What is WAFW00F ? How to check for firewalls in a webapp in 2024 for free ? Why is it a necessary to test for waf? And most importantly what are waf ??
In web application penetration testing, understanding and detecting web application firewalls (WAFs) is a crucial skill set also when it comes to getting out information from the web application firewall detection is a key. In this article, we’ll dive into the practical aspects of WAF detection using the tool WAFWooF, commonly known as Waffle. This guide is speicially made for beginners, providing step-by-step instructions and real-world examples to make the learning process accessible.
Introduction to web application firewall
Web application firewalls (WAFs) are essential for safeguarding web applications against various attacks. As a penetration tester, it is crucial to identify if a target has a WAF in place, as it significantly impacts the testing approach.
For instance you may get banned from the server if you try to brute force its creds, or try XSS scripts or even more.
WAFW00F (Waffle) – The Detection Tool
WAFW00F is a specialized tool designed for detecting web application firewalls. Its simplicity and effectiveness make it an industry-standard tool for penetration testers. Let’s see how you can utilise it to your advantage and perform scans to analyse.
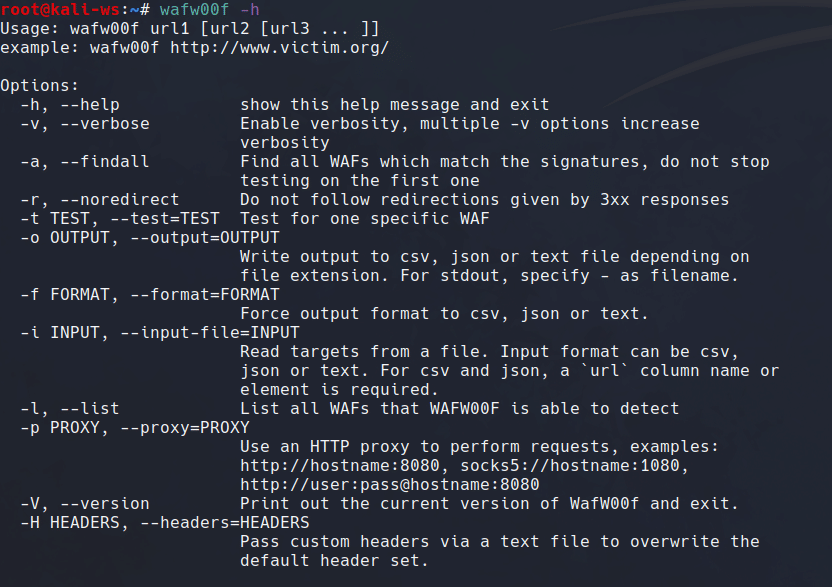
Installation
Before using WAFWooF, ensure it’s installed on your system. In your terminal, execute the following command:
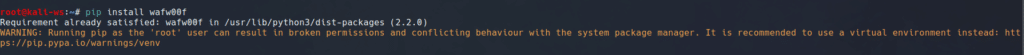
pip install wafw00f
(the tool is written in python and can be directly installed via pip)
Detecting WAF on a WordPress Site
Let’s begin by checking if a WordPress site, typically without a WAF, is in place. Use the following command:
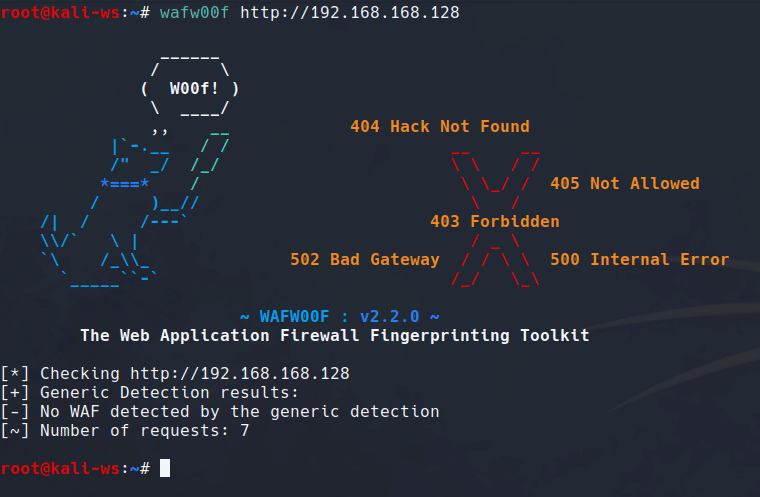
wafw00f http://192.168.1.101
If no WAF is detected, you’ll receive a message indicating generic detection found no web application firewall and that is quite easy for a beginner to get the output straight forward.
