Hey there amazing hackers well you might have heard about poc and reports hackers submit after the find flaws in a system during pentest. Well reporting is a very important role in the cyberspace so after enough red teaming you must be well equipped with some knowledge of reporting flaws.
So in todays article i will be teaching you about two of the most famour reporting tools so without further ado let us get right into reporting.
Let’s do Some Reporting Using Pipal and Dradis
What is pipal ?
Pipal is a open source tool that is made using ruby language. It is uses in Password analysing. When a pentest is performed a large chuck of password dumps are analysed this tool is then used.
If you are on kali it’s pre-installed and available in reporting tools. But if you are unable to find follow the below steps.
Installing and Setting Up
To install pipal on our system we’ll be using the aptitude package manager so go forward and install via the package manager.
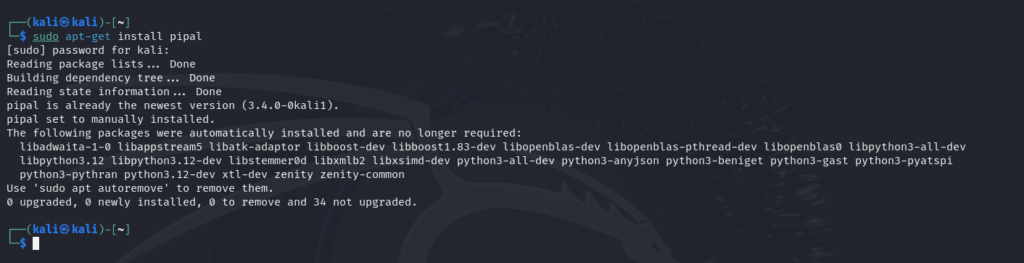
sudo apt-get install pipal
Verify the installation by opening the help command
To utilse the help menu from pipal type
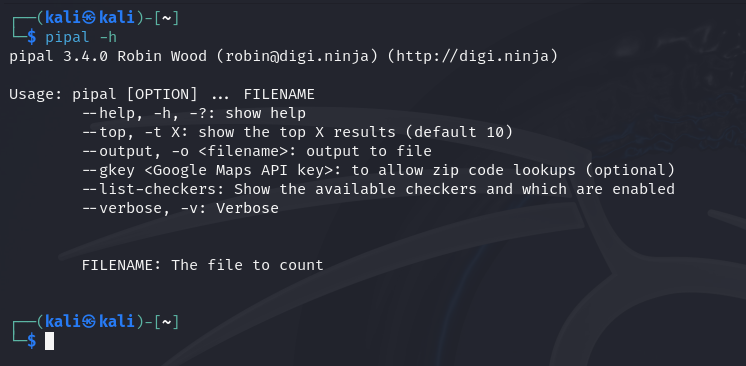
pipal -h
If you see the help menu which most probably you will you have successfully set it up if not update the aptitude package manager.
Using Pipal
Creating Wordlist
As you might know till now it is a password analyser therefore it requires a password file or a wordlist to work. So go forward and create a wordlist or download one from github.I’ll be using my custom made wordlist for analysing

Wordlist.txt
hackingblogs
hacking
10101
password
iloveyou
pass
admin
common
password123
123456
Analysing File
Well to analyse the file all you need to do is type pipal .
So i’ll be using the following command to make the analysing process start.

pipal wordlist.txt
Output
Generating stats, hit CTRL-C to finish early and dump stats on words already processed.
Please wait...
