As we all know a person must know the weapons before going to war it solves half of the problem and increases your chances of winning a war the same goes for when you are hacking into a computer system knowing which tools will work better for you is the first step of getting in the top of the game.
In this blog, I will be sharing with you how you can use these Top 5 Free hacking tools and what are these Free hacking tools. Also don’t forget to check other interesting blogs on hackingblogs.com. Let’s get into the topic
Top 5 Free Hacking Tools
Nmap – Network Mapper
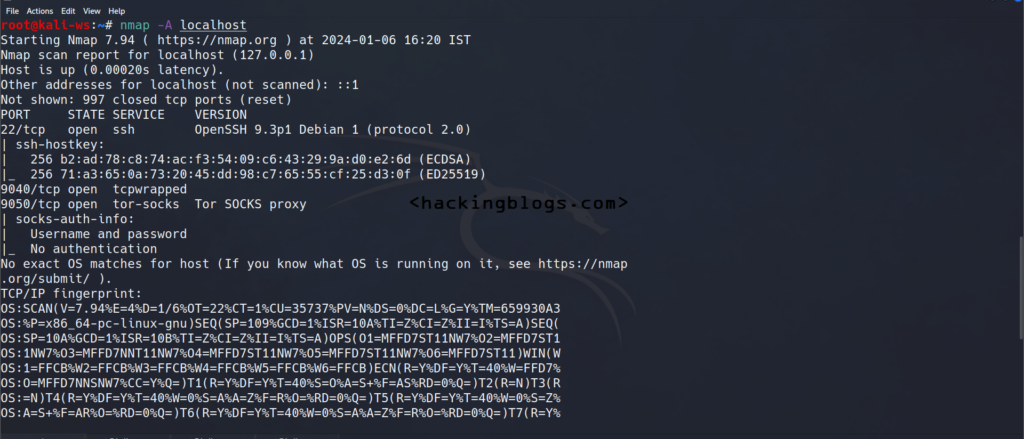
Nmap is a free and open source tool that is used in the field of network discovery and security auditing Nmap is very powerful and it can be used to scan huge networks having thousands of machines and it is a command line tool.
Map supports a wide variety of operating systems these areb:-
Linux,Microsoft,Windows open,BSD Solaris,Irix,Mac OS X,OpenBSD
Nmap is used to scan a network it is used to track, if the hosts are available on the particular network services that are offered by Nmap are generally application names along with their version operating system and the version and the target system that is currently running on .
It helps in firewall evasion and targeting the system and has been scanning for open ports both in the TCP and the UDP network.
To download and learn more about Nmap go to the following link https://nmap.org/download.html
Metasploit
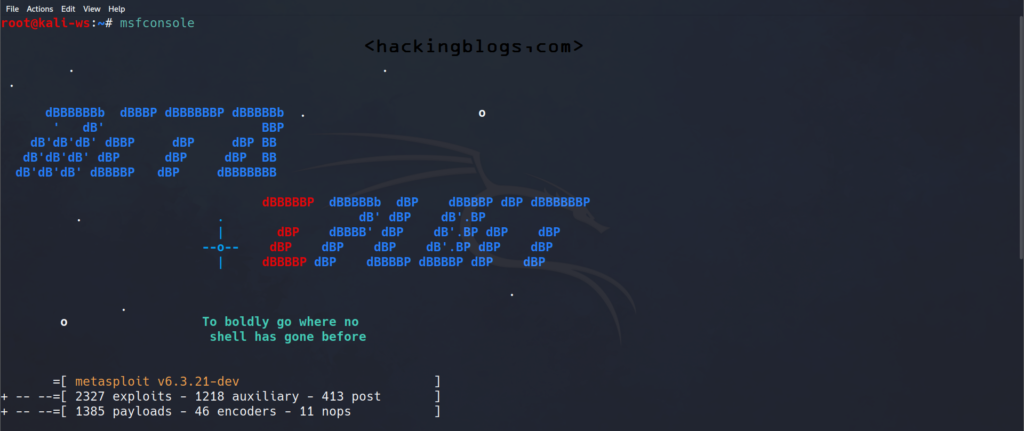
Metasploit is basically a penetration testing toolkit that is used during security assessment.
Metasploit can be used to launch a variety of attacks on the system it is used in the exploitation phase of penetration testing it analyzes the vulnerable system while security testing and then after the testing has been done it can be used to exploit the flaws that have been uncovered while penetration testing
Metasploit is used in a variety of places these are generally are when TCP port scanning is done to obtain the information from the target system.
Viewing the host list and services that are running on the targeted system and analyzing them in a project view and now this vulnerability scan can be used in the target system to get the flaws and later these can be used to plan the attack and exploit the flaws
To know more about Metasploit and to download it in your own system visit the following link https://github.com/rapid7
Nikto
This tool is basically a web server assessment tool it is an open-source tool that helps in performing attacks on the webserver to find various vulnerable misconfiguration files and outdated servers in the web server.
It utilizes the HTTP protocol to determine whether a page or script exists on the target.
The various features that Nikto provides are as follows It checks for outdated server it can scan multiple hosts in the server and also
it can guess credentials while brute forcing for example trying many different ID and password combinations and it highlights and flags the unusual headers.
To download Niko visit the following link https://github.com/sullo/nikto
John the Ripper
John the Ripper is an open-source software that is used for brute forcing and password cracking it supports both dictionary attacks and brute force attacks.
There is also a pro version of John the Ripper Pro it is a more user-friendly version and provides a higher functionality than the normal version in password cracking at the enterprise level.
A variety of features is provided by John the Ripper these are a lot of switches is offered by John the Ripper while cracking the password until the termination command is not provided.
To download john the Ripper visit the following link https://www.openwall.com/john/
Wireshark
Wireshark is an open-source tool that is used to capture traffic on the network it is basically a network protocol analyzer tool.
Wireshark health in a lot of ways that is It helps in sniffing the passwords capturing all the packets over the network.
It also captures any HTTP packet transmission over the network just click on follow TCP connection in the HTTP packet and now you can see the username and passwords that are captured over the network.
Burp Suite
This is one of the trendiest hacking applications that is used by hackers for intercepting data packets it is basically used during web application penetration testing
It provides a wide range of tools some of these are the repeated tab and the intercept tab and it also offers tools like encrypting and decrypting data.
So these are the list of the Free hacking tools that are most used and preferred by hackers go check them out learn to use them and thank me later when you see success through them.
Frequently Asked Questions (Faq’s)
-
What is Burp Suite?
Burp Suite is a popular web application testing tool used for security testing, penetration testing, and vulnerability scanning.
-
What is Wireshark?
Wireshark is a widely used network protocol analyzer that allows users to capture and interactively browse the traffic running on a computer network.
-
What is Nmap?
Nmap is a powerful network scanning tool used to discover hosts and services on a computer network, thus creating a “map” of the network.
-
What is Nikto?
Nikto is an open-source web server scanner that performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/CGIs, checks for outdated versions of over 1250 servers, and more.
-
What is Metasploit?
Metasploit is a penetration testing framework that enables users to develop, test, and execute exploit code against remote targets to determine security vulnerabilities and weaknesses.
-
What is John the Ripper?
John the Ripper is a password cracking tool that is used to detect weak passwords and has the capability to crack password hashes using various methods such as dictionary attacks, brute force attacks, and more.