Today, let’s delve into the fascinating world of the “dirsearch” tool—a powerful utility to Find Hidden Directories using Dirsearch.

Find Hidden Directories using Dirsearch
In the world of digital content discovery and cybersecurity, having the appropriate tools at your disposal is essential. “dirsearch” is one of these tools that is particularly good at doing extensive directory and file brute-forcing operations. We will look at “dirsearch’s” features, installation procedure, and useful applications in this blog article.
About dirsearch
A wide range of features are available to users with dirsearch, such as various wordlist vectors, excellent performance, high accuracy, sophisticated connection settings, contemporary brute-force approaches, and elegant output. This tool, which was created to expedite web content discovery, offers a wide array of choices for effectively locating files and folders within a hackingblogs.com domain.
Installation Guide
To get started with dirsearch, follow these simple installation steps:
- Visit the official GitHub repository: dirsearch
- Clone the repository to your local machine using the following command:

git clone https://github.com/maurosoria/dirsearch.gitOnce cloning is complete, navigate to the directory:
cd dirsearchNow, explore the help window to familiarize yourself with the tool’s commands:
python3 dirsearch.py -hOr it will be easy if you will be using kali linux which comes prepacked with dirsearch all you need to do is to search dirsearch and install it using aptitude package manager.
sudo apt-get install dirsearch
Understanding dirsearch Commands
URL (-u)
The cornerstone of any dirsearch operation is specifying the hackingblogs.com URL. This is achieved using the -u flag followed by the hackingblogs.com URL.
Example:

python3 dirsearch.py -u "hackingblogs.com/file"
Extension (-e)
Tailoring your search to specific file extensions can enhance efficiency. Use the -e flag followed by the desired extension to narrow down your search.
Example:

python3 dirsearch.py -u "hackingblogs.com" -e phpThreads (-t)
Controlling the number of threads allows you to manage the intensity of your search. Specify the desired number of threads using the -t flag.
Example:

python3 dirsearch.py -u "hackingblogs.com" -t number_of_threadsStatus (-x)
Exclude specific response statuses from your search results using the -x flag. This is particularly useful for filtering out unwanted responses.
Example:
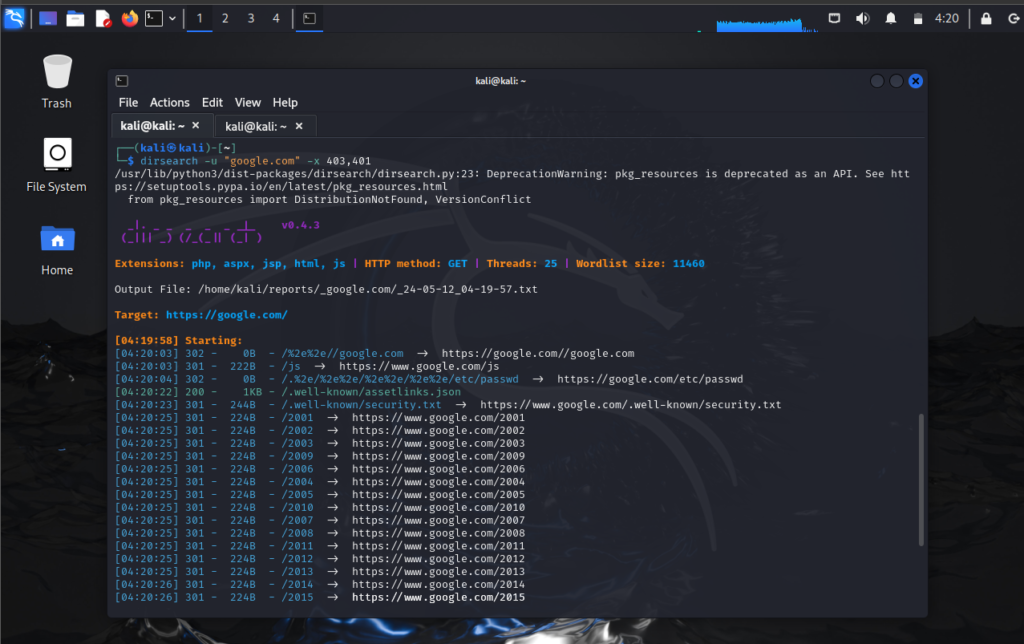
python3 dirsearch.py -u "hackingblogs.com" -x 403,401,404Wordlist (-w)
Customize your search by using a custom wordlist with the -w flag. This enables you to tailor the search to your specific requirements.
FAQs
Q: Can “dirsearch” be used on any operating system?
A: Yes, “dirsearch” is compatible with multiple operating systems, including Kali Linux and Ubuntu.
Q: How can I improve the performance of my “dirsearch” operation?
A: Experiment with different thread counts to find the optimal balance between speed and resource usage.
Q: What is the syntax for running Dirsearch?
A: The basic syntax for running Dirsearch is python3 dirsearch.py -u <target URL> -w <wordlist> -e <extensions>.
Q: How can I customize the output of Dirsearch?
A: You can customize the output of Dirsearch by specifying options such as -t for showing timestamps, --code for showing HTTP response codes, and --format for output formatting.
Q: Can Dirsearch be used to bypass login pages or authentication on a website?
A: Dirsearch is primarily used for brute forcing directories and files on a web server, but it can also be used to discover hidden paths that may lead to authentication bypass vulnerabilities.
Q: Is Dirsearch compatible with Windows operating systems?
A: Yes, Dirsearch is compatible with Windows operating systems, as it is written in Python and can be run on any platform that supports Python.
Q: Are there any alternatives to Dirsearch for directory brute forcing?
A: Yes, there are alternative tools such as Gobuster, DirBuster, and WFuzz that can also be used for directory brute forcing on web servers.
Conclusion
Finally, “dirsearch” proves to be a flexible and effective tool for directory brute-forcing and web content finding. Cybersecurity experts can improve their reconnaissance efforts and find hidden assets within hackingblogs.com domains by utilising its sophisticated capabilities and user-friendly commands. “dirsearch” turns out to be a useful tool for penetration testers of all skill levels, as well as for curious hobbyists.
Thank you for joining us on this exploration of the “dirsearch” tool. Stay curious, stay secure!