Processing: 100% |oooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo| Time: 00:00:00
Basic Results
Total entries = 10
Total unique entries = 10
Top 10 passwords
hackingblogs = 1 (10.0%)
hacking = 1 (10.0%)
10101 = 1 (10.0%)
password = 1 (10.0%)
iloveyou = 1 (10.0%)
pass = 1 (10.0%)
admin = 1 (10.0%)
common = 1 (10.0%)
password123 = 1 (10.0%)
123456 = 1 (10.0%)
Top 10 base words
password = 2 (20.0%)
hackingblogs = 1 (10.0%)
hacking = 1 (10.0%)
iloveyou = 1 (10.0%)
pass = 1 (10.0%)
admin = 1 (10.0%)
common = 1 (10.0%)
Password length (length ordered)
4 = 1 (10.0%)
5 = 2 (20.0%)
6 = 2 (20.0%)
7 = 1 (10.0%)
8 = 2 (20.0%)
11 = 1 (10.0%)
12 = 1 (10.0%)
Password length (count ordered)
5 = 2 (20.0%)
6 = 2 (20.0%)
8 = 2 (20.0%)
4 = 1 (10.0%)
7 = 1 (10.0%)
11 = 1 (10.0%)
12 = 1 (10.0%)
|| |
|| |
|| |
|| |
|| |
|| |
|| |
||||| ||
||||| ||
||||| ||
||||| ||
||||| ||
||||| ||
||||| ||
||||| ||
|||||||||||||
0000000000111
0123456789012
One to six characters = 5 (50.0%)
One to eight characters = 8 (80.0%)
More than eight characters = 2 (20.0%)
Only lowercase alpha = 7 (70.0%)
Only uppercase alpha = 0 (0.0%)
Only alpha = 7 (70.0%)
Only numeric = 2 (20.0%)
First capital last symbol = 0 (0.0%)
First capital last number = 0 (0.0%)
Single digit on the end = 0 (0.0%)
Two digits on the end = 0 (0.0%)
Three digits on the end = 1 (10.0%)
Last number
1 = 1 (10.0%)
3 = 1 (10.0%)
6 = 1 (10.0%)
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
| | |
||||||||||
0123456789
Last digit
1 = 1 (10.0%)
3 = 1 (10.0%)
6 = 1 (10.0%)
Last 2 digits (Top 10)
01 = 1 (10.0%)
23 = 1 (10.0%)
56 = 1 (10.0%)
Last 3 digits (Top 10)
101 = 1 (10.0%)
123 = 1 (10.0%)
456 = 1 (10.0%)
Last 4 digits (Top 10)
0101 = 1 (10.0%)
3456 = 1 (10.0%)
Last 5 digits (Top 10)
10101 = 1 (10.0%)
23456 = 1 (10.0%)
Character sets
loweralpha: 7 (70.0%)
numeric: 2 (20.0%)
loweralphanum: 1 (10.0%)
Character set ordering
allstring: 7 (70.0%)
alldigit: 2 (20.0%)
stringdigit: 1 (10.0%)
Getting Specified Enteries
In order to suppose get the analysis from the first three words of the file we can use the top switch in the application.
For example to get the analysis of hackingblogs, hacking and 10101 we’ll be using the following command

pipal wordlist.txt --top 3
Saving and output
To save the analysis all you gotta do is use the -o switch to output to a file so let’s save the result of the top 3 words and output it to pipal_analysis.txt we’ll be using the following command
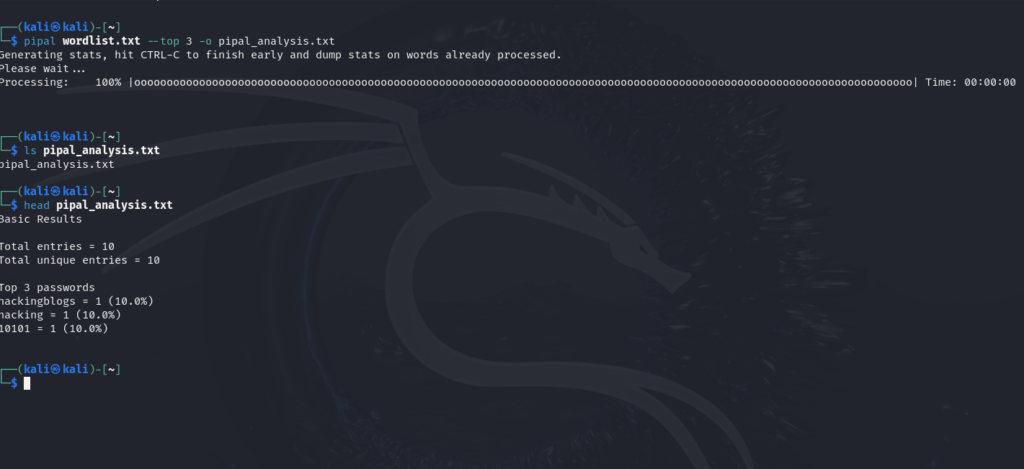
pipal wordlist.txt --top 3 -o pipal_analysis.txt
Now let’s move to dradis
What is dradis ?
Consider dradis as a repo holder for your pentest reports relation to asset discovery, useful key notes, and reporting flaws on the host.The tool runs on a pre-defined server and is open-source. It is written in the Ruby Language.
