
Introduction
Welcome to the Recon Special Penetration Testing Bootcamp, where i will be teaching you about different ways of Passive Information Gathering Techniques & Tools for the trade. In this article, we’ll break down the key concepts while you learn providing commands and the knowledge that you require and thus making it suitable for beginners and the advance hackers.
Search Engine Reconnaissance
First, we will find your target’s administration consoles and vulnerabilities using Google Hacking or the Google Hacking Database. Run commands such as these;
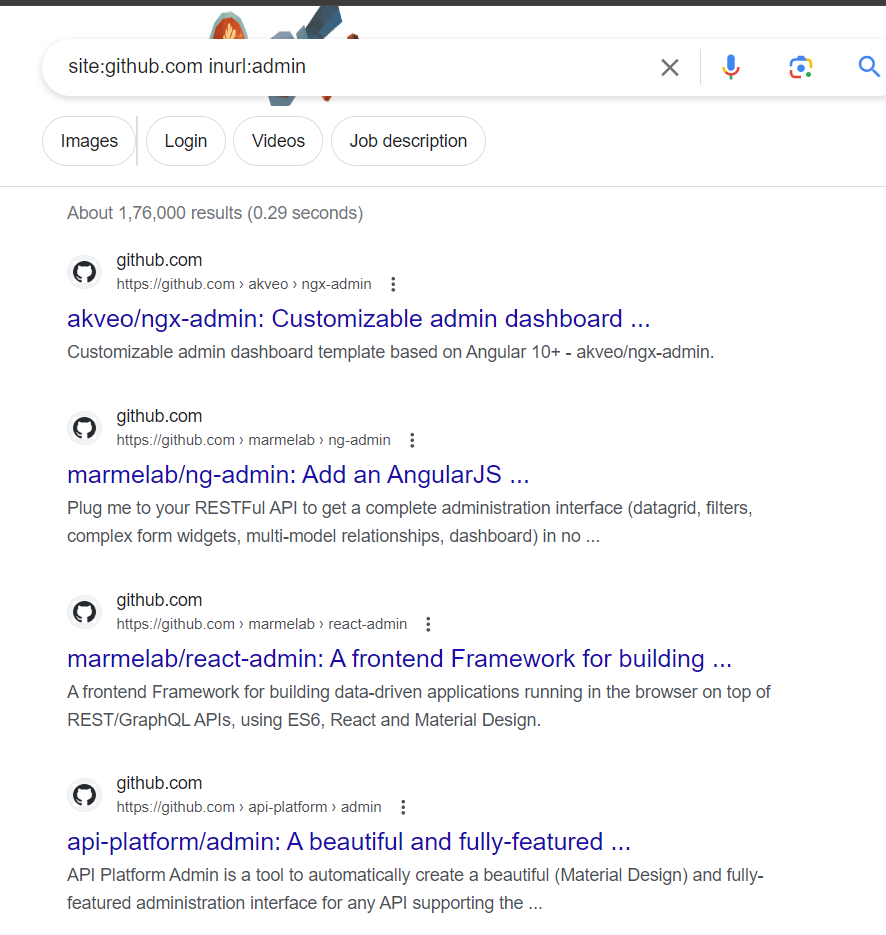
site:example.com inurl:admin
If you want and indepth guide on Google Hacking Check out these two blogs which will blow your mind.
Explore Shodan(I will be making a indepth guide for it too), a search engine for obtaining crucial information about hosts and target networks:
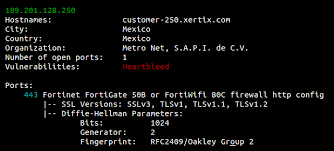
shodan search example.com
Social Network Recon
This type of Passive Information gathering can be somewhat like to Extract valuable employee data from platforms like Facebook, Twitter, and LinkedIn using frameworks. For example for Facebook, you might use:
python3 osint-scraper.py -u <target_facebook_profile_url>
WHOIS Information
To Retrieve domain and registrant information with WHOIS commands this can be benficial in knowing when is the expiry to look legitimiate as a hacker:

whois example.com
Website Footprinting
Dive into code review with tools like HTTrack and archives.org to access older versions of web pages so that you can see the bugs that persisted then and the technologies that was used:
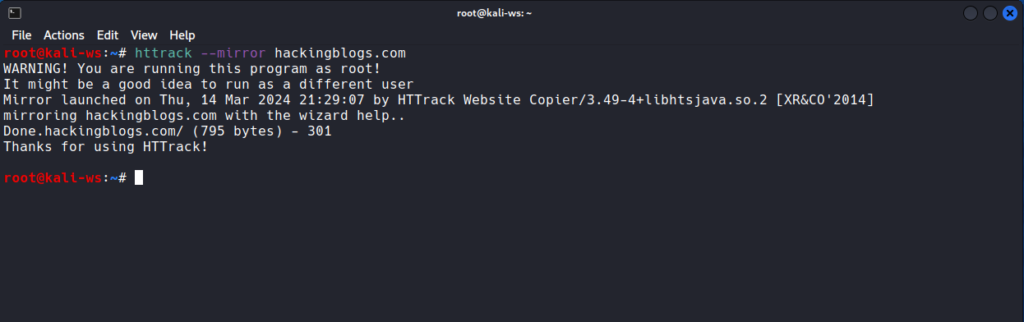
httrack --url=example.com --mirror
Use proxies for inspecting requests to the web server:
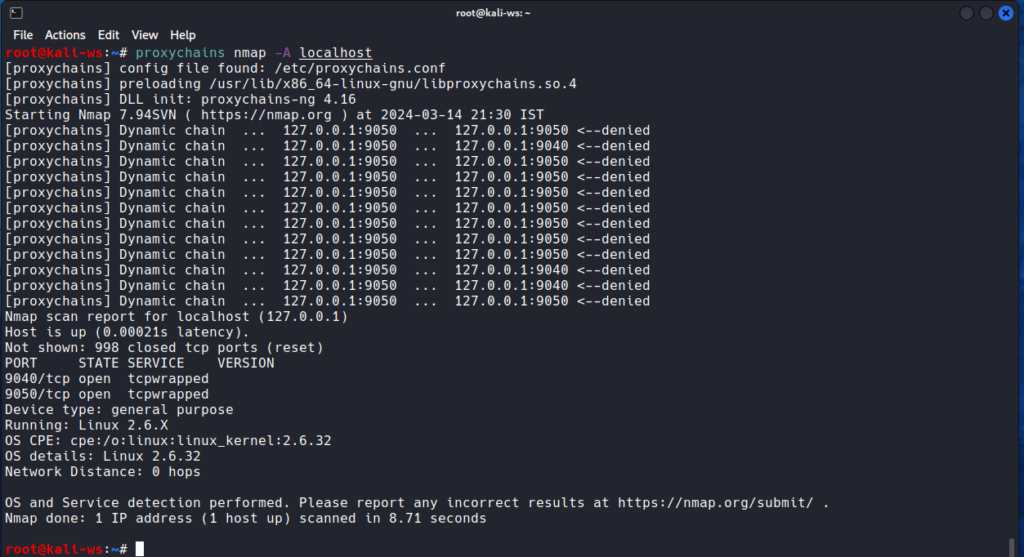
proxychains <your_command_here>
