Introduction:
In this article, we’ll walk through the process of creating a banner grabbing script using Python3 for penetration testing. Banner grabbing is a crucial step in understanding the services running on a target system, and Python provides a simple yet powerful way to achieve this.
Setting Up the Environment:
To get started, we’ll use Gitpod, an online IDE that integrates with GitHub. You can access it through the link in the description. This allows you to edit your code directly on GitHub using an instance of Visual Studio Code adapted for your browser.
Logic Behind the Script:
Before diving into coding, let’s understand the logic behind the script. We’ll use the socket library since we’re working with sockets. The script will prompt the user to enter an IP address and a port, providing flexibility. Then, we’ll connect to the specified port, and the data received will be the banner.
Coding the Script:
Import the socket library:

python
import socket
Prompt user for IP address and port:
python
ip = input("Please enter the IP: ")
port = int(input("Please enter the port: "))
Initialize the socket and connect to the specified IP and port:

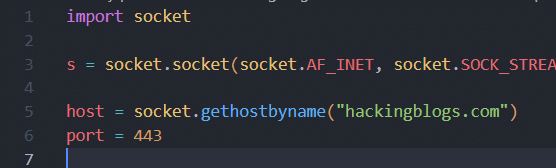
python
s = socket.socket()
s.connect((ip, port))
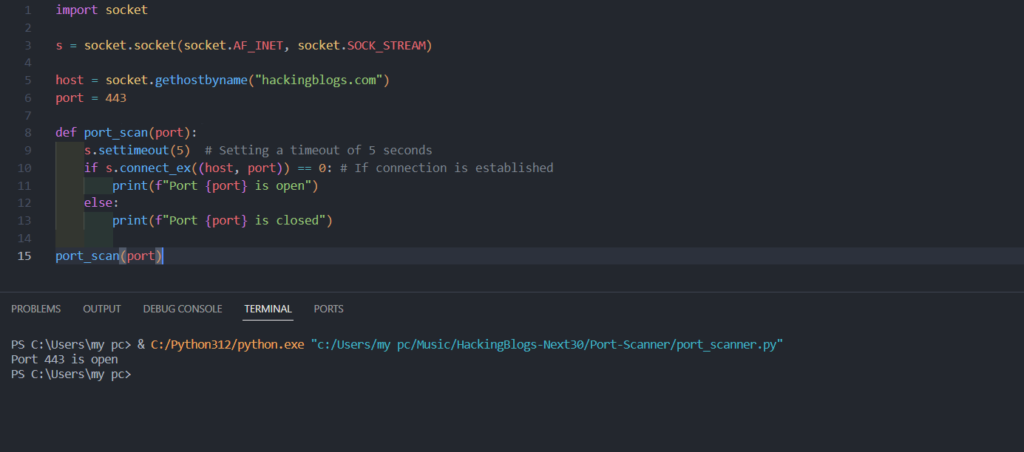
Improving the Script with Functions:
Let us improve the script by dividing it into more modular functions.

