Hello dear hacker !!
Greeting of the day. Here is freshly toasted and spiced articles containing valuable information to crack Zip and Rar Files using the HashCat Utily. So Enjoy the articles as you learn How to use the tool. Also View another spicy content on our offcial blogsite Hackingblogs.com.
Let’s Get to hacking….
Assets You Require
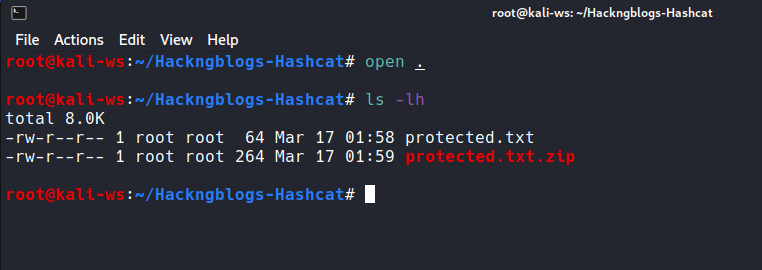
So from the perpective of the end user go forward and create a dummy text file as you see here. You can write any strings or content as you wish in the file.
Now that you have done this go forward and archive the text file into zip format as you see here.
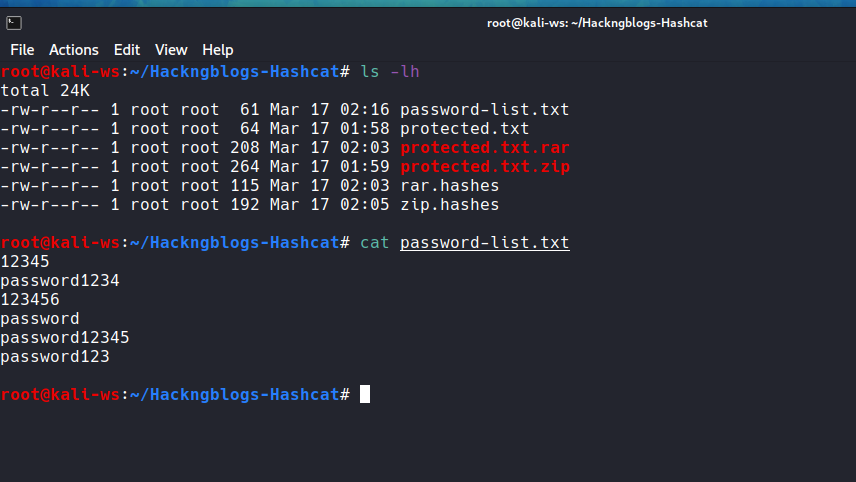
And most importantly assign a password to the zip. For the demonstration Purpose let’s keep it simple to password123
Filename = [protected.txt] [hackingblogs.zip]
password = password123
Tools we will use
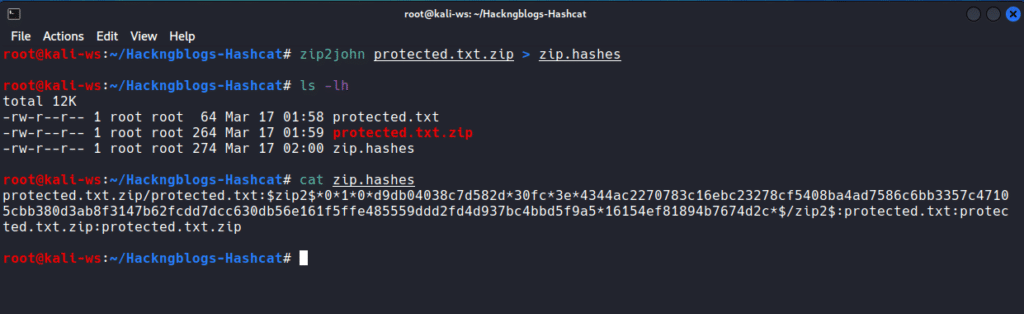
Zip2john
Zip2john is a tool that allows us obtain the hash from zip files. If you are cracking a.rar file, you can use the rar2john programme.