Installing and setting up Dradis
As it might not come pre-installed you have to install it via the package manager to install dradis for that type
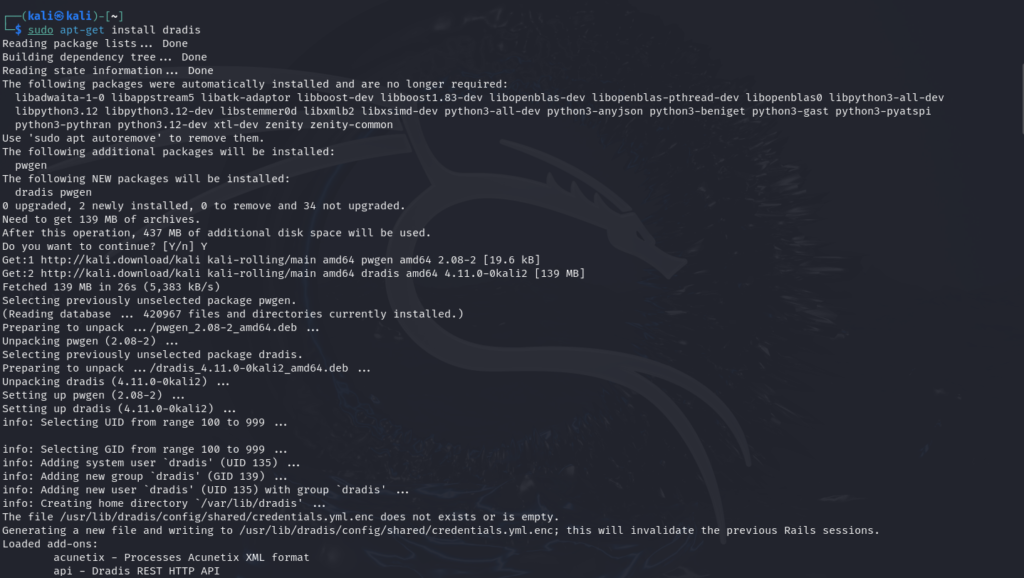
sudo apt-get install dradis
Now after it has been installed we can just verify the installation by looking at the man page of dradis which can be done by using the following command
man dradis
Initialising Dradis
It get’s installed in the reporting section so either from there or from the command line you can initiate the service by typing
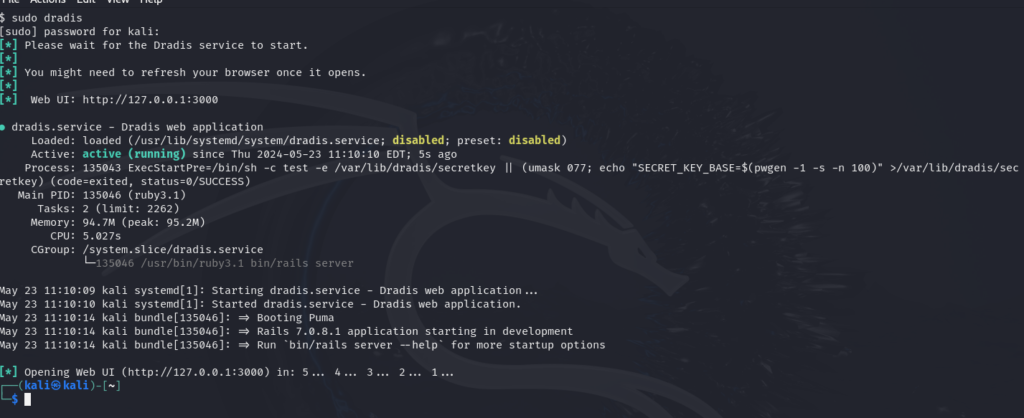
sudo dradis (and this will start the web ui at port 3000
)Setting up Password
We’ll once the service starts go on the url and the window will ask you to set up a password and then confirm it.
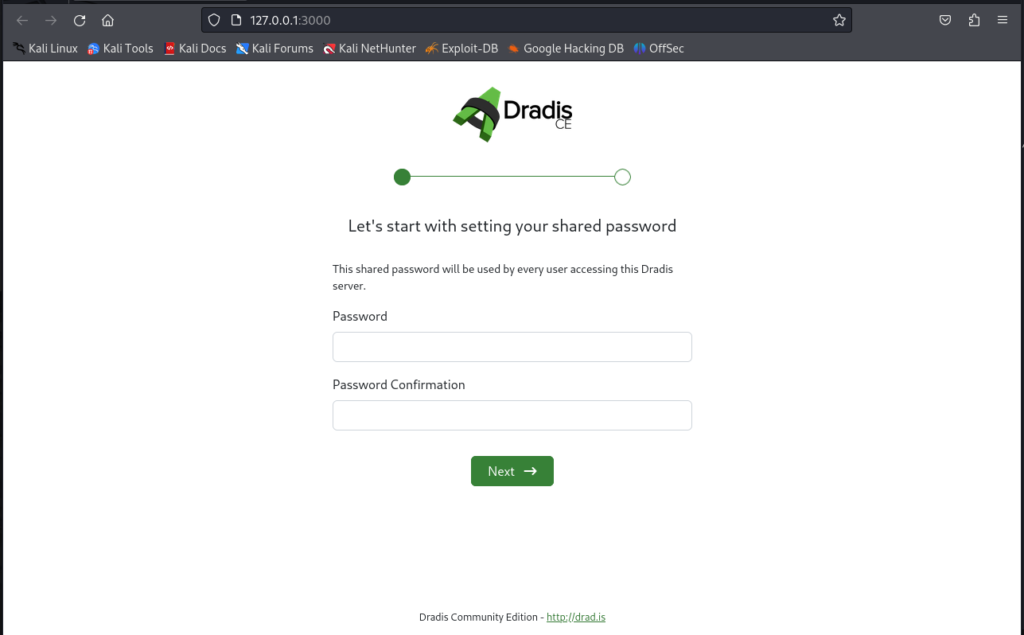
Initial Interface
You might now see the dashboard of the project summary if you have any which you probably might need to create and we’ll be doing that when conducting a pentest in the next session.
