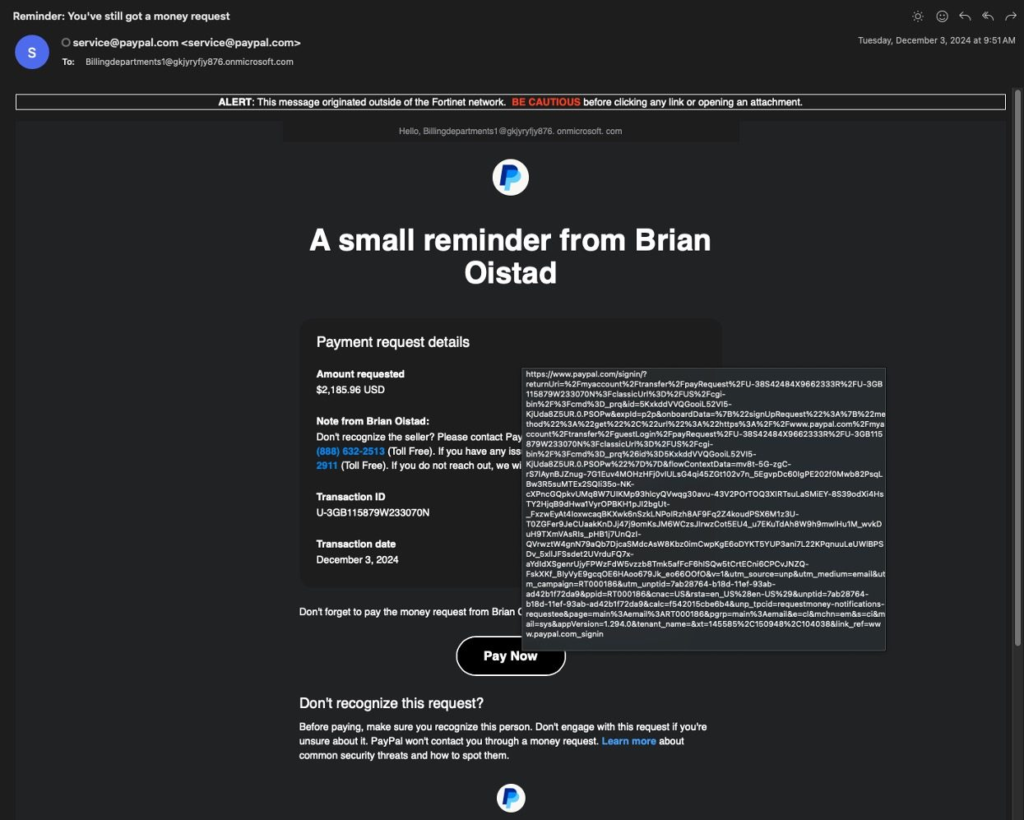
- Abusing PayPal’s “Send and Request Money” Feature : The attackers take use of PayPal’s built-in function that lets users ask anyone for money. They provide the impression that their email is authentic by doing this.
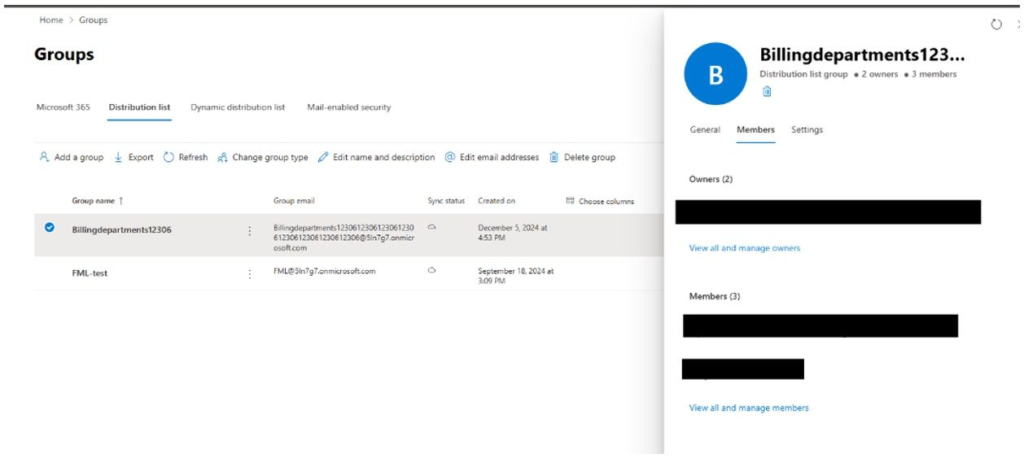
- Using a Microsoft 365 Test Domain : The scammers generate a mailing list with victim email addresses by registering a free Microsoft 365 test domain. Because Microsoft 365 emails usually utilise the domain “onmicrosoft.com,” it is more difficult to identify the fraud.