Here is the syntax to obtain the password hash of a
zip file: $ zip2john file.zip > zip.hashes
This command will obtain the hash from the zip file and put it in the zip.hashes file.
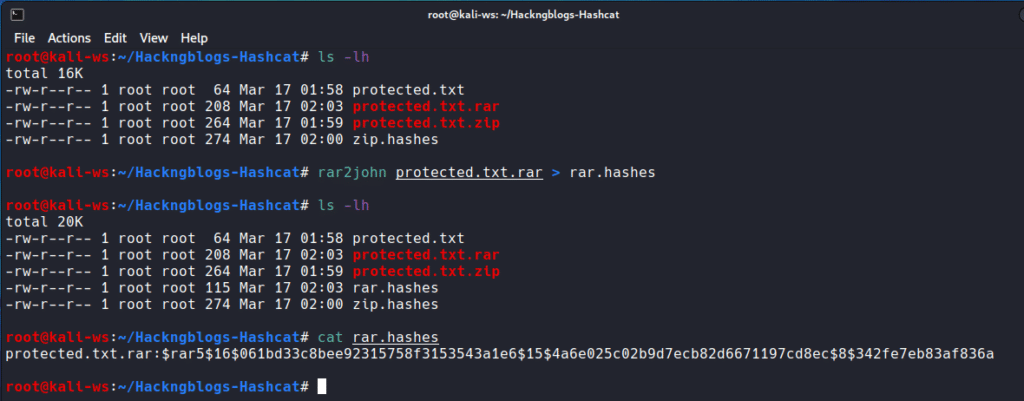
Rar2john
If you are cracking a .rar file, you can use the rar2john utility.
Follows the same syntax as to zip2john
Rar file: $ rar2john file.zip > rar.hashes
HashCat
Using rainbow table, dictionary, brute force, and hybrid approaches, hashcat is an advanced password recovery programme that can crack passwords.
In addition to auditing system passwords for security reasons, it can be used to recover forgotten or lost passwords.
Both private users and businesses use it for security audits and password recovery.
Obtaining the Hash
So after you have made the file.txt and successfully archieve it now you need to get the hash of the archieve in order to crack the password.
So inorder to obtain the hash of the archieve, type the following command
zip2john hackingblogs.zip > ziphash.txt
This will successfully copy the hash to a seperate file that is ziphash.txt
In order to ensure things up type
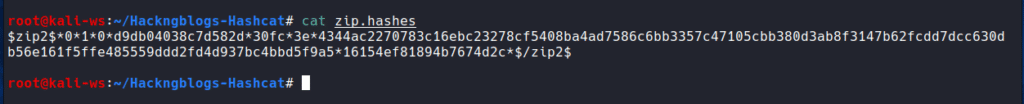
cat ziphash.txt
As you see this is the hash
Removing The Unwanted Head and Tail
So as you see the highlighted data is not as so important to hashcat and inorder to use this hash we need to remove this from the text file.
So go forward and use the vim editor to do this stuff , type
vim ziphash.txt
This will open the file in the editor…
Type I in order to make deletion delete the shown data and let the hash remain which is genrally under ($$)
Type wq after successfull deletion of the hash
And now the hash is in the correct format so let’s go forward and use it.
Utlising HashCat
So The quick and dirty method is to just go forward and open documentation
type : hashcat –help
This will return the help menu that you should read although i am adding some of the important switched that you should definetly check out.
Way to write a hashcat command
Hash Type
After typing hashcat you need to speicify the hash type
This is done via the -m switch
There are different hashtype example md5, SHA1… and they have there unique id’s
Attack Type
After you have selected the hash type you need to specify the attack type.
This is done via the -a switch
There are different attacks modes like bruteforce, dictionary, straight etc….
Cracking Our Zip File
So what is out hash that we are dealing with ?
