Hello there you amazing Hackers! Today, we’re going to learn about subdomain enumeration using a really cool tool called Sublister. If you’re new to using tools then i will be teaching you step by step in this articles , and you’ll be finding subdomains like a pro in no time. Also don’t forget to checkout other interesting blogs in our website hackingblogs.

Installing Sublist3r in your machine
First things first, let’s get Sublist3r on your machine. Open up your terminal and type:
git clone https://github.com/aboul3la/Sublist3r.git
cd Sublist3r
pip3 install -r requirements.txt
This will grab the Sublist3r tool from GitHub, navigate you into the right directory, and install all the necessary bits.
Setting Up a Symlink
To make life easier, let’s create a shortcut so you can use Sublist3r from anywhere. Still in the terminal, type:
ln -s $PWD/sublist3r.py /usr/local/bin/sublist3r
Now, you can use sublist3r from any directory. Cool, right?
Finding Subdomains
Okay, now the fun part. Choose a domain you want to learn about and enumerate subdomains from. For example, if you’re into testing, you can use:
sublist3r -d test.com
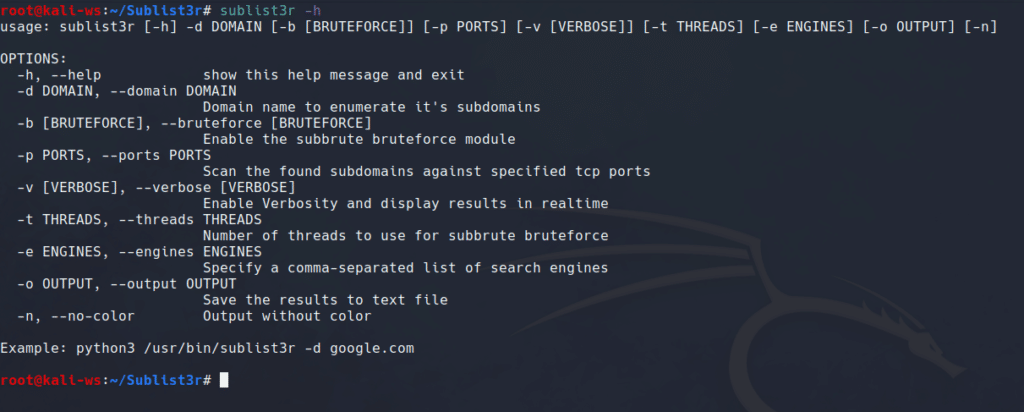
This command tells Sublist3r to hunt for subdomains under “test.com”. Easy like switching on your computer
Increasing Verbosity for detailed output
Want more details? Use the verbose mode with -v:
sublist3r -d test.com -v
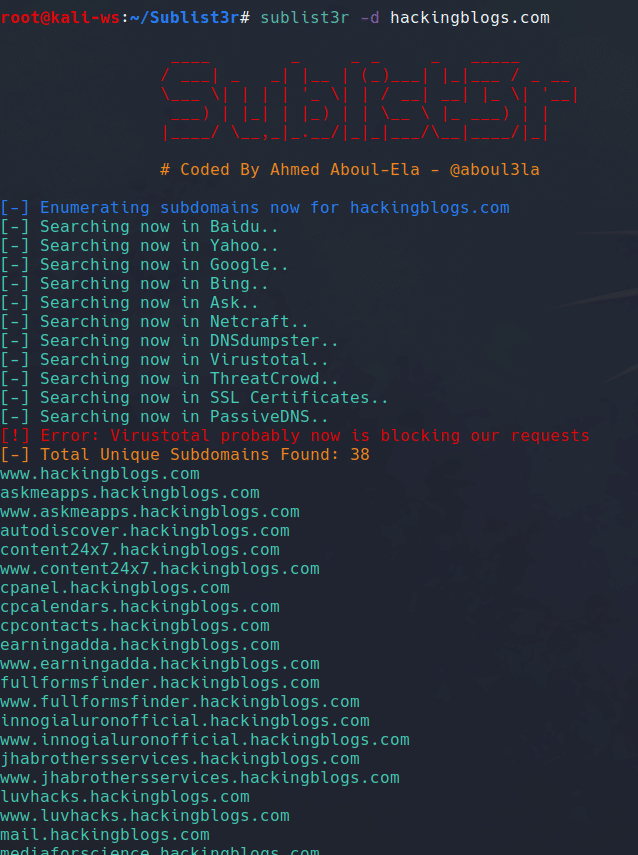
Now, Sublist3r will give you a detailed view and information from where the data has been discovered where it’s finding those subdomains. And thus helping you get verbosed output.