- Email Spoofing That Passes Security Checks : Microsoft’s Sender Rewrite Scheme (SRS) modifies the sender address when the money request is submitted through PayPal in order to conform to SPF/DKIM/DMARC authentication protocols. By doing this, the email is certain to go past spam filters and not be reported as harmful.
Well Do you know a lot of danger comes with this
A legitimate PayPal sign-in URL (https://www.paypal[.]com/sign-in/?) is included in the email to give recipients a false sense of security. Victims who click on this link are taken to the official PayPal login page, but this is where the true trap is:
Your account is connected to the attacker’s account when you log in to examine the money request. Scammers can now access your PayPal account and take your money or carry out illegal activities thanks to this. According to Windsor, this tactic is so clever and sophisticated that it gets past PayPal’s own phishing detection guidelines.
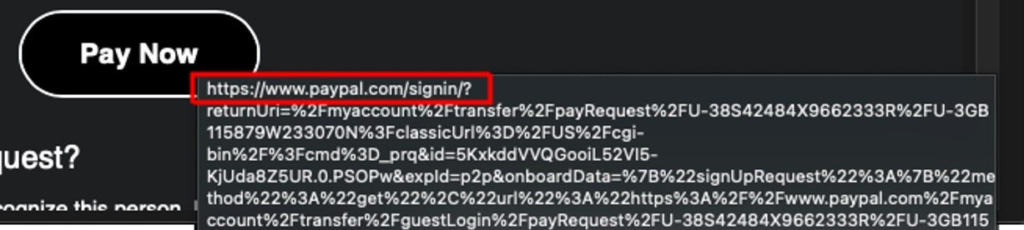
The fraud appears to be particularly successful because, unlike standard phishing emails that use fake URLs or badly written messages, it is nearly hard to tell this scam from authentic communication.
How to not get in the same trouble ?
Even if an email seems to be from a reliable source, the CISO of Fortinet stresses the need to be cautious while responding to it. Here are some safety recommendations for you:
- Develop the Skills of a Human Firewall According to Windsor, a “human firewall” is someone who is suspicious and alerts them to any unwanted emails, regardless of how legitimate they may appear. Make sure to carefully review emails before acting on them.
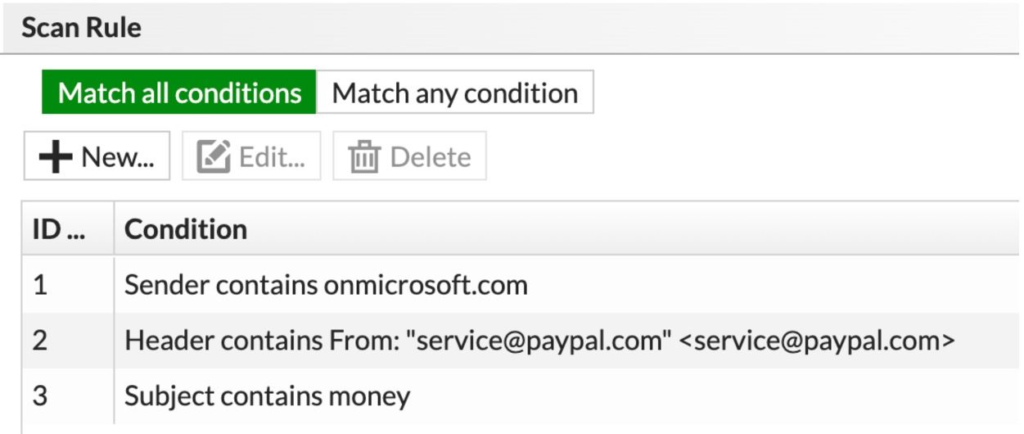
- Put Email Filters in Place Make a rule for data loss prevention (DLP) that will identify emails with questionable parameters. Windsor advises being aware of the following symptoms: The sender has “onmicrosoft.com” in it. Included in the header is “service[@]paypal.com.”
- Observe the Security Advice of PayPal. Emails from senders you do not recognise or that use generic greetings should be avoided. Verify the webpage address by hovering over links before