Web Technologies Footprinting
Identify web technologies and frameworks using builtwith.com on Firefox or their online service to find out the version and the software it is using to find any known CVE or bugs in the current version being used:

firefox --new-tab https://builtwith.com/example.com
Domain and Subdomain Reconnaissance
Offcrs this is important while doing recon try to employ Sublist3r, a powerful tool using passive information to find out the subdomains of a site:
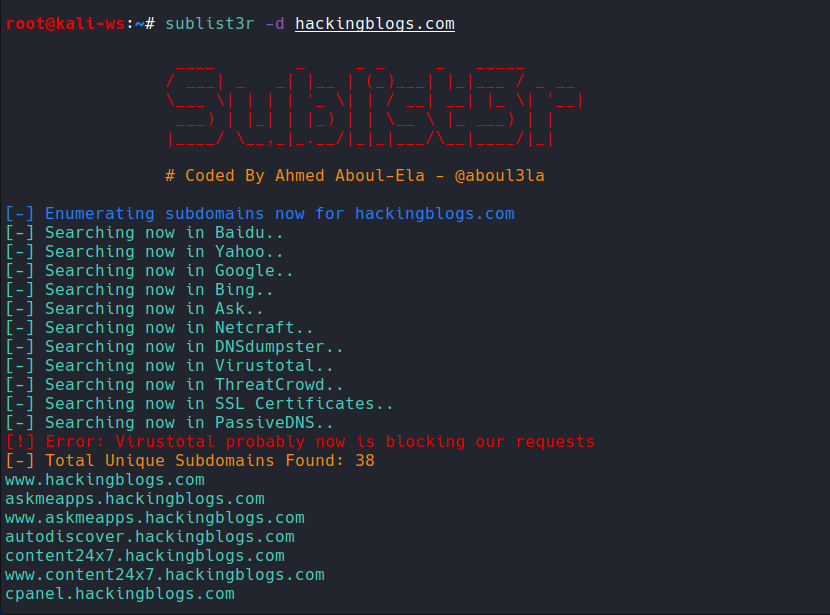
python sublist3r.py -d example.com
Cloud Reconnaissance
Focus on AWS using the S3 scanner to find hidden data in aws buckets which can lead you to important information disclosure:
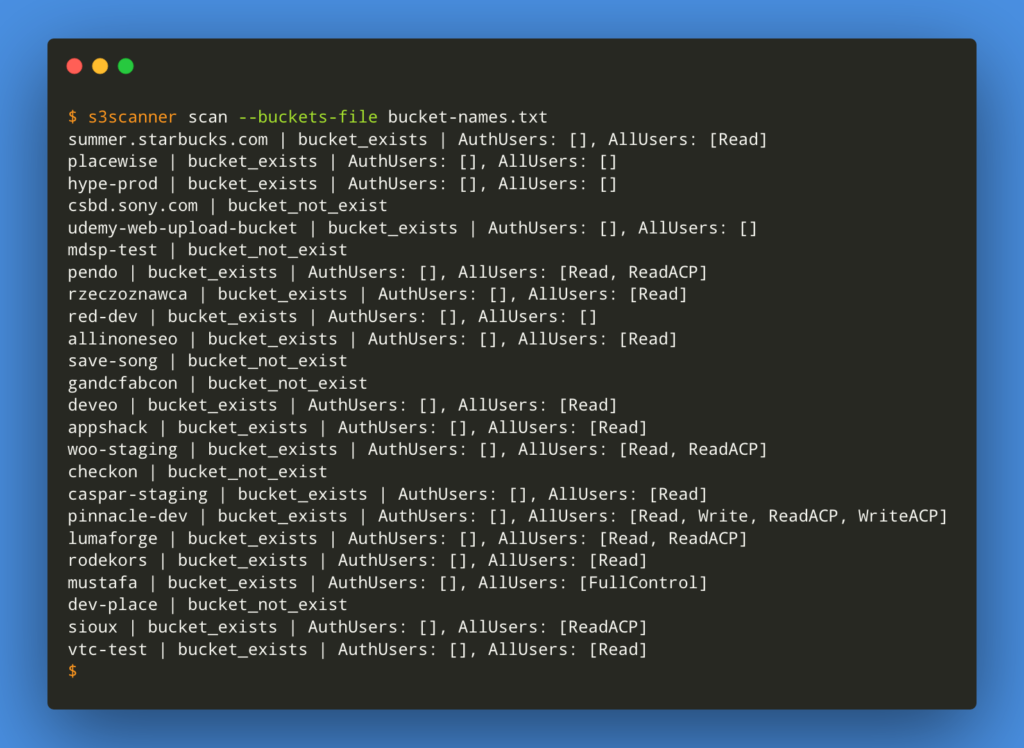
python s3scanner.py -u example.com
Metadata Analysis
For image and document metadata, use Metagoofil while doing forensics or stegnography this can usually help you while doing CTF’s:
python metagoofil.py -d example.com -t doc,pdf -l 100 -n 50 -o output_folder
Summing up all the Recommended Frameworks and Tools
- Recon–ng: A standard for reconnaissance.
- Maltego: Great for building a scope and gaining an overview.
- Sublist3r: Effective for subdomain enumeration.
- The Harvester: Enumerate emails from publicly available information.
- OSRFramework: A comprehensive framework for open-source intelligence reconnaissance.
- Netcraft: Provides extensive information about the target’s domain and web technologies.
- Showdown: A powerful search engine offering a wealth of information.
- Metagoofil: Extracts metadata from documents.
Conclusion
This was just a normal blog covering vast tools to help you make passive reconnaissance to your target remember using this tools is legal and will boost your skill as hacker but always use these tools with responsibility.