So you don’t need to worry i have already found it for you its winzip hashtype code 13600
And The Attack type that we’ll deal with is the straight attack (-a) code 0
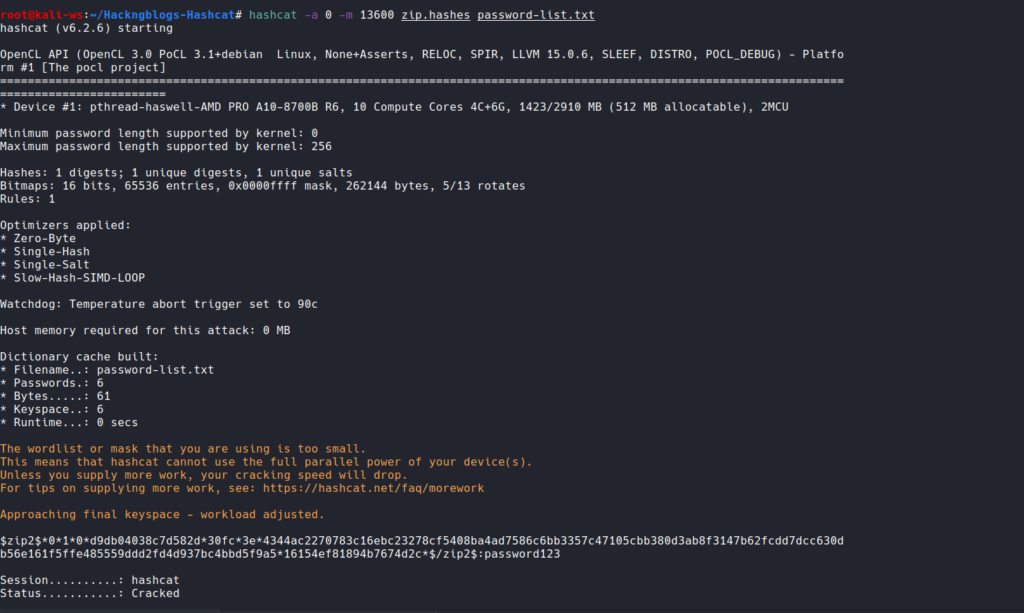
So this is the command that you will use for running hashcat
hashcat -a 0 -m 13600 ziphash.txt /usr/share/rockyou.txt
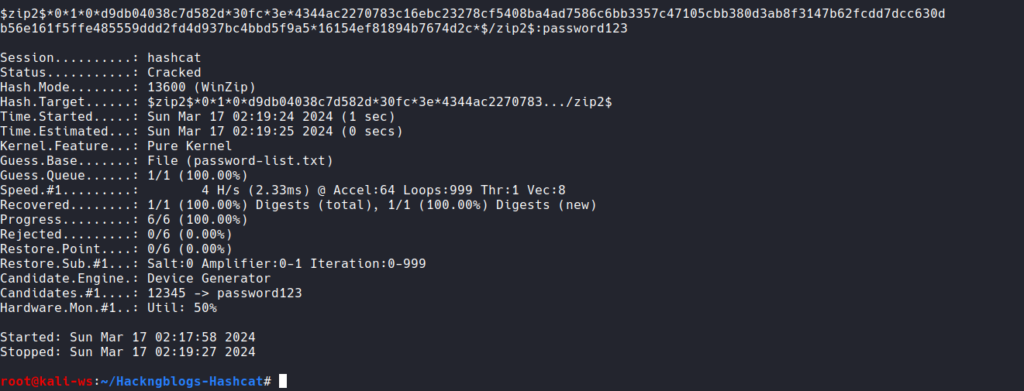
Cracking Our Rar’s File
So now that you know how we can crack a Zip archieve let’s move to cracking a rar archieve.
Go forawrd and create a rar archieve for the same text file protected.txt
Don’t Forget to assign a password to this rar file
Filename – [protected.txt] [hackingblogs.rar]
password – password123
Generating Hash
Now that you have the rar file we need to get the hash of this file so to get the hash of this file we will be utlising the Rar2john Utility.
So go forward and type :
rar2john hackingblogs.rar > rarhashes.txt
And as always you hashes get loaded up…
Cat rarhashes.txt to check the hash exist and as you see it does..
Go forward open the vim editor remove the element before the ($$) and write and quit from the vim editor.
Writing The Hashcat Command
So in order to write the command we need to find the hashtype and code and as you all are to lazy to find it yourself i will let you know what it is.