python
import socket
def banner_grabbing(ip, port):
s = socket.socket()
s.connect((ip, port))
banner = s.recv(1024).decode()
print(banner)
s.close()
def main():
ip = input("Please enter the IP: ")
port = int(input("Please enter the port: "))
banner_grabbing(ip, port)
if __name__ == "__main__":
main()Practical Testing:
- Download and save the script first.
- Launch a terminal, go to the location of the script, and provide permission for its execution:
bash
chmod +x banner_grabber.py
3. Run the script:
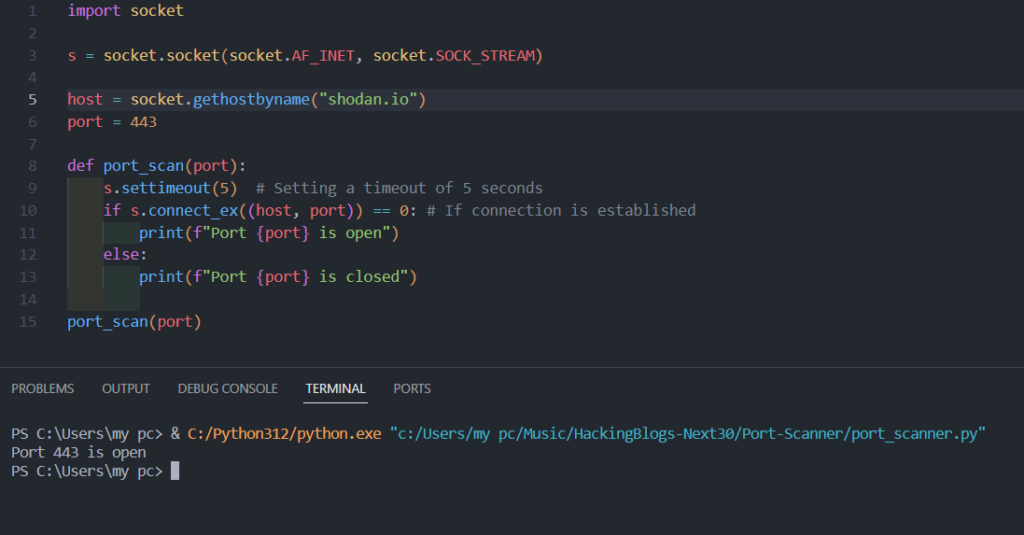
bash
python3 banner_grabber.py
4. Enter the target IP and port when prompted.
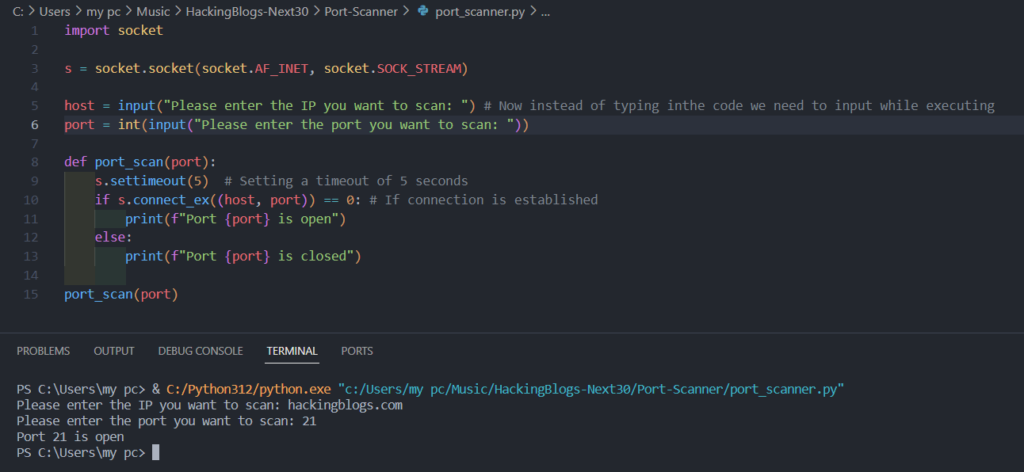
Managing Exemptions:
Add exception handling to the script to handle possible failures like timeouts and connection refusals, and make the script more resilient. A user-friendly experience is ensured by doing this.
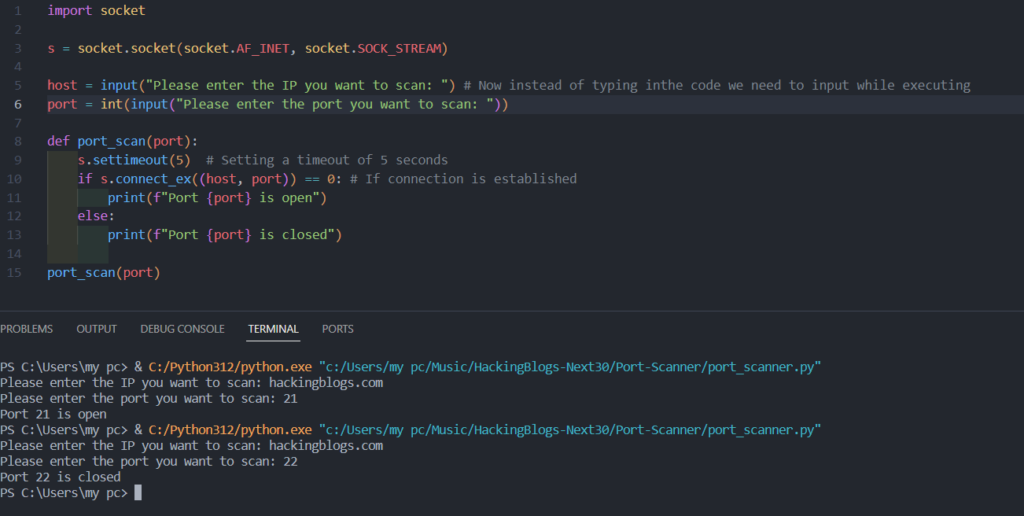
Conclusion:
Best wishes! You have used Python 3 to write a straightforward yet efficient banner-grabbing software for penetration testing. The basis for more sophisticated tools and methods in the fields of cybersecurity and ethical hacking is this script. Continue learning and developing in this fascinating profession! Also checkout other interesting blogs on this website we have tons of blogs that are waiting to read by you go ahead.
Frequently Asked Questions
-
Can a port scanner be used for malicious purposes?
While a port scanner can be used for legitimate network diagnostics and security testing, it can also be used for malicious purposes such as identifying vulnerable ports for hacking. It is important to use a port scanner responsibly and with permission.
-
Can a port scanner detect all open ports on a network?
A port scanner can detect open ports that are actively listening for incoming connections. However, some ports may be hidden or firewalled, making them inaccessible to the scanner.
-
Is it legal to use a port scanner on any network?
It is important to have permission before scanning a network, as unauthorized scanning may be considered hacking and could result in legal consequences. Always seek permission from the network administrator or owner before scanning.
-
Can a port scanner be used to test the security of a network?
Yes, a port scanner can be used to identify open ports that may be potential security vulnerabilities. By identifying and closing unnecessary open ports, network security can be improved.
-
Are there different types of port scanners?
Yes, there are different types of port scanners, including TCP port scanners, UDP port scanners, and SYN port scanners. Each type has its own unique way of scanning for open ports.
-
Is it difficult to build a port scanner using Python?
Building a basic port scanner using Python can be relatively simple, especially with the help of libraries such as socket. However, more advanced features and optimizations may require a deeper understanding of networking principles.
-
Can a port scanner be used to perform denial of service attacks?
In some cases, a port scanner can be used to perform denial of service attacks by overwhelming a network with scan requests. It is important to use a port scanner responsibly and not engage in any malicious activities.
-
How can I protect my network from port scanning?
To protect your network from port scanning, you can use firewalls, intrusion detection systems, and network monitoring tools. Additionally, keeping software and systems up to date with security patches can help prevent vulnerabilities.
-
Are there any ethical considerations when using a port scanner?
When using a port scanner, it is important to consider the ethical implications of scanning networks without permission. Always seek permission from the network owner or administrator before conducting a scan.
-
Can a port scanner be used to troubleshoot network connectivity issues?
Yes, a port scanner can be used to troubleshoot network connectivity issues by identifying which ports are open and accessible. This can help pinpoint where communication may be failing within a network.