That’s it for today, hackers! You’ve leveled up your hacking skills. Stay tuned for more beginner-friendly guides. Happy hacking! Also don’t forget to check another cool blogs on this website i keep updating the content and making hacking an easy way to learn for all.
Frequently Asked Questions
1. Describe Sublist3r.
A subdomain enumeration tool called Sublist3r is used to find subdomains inside a given domain.
2. In what ways is Sublist3r applicable to cybersecurity?
Cybersecurity experts can use Sublist3r to find possible points of entry for attackers because subdomains are frequently disregarded by businesses when it comes to security protocols.
3. Define Metagoofil.
A tool called Metagoofil is used to extract metadata from publicly accessible documents, such as Word, PDF, and image files.
4. What is the value of Metagoofil in digital research?
Digital detectives can use Metagoofil to collect important data from publicly accessible documents, including author names, email addresses, and geolocation information.
5. Describe Amazon Web Services, or AWS.
Amazon offers a cloud computing platform called AWS, which offers a variety of infrastructure services, such as networking, storage, and processing capacity.
6. What are the commercial benefits of AWS?
Businesses can gain from AWS by using its scalable and reasonably priced cloud solutions, which can aid with operational efficiency, increased agility, and improved overall performance.
7. Describe Netcraft.
A cybersecurity firm called Netcraft offers services for protecting against online risks such as virus hosting, phishing attack detection, and monitoring.
8. How does Netcraft contribute to website security?
By offering real-time monitoring and alerting services, Netcraft can assist in the protection of websites by enabling their owners to promptly identify and address any security issues.