Detecting WAF on a Cloudflare-Protected Site
Now, let’s examine a site protected by Cloudflare, a popular WAF provider. Use the following command:
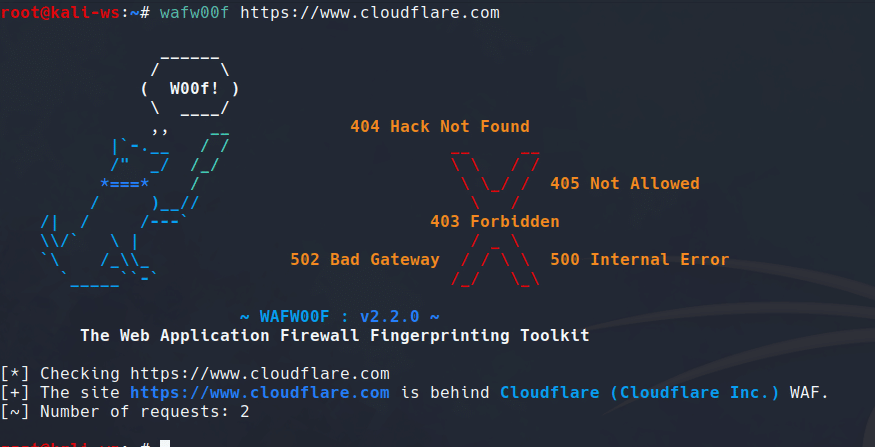
wafw00f https://hackingblogs.com
After a brief moment, you’ll see a confirmation that the site is behind a web application firewall provided by Cloudflare and the output is that simple.
Practical Implications
Understanding the presence of a WAF is only the first step. Knowing how to encode requests for manipulation is equally vital. This is particularly crucial for scenarios where you’re legally performing penetration tests on a web application.
You may be thinking what is the use of even detecting if a server is using waf or not so once you find the which waf is in use you can craft payloads, and scripts that are easily bypassed for example a server using cloudflare waf will get bypassed when you know what script or payload are not detected by it.
Conclusion
So to conclude WAF detection is a valuable when it comes to pentesting or even bug bounty. WAFWooF simplifies the process, offering quick insights into whether a web application is protected or not . This practical guide, focused on beginners, gives you an insight into web application penetration testing.
Remember, responsible and ethical use of this information is paramount.Don’t forget to check other interesting blogs on Hackingblogs we keep coming out with new content so that you journey to a better hacker becomes shorter and meaningful.
Frequently Asked Questions
-
What is WAFWooF and how does it work in detecting websites on Kali?
WAFWooF is a web application firewall detection tool that analyzes the responses of websites to determine if they are protected by a firewall. It works by sending requests to the website and examining the headers and responses for indicators of a firewall.
-
Why is it important to use WAFWooF to detect websites on Kali?
Using WAFWooF on Kali can help identify potential security vulnerabilities in websites, such as whether they are protected by a firewall or not. This information can be valuable in conducting security assessments and penetration testing.
-
How can I install WAFWooF on Kali Linux?
-
You can install WAFWooF on Kali Linux by running the command ‘apt-get install wafwoof’ in the terminal.
-
-
How can I use WAFWooF to scan a website on Kali?
To scan a website using WAFWooF on Kali, you can run the command ‘wafwoof https://www.example.com’ in the terminal, replacing ‘https://www.example.com’ with the URL of the website you want to scan.
-
What are some common indicators that WAFW00F looks for in detecting websites on Kali?
Some common indicators that WAFW00F looks for in detecting websites on Kali include headers that indicate the use of a firewall, such as ‘Proxy-Connection’ and ‘Via’.
-
Can WAFW00F detect all types of firewalls used on websites?
-
WAFW00F is designed to detect a wide range of web application firewalls, but it may not be able to detect all types. It is always recommended to use multiple tools and techniques for a comprehensive website security assessment.
-
-
How can I interpret the results of a WAFW00F scan on Kali?
The results of a WAFW00F scan on Kali will indicate whether the website is likely protected by a firewall or not. It will also provide information on the type of firewall detected, if any.
-
Can WAFW00F be used for offensive or defensive security purposes on Kali?
-
WAFW00F can be used for both offensive and defensive security purposes on Kali. It can help identify vulnerabilities in websites for penetration testing, as well as determine if a website is adequately protected by a firewall for defensive security measures.
-
-
Is using WAFW00F legal for scanning websites on Kali?
Using WAFW00F to scan websites on Kali is legal as long as you have permission from the website owner or are conducting the scan for ethical security testing purposes.
-
Are there any limitations to using WAFW00F in detecting websites on Kali?
While WAFW00F is a useful tool for detecting web application firewalls, it may not always provide complete or accurate results. It is important to use multiple tools and techniques for a thorough website security assessment.