So it is a Rar5 hashtype and the code is 13000
The attack mode will be straight 0
The Command we’ll be using will be
hashcat -a 0 -m 13000 rarhashes.txt /usr/share/rockyou.txt
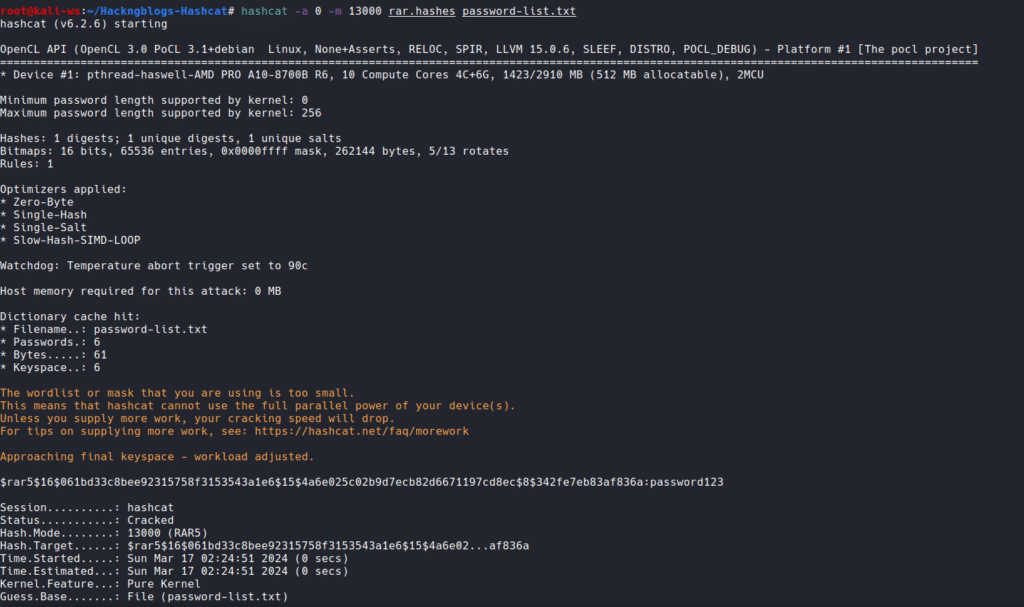
And yeah you can see that we have successfully cracked this rar archieve aswell. So was it not interesting to do it..
Frequently Asked Questions
- Q: What is Hashcat and how does it work?
A: Hashcat is a fast and highly efficient password cracking software that is capable of recovering lost or forgotten passwords by employing various cracking techniques. It works by taking a hash (an encrypted version of a password) as input and attempts to derive the original password through brute force, dictionary attacks, or hybrid methods. - Q: What are the different hash types supported by Hashcat?
A: Hashcat supports a wide range of hash types, including MD5, SHA-1, SHA-256, SHA-512, SHA-3 (Keccak), NTLM, LM, RIPEMD-160, and many more. It also supports GPU acceleration, making it faster than other traditional password cracking tools. - Q: What are the different attack modes available in Hashcat?
A: Hashcat offers several attack modes, such as brute-force, dictionary, hybrid, mask, and combinator attacks. Brute-force attacks try all possible character combinations, dictionary attacks use pre-made wordlists, hybrid attacks combine multiple attack modes, mask attacks use a specified character set and pattern, and combinator attacks generate combinations of words from a provided list. - Q: How can I optimize Hashcat for better performance?
A: To optimize Hashcat, ensure your system has enough RAM and that you’re using the latest version of Hashcat. You can also use multiple GPUs to increase processing power, choose the appropriate hash type and attack mode, and fine-tune settings like the wordlist size and character set for mask attacks. - Q: What is the difference between Hashcat and other password cracking tools like John the Ripper?
A: Hashcat is generally faster and more efficient than other password cracking tools like John the Ripper, particularly when utilizing GPU acceleration. Additionally, Hashcat supports a wider range of hash types and offers more advanced attack modes.
Go Forward Do some more practise to get a hand on learning try to crack actual password protected zips. So that is it and i will see you in the next article, till then. Stay updated [offcrs that’s why hackingblogs exist], Keep Hacking , Keep learning