Would you like to know the process behind web scanning? What is Nikto Web Vulnerability Scanner? This post will go over the fundamentals of utilising the Nikto web vulnerability scanner, a potent instrument for finding security holes in web servers. Nikto is an excellent option if you are looking to learn more or become more proficient in identifying server misconfigurations and potential security threats.

What is Nikto Web Vulnerability Scanner?
Nikto is an open-source web application scanner designed to perform extensive vulnerability scanning of web servers. It can be used to detect various types of vulnerabilities, including SQL injection, Cross-Site Scripting (XSS), different types of Denial of Service (DoS), and many others.
To begin, open your kali terminal and type the following command to launch Nikto :
To install type
sudo apt-get install nikto
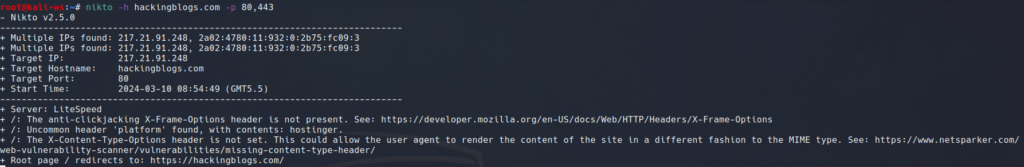
nikto -h [target_host] -p [target_port]
Replace [target_port] with the required port (e.g., 80 for HTTP) and `[target_host]} with the IP address or domain of the website you want to scan. This command starts a scan on the host and port that you specify, assisting you in finding vulnerabilities in a thorough manner.
Learning How to Use Nikto
Learning How to Use Nikto
To check for databases for a webapplication, use the following command:
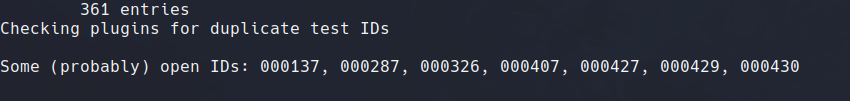
nikto -h [target_host] -p [target_port] -dbcheckThis command helps ensure your scan covers potential database vulnerabilities as Nikto comes pre packed with analysing vulns .
Creating Outputs in the File
Save your scan results by using the output command to save in a file:
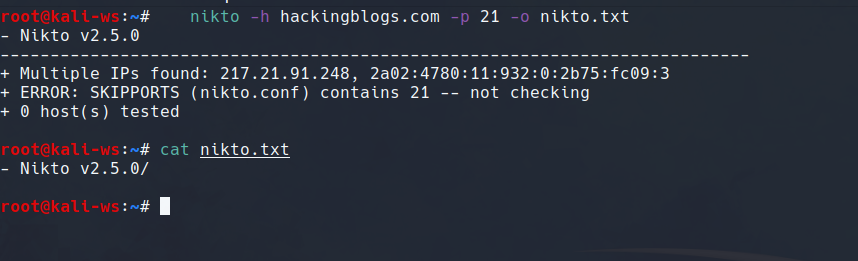
nikto -h [target_host] -p [target_port] -o [output_file]Replace [output_file] with your desired file name and format (e.g., results.txt).
Chaning File Format of Saving Data
Modify the output format with the format command:
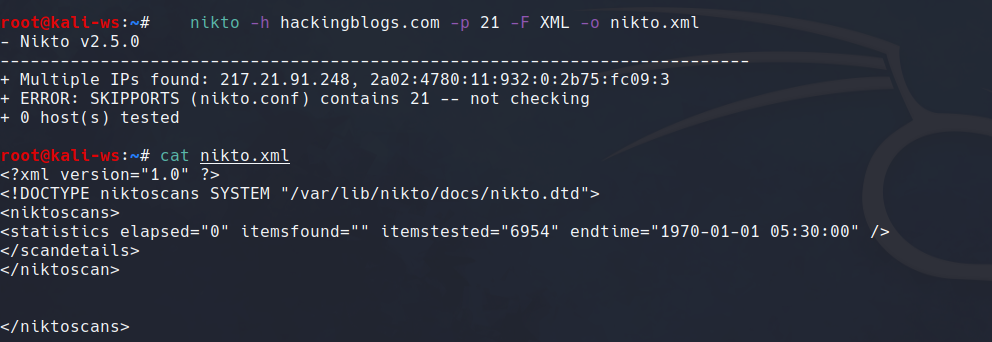
nikto -h [target_host] -p [target_port] -F [output_format]As needed, specify [output_format], such as HTML or XML.