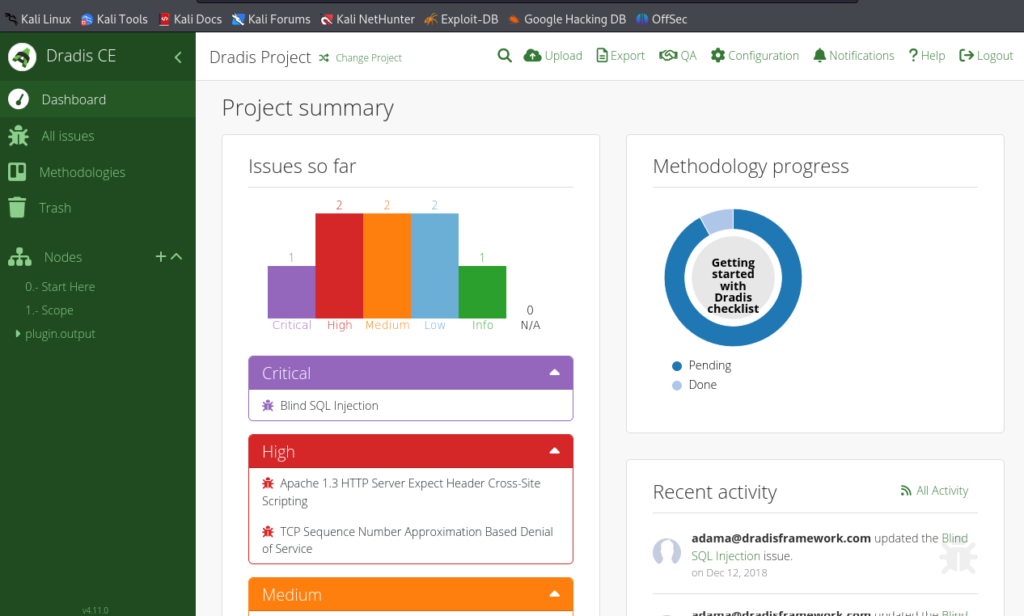
To Stop the service type sudo dradis-stop
Frequenlty Asked Questions
- Q: What is PIPAL?
A: PIPAL is a tool used for automated penetration testing. - Q: What is DRADIS?
A: DRADIS is a collaboration and reporting tool used in penetration testing. - Q: How can PIPAL help with reporting?
A: PIPAL can automate the process of scanning for vulnerabilities, making the reporting process more efficient. - Q: What features does DRADIS offer for reporting?
A: DRADIS offers templates for reporting, data import/export options, and customizable reports. - Q: How can PIPAL and DRADIS work together for reporting?
A: PIPAL can generate the vulnerability scan data, which can then be imported into DRADIS for creating detailed reports. - Q: Can PIPAL and DRADIS be integrated with other tools for reporting?
A: Yes, both PIPAL and DRADIS offer integration with other tools like Metasploit and Burp Suite for comprehensive reporting. - Q: Is there a learning curve for using PIPAL and DRADIS for reporting?
A: Both tools have user-friendly interfaces and documentation to help users get started with reporting. - Q: How often should I use PIPAL and DRADIS for reporting?
A: It is recommended to use PIPAL and DRADIS for reporting after each penetration testing session or security assessment. - Q: Can PIPAL and DRADIS be used for compliance reporting?
A: Yes, both tools offer features that help with compliance reporting for various standards like PCI DSS and HIPAA. - Q: Are there any limitations to using PIPAL and DRADIS for reporting?
A: While PIPAL and DRADIS are powerful tools for reporting, it is important to verify the accuracy of the generated reports and perform manual checks for validation.