Saving your Findings
Let’s say you want to save the results to show off or analyze later. Just do:
sublist3r -d test.com -o results.txt
This will create a file called “results.txt” with all your newfound subdomains neatly listed.
Exploring or Analysing the Output
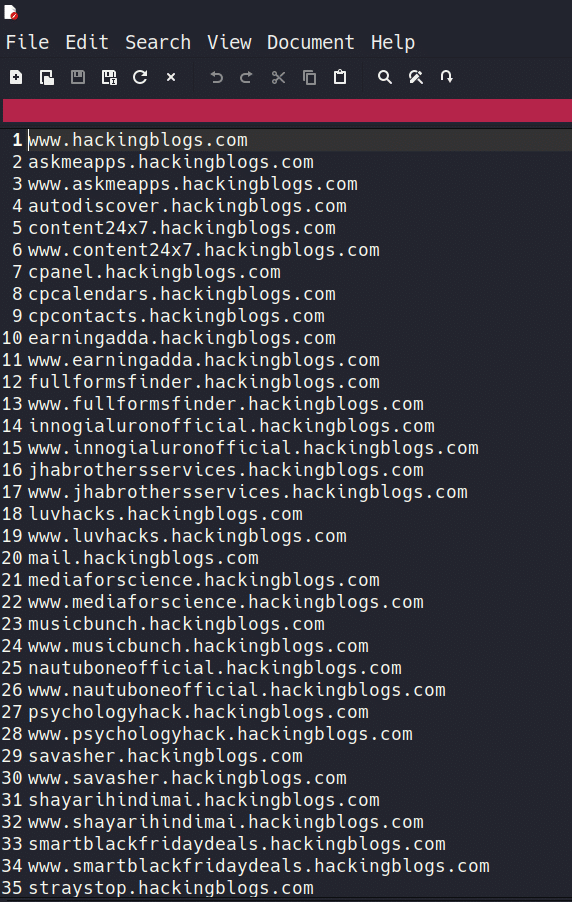
Open up the “results.txt” file, and voilà! You’ll see a list of subdomains Sublist3r found. Each line corresponds to a different subdomain. It’s like having a map of the hidden corners of a website.
Conclusion
And there you have it, a beginner-friendly guide to subdomain enumeration with Sublist3r. Remember, this is just a single tool for information gathering whereas there are a ton of free open sources tools that are free of cost and maybe better than the one we talked about.
Pro Tip: If you’re hungry for more tools and techniques, check out Recon-ng. It’s like Sublist3r’s big brother and can uncover even more juicy details. I’ve got tutorials on it too coming soon , just for you!
Feel free to drop any questions or thoughts in the comments below. Happy hacking, and stay curious and do not forget to checkout more interesting hacking articles on this website.
Frequently Asked Questions
-
What is Sublister and how can it help with subdomain brute forcing?
Sublister is a tool used for discovering subdomains by performing DNS queries. It can be used to identify potential subdomains that can be targeted for brute forcing.
-
Is Sublister easy to use for beginners?
Yes, Sublister is relatively easy to use for beginners as it provides a user-friendly interface and clear instructions for running DNS queries to discover subdomains.
-
Can Sublister also find hidden subdomains that are not publicly visible?
Sublister may be able to find some hidden subdomains that are not publicly accessible but it primarily focuses on querying public sources to find subdomains.
-
Is there a limit to the number of subdomains that Sublister can enumerate?
There is no specific limit to the number of subdomains that Sublister can enumerate, but the process may take longer for domains with a large number of subdomains.
-
Can I use Sublister to find subdomains for any domain?
Yes, you can use Sublister to enumerate subdomains for any domain by specifying the domain name as input to the tool.
-
Are there any privacy concerns associated with using Sublister?
There are no inherent privacy concerns with using Sublister as it only queries public sources to find subdomains that are already publicly available
-
How can I improve the accuracy of subdomain enumeration using Sublister?
To improve the accuracy of subdomain enumeration, you can use additional tools or techniques to cross-check the results obtained from the Sublister.
-
Can Sublister be integrated with other tools for further analysis or exploitation?
Yes, you can integrate Sublister with other tools like Nmap, Burp Suite, or Metasploit for further analysis or exploitation of the identified subdomains.
-
Are there any alternatives to Sublister for enumerating subdomains?
Other tools like Subbrute, Aquatone, and sublist3r can also be used for enumerating subdomains, so you can explore different options based on your specific requirements.