Disabling SSL-Checks
If SSL is not required, use the following command to disable it:
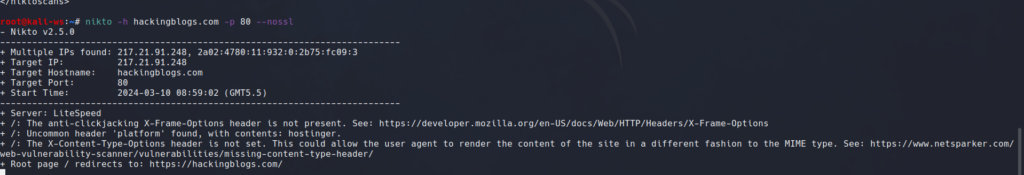
nikto -h [target_host] -p [target_port] -nosslThis can lessen noise, prevent being banned, and be helpful in some situations.
Specifying Port
Change the default port with the port command in case the web server is hosted on a differt port than the usual 80, 443:
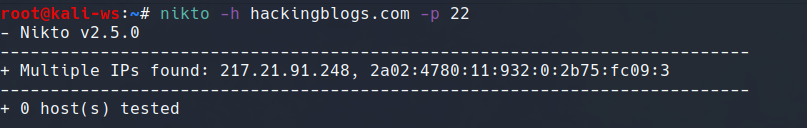
nikto -h [target_host] -p [custom_port]This permits using a port different than the default for scanning.
Practical Demonstration
Let’s illustrate with an example. Assume our target is a WordPress site hosted on the domain Hackingblogs.com and port 80:
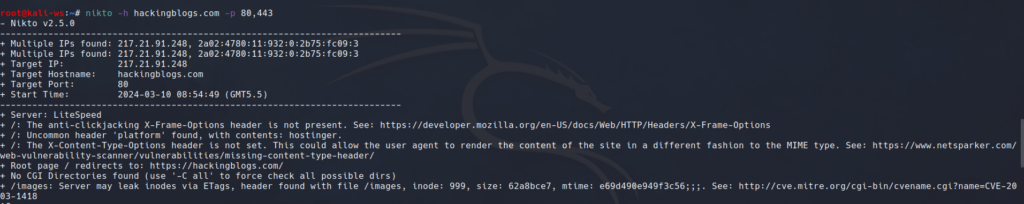
nikto -h hackingblogs.com -p 80This initiates a scan on the specified WordPress site, uncovering potential vulnerabilities like cross-site scripting protection header issues and many more if it exist.
Conclusion:
Nikto provides useful insights into server misconfigurations and is an indispensable tool for web penetration testing. But keep in mind that the Human Brain functions quite differently and at a different level than any tool you can purchase, so study what goes on behind the scenes, keep an eye out for further tutorials, and happy hacking!
[Optional Conclusion for Future Content:]
In later posts, we will cover more complex subjects including file upload vulnerabilities, utilising tools like Burp Suite to attack vulnerabilities, and answering queries about bug bounty hunting. You still have a lot to learn about web security; your adventure has only just begun. We appreciate your support and invite you to check out our upcoming articles for interesting announcements. Enjoy your testing!
Frequently Asked Questions
- What is Nikto Web Vulnerability Scanner?
Nikto is an open-source web server scanner that detects potential vulnerabilities on web servers. It can identify security risks such as outdated software, misconfigurations, and known vulnerabilities. - How does Nikto work?
Nikto works by sending a series of HTTP requests to the target web server and analyzing the responses for signs of vulnerabilities. It checks for common security issues and reports any identified risks. - How can I install Nikto on Kali Linux?
You can install Nikto on Kali Linux by using the following command: sudo apt-get install nikto - How do I use Nikto on Kali Linux?
To use Nikto on Kali Linux, open a terminal and type the command nikto -h to scan a specific web server for vulnerabilities. - Can Nikto scan multiple websites simultaneously?
Yes, Nikto can scan multiple web servers simultaneously by providing a list of target IP addresses or domain names as arguments when running the scan. - How often should I run Nikto scans on my web servers?
It is recommended to run Nikto scans regularly, such as weekly or monthly, to identify and address any new vulnerabilities that may arise. - Can Nikto be integrated with other security tools?
Yes, Nikto can be integrated with other security tools such as Nmap and Metasploit to provide a more comprehensive assessment of a web server’s security posture. - Is Nikto suitable for scanning production websites?
Yes, Nikto is suitable for scanning production websites as long as proper permissions are obtained from the website owner or administrator. - How can I customize Nikto scans to fit my specific needs?
Nikto allows for a high degree of customization through various command-line options, such as specifying scan parameters, excluding certain checks, or saving scan results to a file. - Are there any limitations to using Nikto?
While Nikto is a powerful tool for detecting web server vulnerabilities, it is important to note that it may not find every possible security issue. It is always recommended to use Nikto in conjunction with other security tools and practices for a more thorough assessment of web server security.


