Ready to learn about a new tool that will make your life easier as hacker ? In this article, we’ll learn how you can use Searchsploit, a powerful command-line tool for finding exploits. This guide is tailored for beginners, providing practical steps and commands to help you navigate and utilize this tool effectively.

Introduction
This tool is a command-line search and query tool designed for finding exploits in the Exploit Database (exploitdb). It comes pre-installed in popular penetration testing distributions like Kali Linux, making it a must-have tool for security professionals.
SearchSploit Basics
Let’s jump into practical aspects. Updating the local exploit database is crucial. Execute the following command to ensure your database is up-to-date:
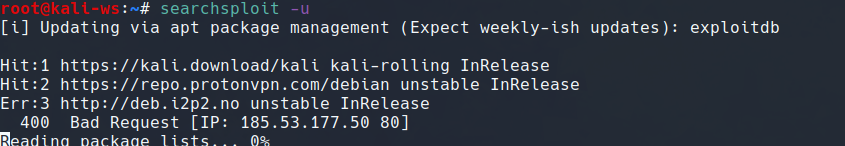
searchsploit -u
This command utilizes the aptitude package management system and ensures you have the latest exploits at your disposal.
Performing Basic Exploit Searches
To search for exploits related to a specific software version, such as OpenSSH, use the following command:

searchsploit open ssh
This simple query provides a list of exploits associated with OpenSSH. Feel free to refine your search further by specifying the software version, e.g., OpenSSH 7.2: this will provide specific results.
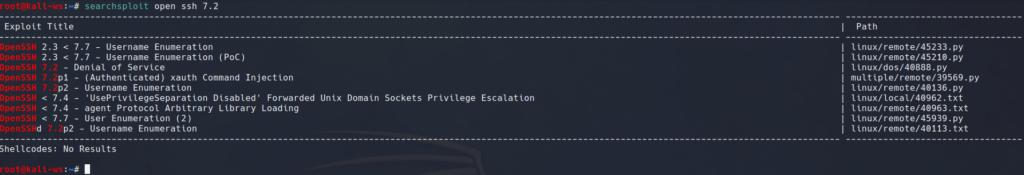
searchsploit open ssh 7.2Platform-Specific Exploit Searches
For platform-specific searches, where the focus is on the title of the exploit, employ the ‘-t’ command. For example, to find Windows 10 exploits, use:
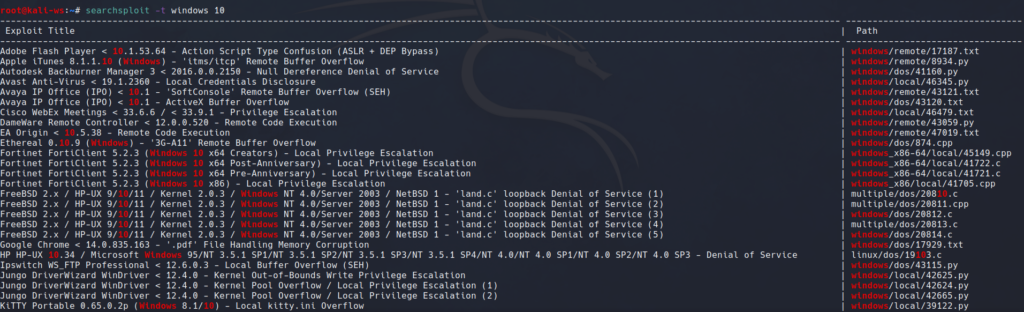
searchsploit -t windows 10
This narrows down the results to exploits with ‘Windows 10’ in their titles, providing more targeted information. All the exploits that are made to exploit the architechture, the operating system etc.
Copying Exploits Locally
Once you’ve identified an exploit you want to use, copy it to a working directory using the following commands:
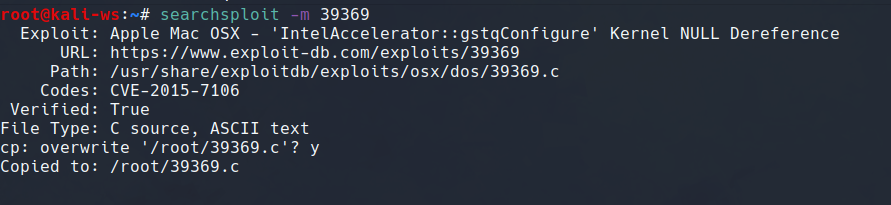
searchsploit -m <exploit_number>Replace <exploit_number> with the specific exploit number you want to copy. This action ensures you have the exploit file locally for further analysis and use.
Conclusion
SearchSploit proves to be an invaluable tool for penetration testers, offering efficiency and accessibility. Whether you’re searching for specific exploits, updating your local database, or copying exploits for practical use, mastering this tool enhances your penetration testing capabilities.
In conclusion, this tool will be very helpful for you either you are solving a ctf performing real life bug hunting or exploiting local systems.That is it for this article and i will see you in the next article also checkout different articles that are posted in this website. Stay Hungry Keep Learning Keep Hacking !
Frequently Asked Questions
- What is Searchsploits in Kali Linux?
This tool is available in Kali Linux that allows users to search for exploits in the Exploit Database. - How do I use this tool in Kali Linux?
You can use this tool by entering the command “searchsploit” followed by the name of the exploit or vulnerability you are looking for. - Can I search for specific exploits using this tool?
Yes, you can search for specific exploits by entering keywords related to the exploit you are looking for. - Is this tool only limited to searching for exploits?
No, Searchsploit can also be used to search for other information such as shellcode and papers related to vulnerabilities. - How frequently is the Exploit Database updated in this tool ?
The Exploit Database in Searchsploit is regularly updated to ensure that users have access to the latest exploits and vulnerabilities. - Can this tool be used to analyze vulnerabilities on a network?
Yes, Searchsploit can be used to analyze vulnerabilities on a network by searching for relevant exploits that can be used to exploit those vulnerabilities. - Is this tool a standalone tool in Kali Linux?
Searchsploit is a part of the Exploit Database project and is integrated into Kali Linux as a pre-installed tool. - Can I contribute to the Exploit Database through this tool?
Yes, users can contribute to the Exploit Database by submitting new exploits and vulnerabilities through this tool . - Are there any limitations to using this tool in Kali Linux?
While Searchsploit is a powerful tool, it is important to use it responsibly and ethically to avoid any legal issues. - Can this tool be used by beginners in Kali Linux?
Yes, this tool can be used by beginners in Kali Linux to search for exploits and vulnerabilities, but it is recommended to have a basic understanding of ethical hacking principles before using it.


